Kenna Vulnerability & Risk Intelligence platform
Nominated in the Category:
Photo Gallery
 |
 |
Kenna Vulnerability & Risk Intelligence platform

Additional Info
| Company | Kenna Security |
| Company size | 50 - 99 employees |
| Website | http://www.kennasecurity.com |
NOMINATION HIGHLIGHTS
Kenna is an innovative vulnerability and risk intelligence platform that processes more than 1 million vulnerabilities each hour, helping IT teams prioritize and thwart would-be security threats.
Organizations today face a lot of vulnerabilities – including malware exploits, out-of-date software, IT compliance issues, new technologies being introduced to the system and more - but are unable to prioritize, report and remediate them effectively across enterprise-wide systems. Traditional, human-powered monitoring and tracking in spreadsheets no longer works to address the speed at which change occurs and attackers advance. The modern enterprise needs data science at scale, and a way to measure risk that can be presented everywhere, including inside the boardroom.
Kenna knows how to solve these problems, and has experienced firsthand just how frustrating and challenging vulnerability management can be – the struggles with being unable to keep up with the volume of scan data, having to settle for inadequate security due to budget constraints,
picking a remediation list at random (and hoping for the best), and being unable to measure and report on efforts to reduce exposure to risk.
Kenna’s approach to threat and vulnerability management integrates the results of vulnerability scan data—Qualys, Nessus, Rapid 7, and dozens more—with the results from 8 different threat feeds. The result? A clear list of what vulnerabilities need to be prioritized in order to improve a company’s security posture. This also makes it simpler to report on activity and show the impact of remediations.
How we are different
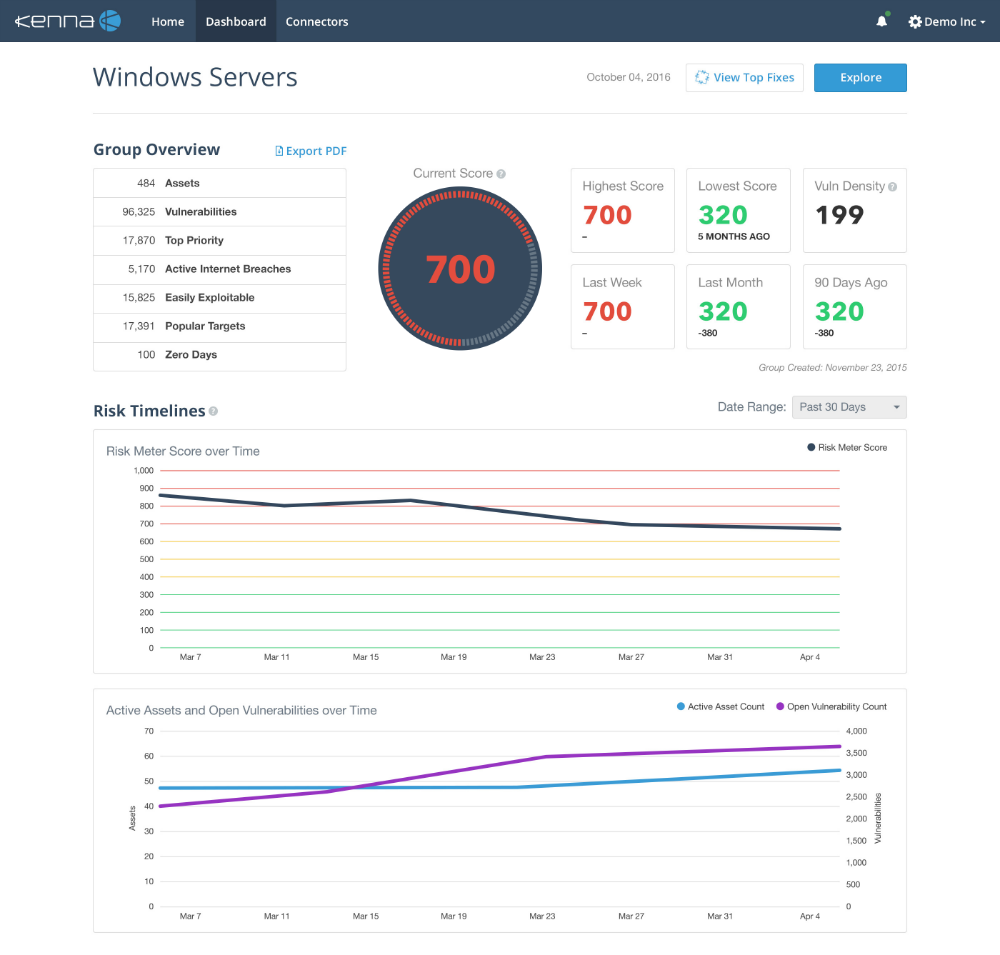
The Kenna Risk Meter lets you know exactly what risk you incur across all your groups of assets by displaying the results of both your vulnerability scan data as well as external threat intelligence so that you can clearly see which assets are subject to active Internet breaches, exploits and zero-day threats.
● Kenna also helps customers shave hours off their remediation time by prioritizing the most important remediations based on real-world threat intelligence. Kenna correlates attack, threat and exploit data aggregated by its threat processing engine against customers’ vulnerabilities twenty-four hours a day, seven days a week. Furthermore, if you want to achieve a certain risk score, Kenna will present exactly the vulnerabilities you need to remediate in order to get to your desired level.
● Kenna also makes reporting easier and better with asset tags and groups that help make data more relevant and allowing for customization of reporting, access, remediation and dashboards. Its unique tagging system offers greater flexibility by allowing users to organize assets right within the Kenna platform and enabling users to easily see the vulnerabilities for any part of their environment. Kenna Alerts provide the ability to proactively stay on top of risk across the environment. Emails or in-app notifications let users know when risk reaches critical thresholds, or when most valued asset groups face new threats, so they can take immediate action.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



