KELA’s RADARK – Cyber Threat Intelligence Solution
Recognized in the Category:
Photo Gallery
 |

 |
KELA's RADARK - Cyber Threat Intelligence Solution


Additional Info
| Company | KELA |
| Company size | 50 - 99 employees |
| Website | https://ke-la.com/ |
NOMINATION HIGHLIGHTS
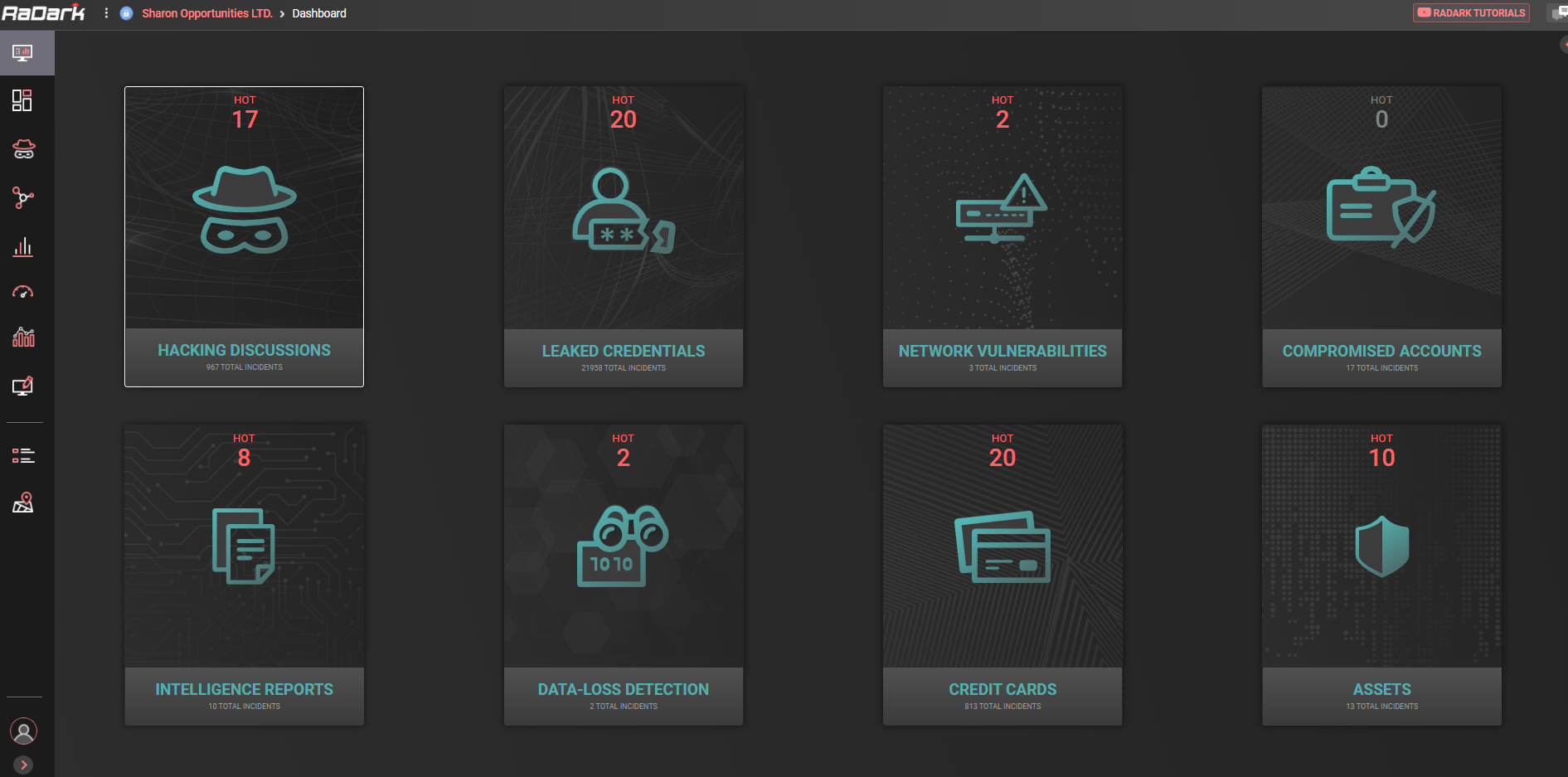
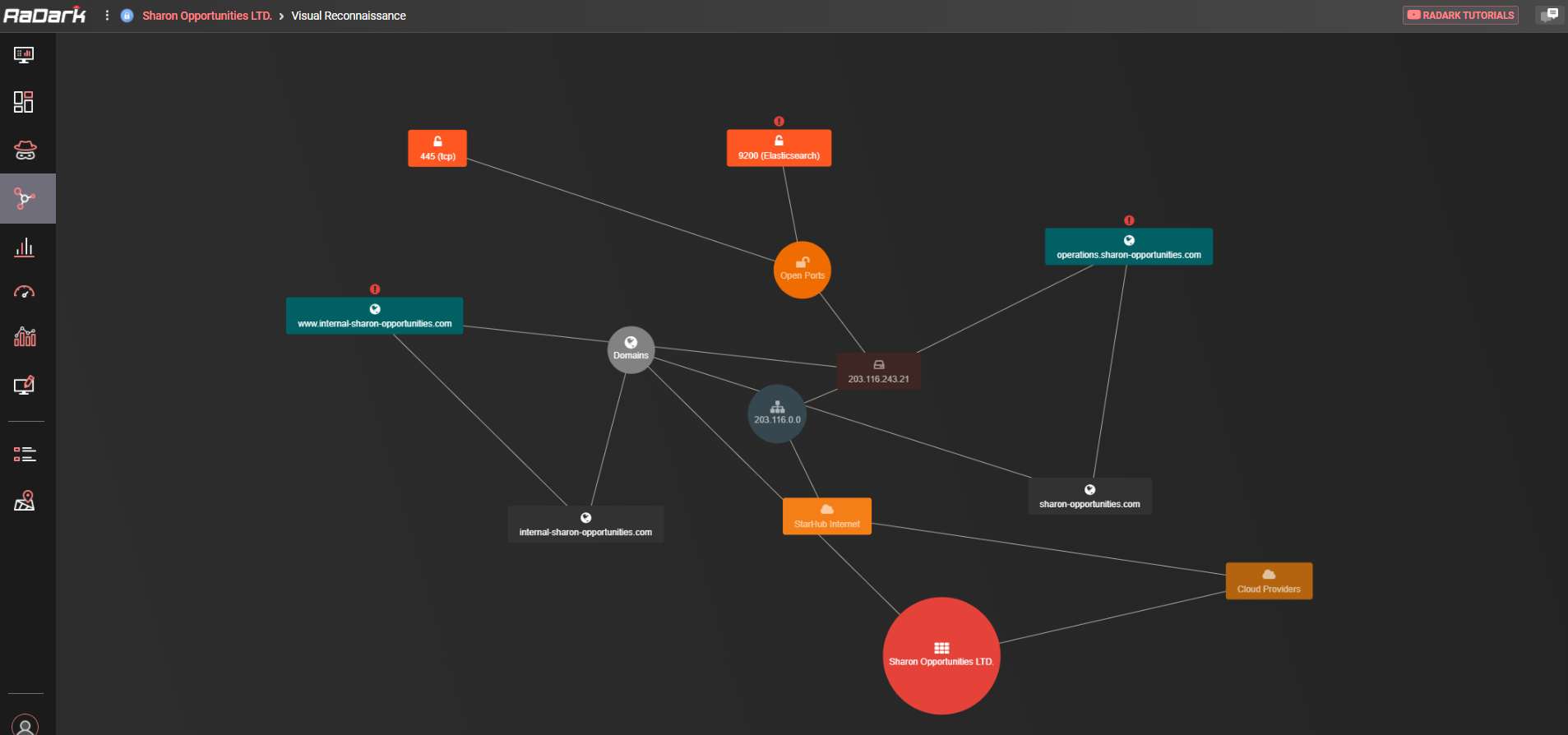
RADARK, KELA’s radar of the Dark Net, monitors a curated set of Dark Net sources to detect any mention of our clients’ key assets. Each client receives access to a customized dashboard where actionable and automated alerts are generated when a mention of their assets has been detected across sources that RADARK monitors. These sources include underground forums, information sharing sites, instant messaging groups, specialized auto-shops (such as botnet markets), code repositories, and more.
RADARK provides clients with a holistic view of their attack surface at all times, exactly as seen in the eyes of attackers. In order to ensure scalability and efficiency, RADARK works 100% automatically to collect targeted intelligence on our client’s assets. In order to ensure that these automated alerts are actionable, KELA’s experienced intelligence analysts are enriching and validating each threat that is generated. KELA’s team does not stop following the phase of early detection and warning of threats. KELA acts as a partner to the client’s team to support any additional remediation or mitigation steps required, such as account purchases, enrichment of alerts, interaction with threat actors, and more. The combination between the automation and the analyst services, provides our clients with a unique cyber threat intelligence solution.
RADARK is most used by CTI teams, fraud detection teams, brand protection and corporate security teams, vulnerability management teams, insider threat teams, and supply chain risk management teams.
