Photo Gallery

|


|
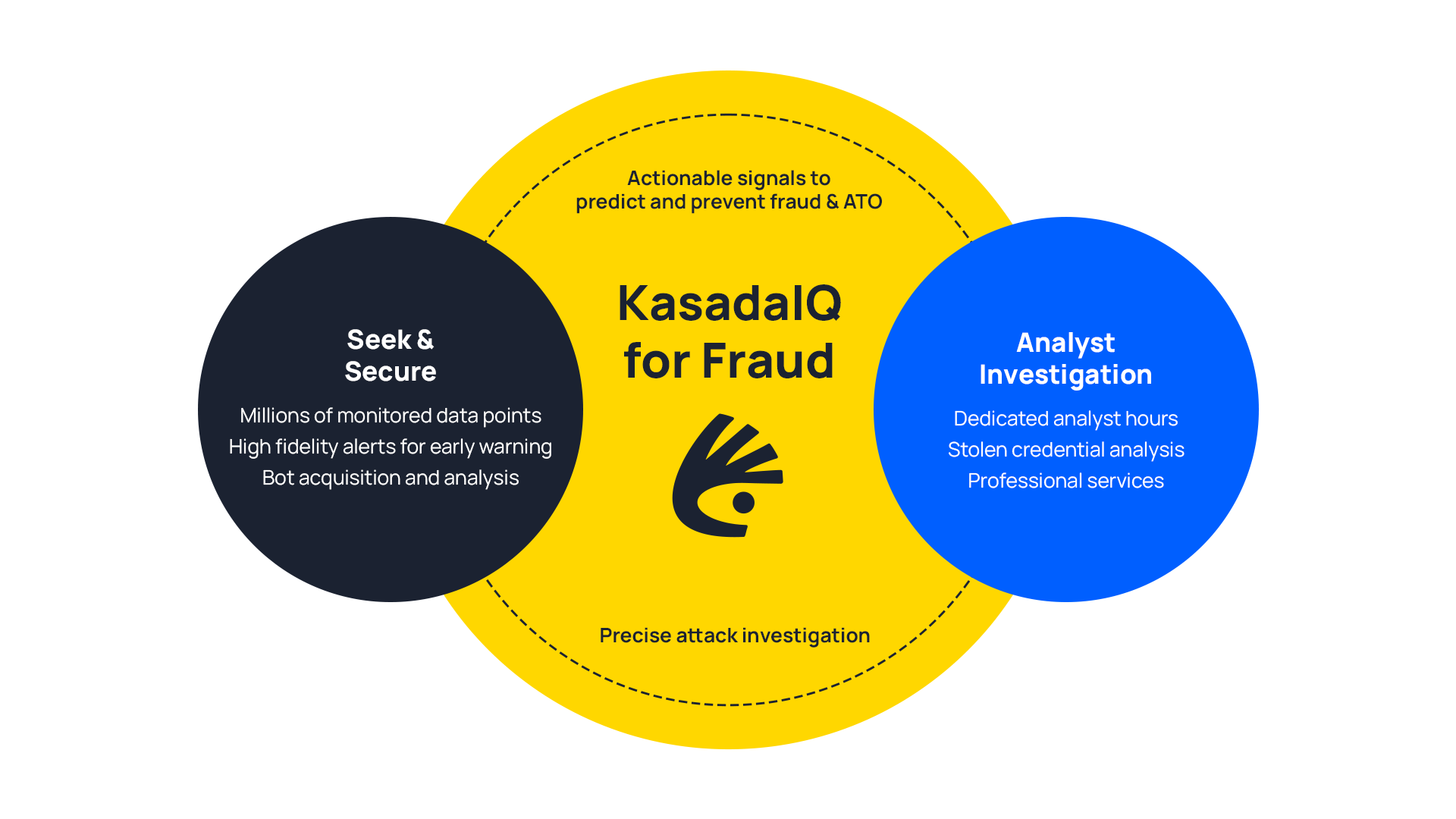
Kasada IQ for Fraud

Additional Info
| Company | Kasada |
| Company size | 50 - 99 employees |
| World Region | North America |
| Website | https://www.kasada.io/ |
NOMINATION HIGHLIGHTS
Fraud is incredibly costly for businesses, amounting to lost time, money, and reputation, while putting customers at risk. This growing problem was estimated to cost merchants $38 billion in 2023. Much of the threat arises from the growing sophistication of bot attacks perpetrated by a motivated, collaborative adversary community. These groups share and sell methods like CAPTCHA solvers to evade bot detection, perpetuating Account Takeovers (ATOs), fake account creation, and credential stuffing.
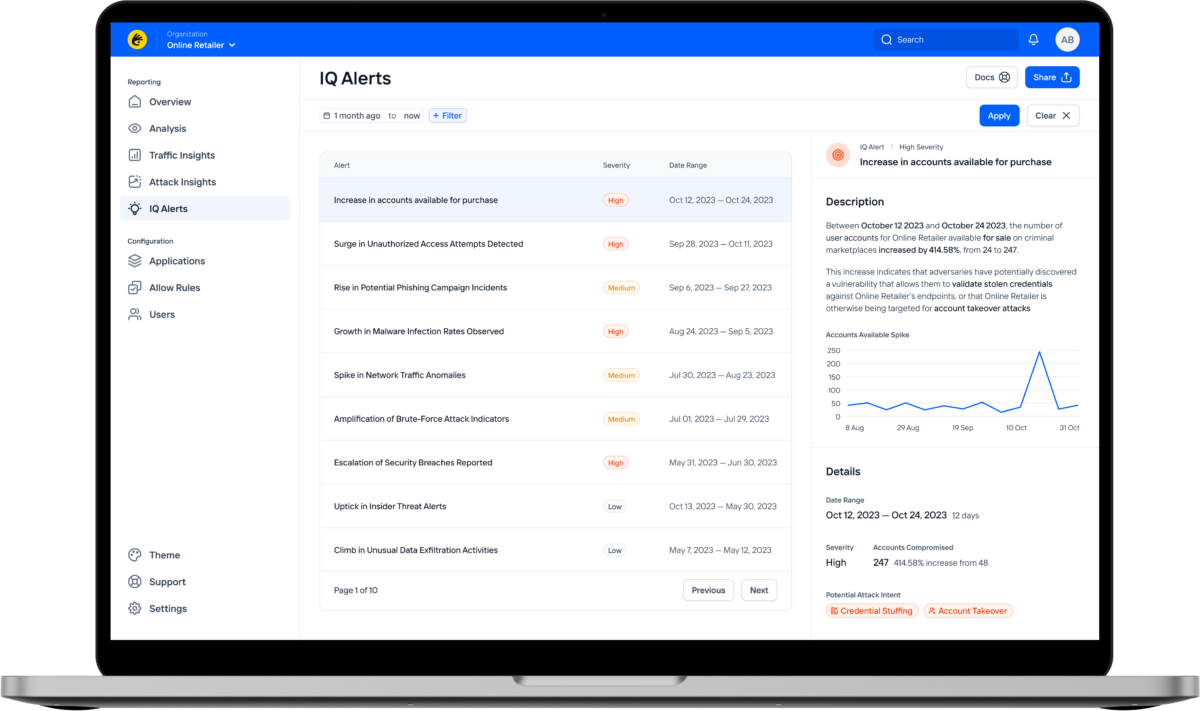
Kasada IQ for Fraud provides a market-leading capability to predict early indicators of attacks such as Account Takeover (ATO) before they happen and confirm threats that would otherwise go undetected. Kasada’s threat research team relies on over 2,000 non-traditional data sources, millions of data points across the internet, and covert infiltration of secretive adversary communities to monitor threats emerging in real time.
Key highlights:
-24/7 monitoring threat monitoring and actionable alerts of future and current threats, with detailed guidance of how to improve defenses. For customers of Kasada’s bot defense, Kasada automatically updates defenses to reflect new threats.
-Analyst investigation hours for deeper investigation of an issue or analysis of stolen credentials.
-Passing on the earliest warnings of a coming attack (such as a configuration file posted in a forum), Kasada provides actionable recommendations to shore up defenses and often prevents the attack entirely – removing significant downstream fraud.
-Reconstruction of detailed timeline of a past attack, from the first signs to its scale and impact (such as number of stolen accounts and monetization by attackers.)
-No integration whatsoever required.
-A high-touch experience where Kasada is effectively an extension of the customer’s fraud and security teams, responding within minutes.
