Photo Gallery
 |
 |
K2 Security Platform by K2 Cyber Security

Additional Info
| Company | K2 Cyber Security |
| Company size | 10 - 49 employees |
| Website | http://www.k2io.com |
NOMINATION HIGHLIGHTS
Organizations are under constant pressure to deliver applications from development to production as quickly as possible. The prioritizing of speed over security has led to an increase in the number of vulnerabilities found in released code, resulting in costly attacks on web applications.
K2 offers a revolutionary approach to the detection of attacks and vulnerabilities, including the OWASP Top 10. K2’s Security Platform is based on a unique, patent-pending technology called Optimized Control Flow Integrity (OCFI).
OCFI uses a deterministic approach to security; its innovative design approach creates a unique map or DNA for each application, allowing K2’s Security Platform to verify that the function and API calls are operating the way the code was written and intended. Zero day exploits and other vulnerabilities are immediately identified as a deviation to the code’s correct execution. K2’s technology has 8 patents granted/pending.
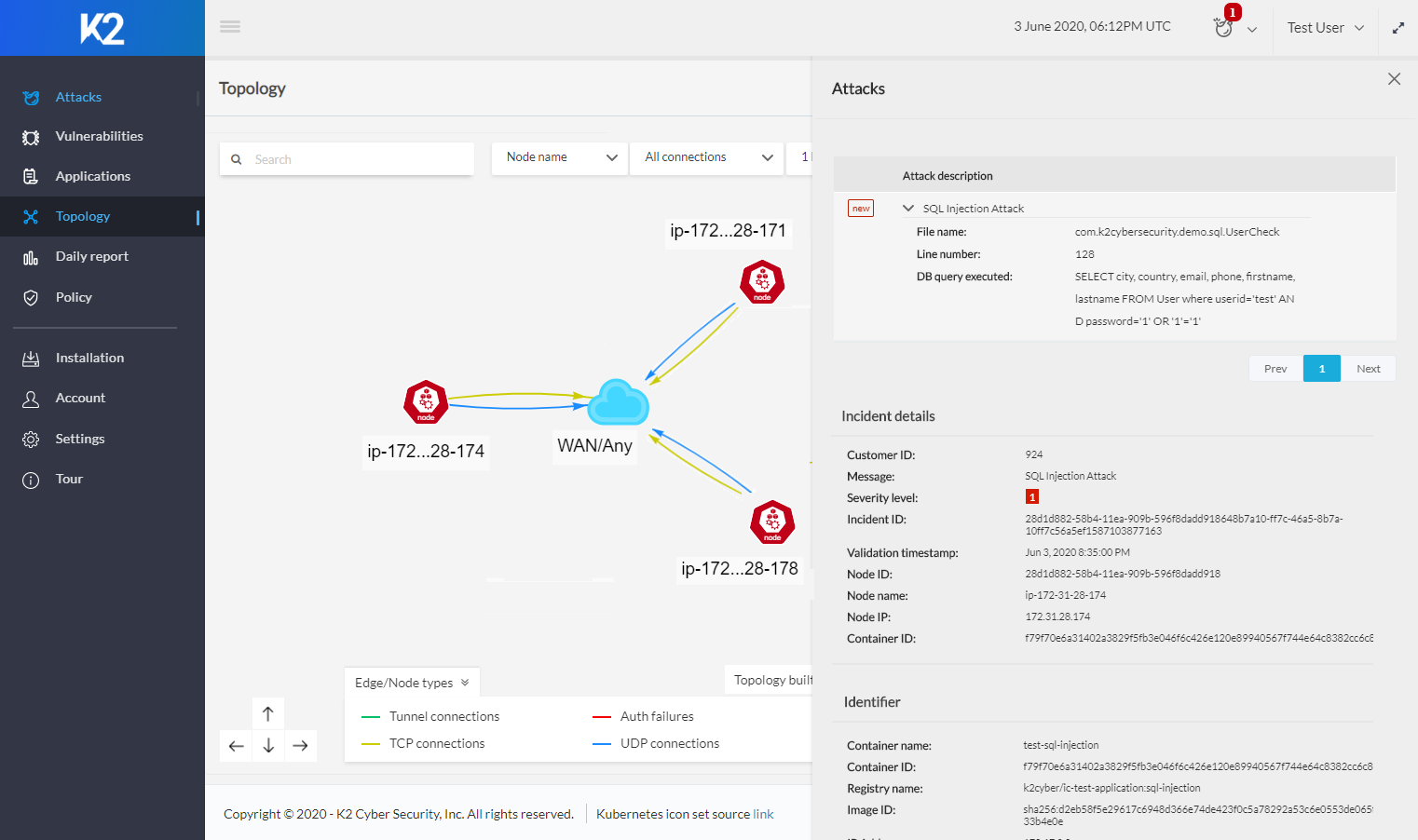
K2’s Security Platform can be used during DAST/penetration testing to improve vulnerability detection and has a second use case, where K2 is deployed on production servers for runtime protection of applications.
Current penetration tools create too many false positives and provide limited information on vulnerabilities, making finding and fixing vulnerabilities time consuming and laborious. When K2 discovers a vulnerability, such as SQL injection, XSS, Remote Code Injection, and others, it provides complete visibility including the exploit payload, the line of code, and the file name that contains the vulnerability. This level of granularity enables developers to start the remediation process quickly. K2 can also be used to locate false positives from DAST testing and to find additional missed vulnerabilities during testing. In recent customer testing, K2 identified 50% more vulnerabilities than with standard testing tools alone.
K2’s Security Platform is easy to install and can be deployed in the cloud, on premise or in hybrid environments.
How we are different
• By focusing on the correct execution of the application itself, and not on prior attacks or behavior, K2 can determine when a vulnerability exists, even when DAST and other testing tools fail to detect a vulnerability.
• K2 provides line of code visibility to the vulnerability, by specifying exact filename and line of code where the discovered vulnerabilities are located, along with the full payload to reproduce the exploit on the vulnerability. With specific vulnerability telemetry, K2’s solution produces minimal false alerts and dramatically eliminates wasted security resources and debugging time
• K2’s Security Platform works in tandem with DAST/pen-test tools to enhance their visibility and point to vulnerabilities more quickly; in recent customer testing, K2 identified 50% more vulnerabilities than in standard testing tools alone

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