How we are different
- Targeted Intelligence: In order to ensure we're saving our clients time, we make sure that they're only receiving alerts that are 100% related to their assets. We won't flood our clients with alerts on general industry threats if it is not directly targeting them or their supply chain in any way. That way, our clients can focus on real threats posing immediate risks to them.
- Double Curation Methodology: At the basis of all our source collection, KELA has a team of intelligence and Dark Net experts that are continually locating, analyzing and qualifying new information sources daily. Once curated, those sources are stored in our data lake so that all information will be accessible at all times. The monitoring is then done from within our internal systems so that our client's information is not exposed in any way. All alerts that clients receive are first checked by our analysts, ensuring an extra layer of curation to prevent our clients from receiving any false-positive threats.
- Managed Intelligence Services: KELA has a team of intelligence experts that leverage experiences from Israel's elite military intelligence units. As part of KELA's offering, clients can choose from a variety of levels of support from our team. These managed intelligence services include anything from one-time threat assessments or reports, all the way to a dedicated intelligence analyst that becomes a partner of our client's team to support them in their daily intelligence operations. To ensure that our clients are always receiving fully contextualized intelligence, we offer multiple services to support our clients’ intelligence needs, including round-the-clock intelligence support, secured threat actor interactions and communication, ongoing responsiveness to RFIs, takedowns and account purchases, and more.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