Key Capabilities / Features
Unconventional Sourcing:
Kasada mines the most comprehensive intelligence from millions of data points from underground sources, detecting abuse of business logic and customer data missed by traditional monitoring methods.
Dedicated Analyst Hours:
Kasada’s analysts can dig deeper to investigate what’s most relevant – such as intelligence on specific fraud groups, reverse-engineering, or pinpointing security weaknesses in the customer’s environment.
Early Warnings:
Kasada analysts identify and vet current and emerging threats within Kasada’s own data system and then send actionable alerts, enabling customers to respond quickly and reduce alert fatigue.
Professional Services:
Kasada scopes custom requirements and provides guidance on how to achieve the outcomes customers want.
Bot Acquisition and Analysis:
Kasada secretly buys the bots targeting its customers, then cracks them open to see how they work. These may be targeted retail bots, account cracking scripts, or all-in-one bots - so customers know exactly what they’re facing.
Stolen Credential Analysis:
Kasada purchases and evaluates stolen credential sets from criminal marketplaces that target a customer’s users - or have come from their network – to remedy current and future security gaps.
How we are different
-Unparalleled visibility into fraud communities. Kasada has infiltrated secretive attacker communities that plan and collaborate to carry out attacks. It’s able to see the entire lifecycle of an attack, from first signs of planning to whether it was successfully carried out and monetized.
-Actionable intelligence, not just alerts. There is frustration in the market with “yet another threat intel feed” that spews data of limited use. Kasada IQ for Fraud’s alerts are targeted and actionable, and Kasada is hands-on to help the customer incorporate.
-New findings instantly reflected in defenses. For customers of its bot defense, new threat data is rolled into defenses very quickly - often within minutes. This is much faster than typical of the industry, where patches and updates can take weeks to roll out (and attackers then bypass again in 30 minutes).


