Photo Gallery
 |
 |
Kenna Security, Kenna.VM

Additional Info
| Company | Kenna Security |
| Company size | 100 - 499 employees |
| Website | http://www.kennasecurity.com |
NOMINATION HIGHLIGHTS
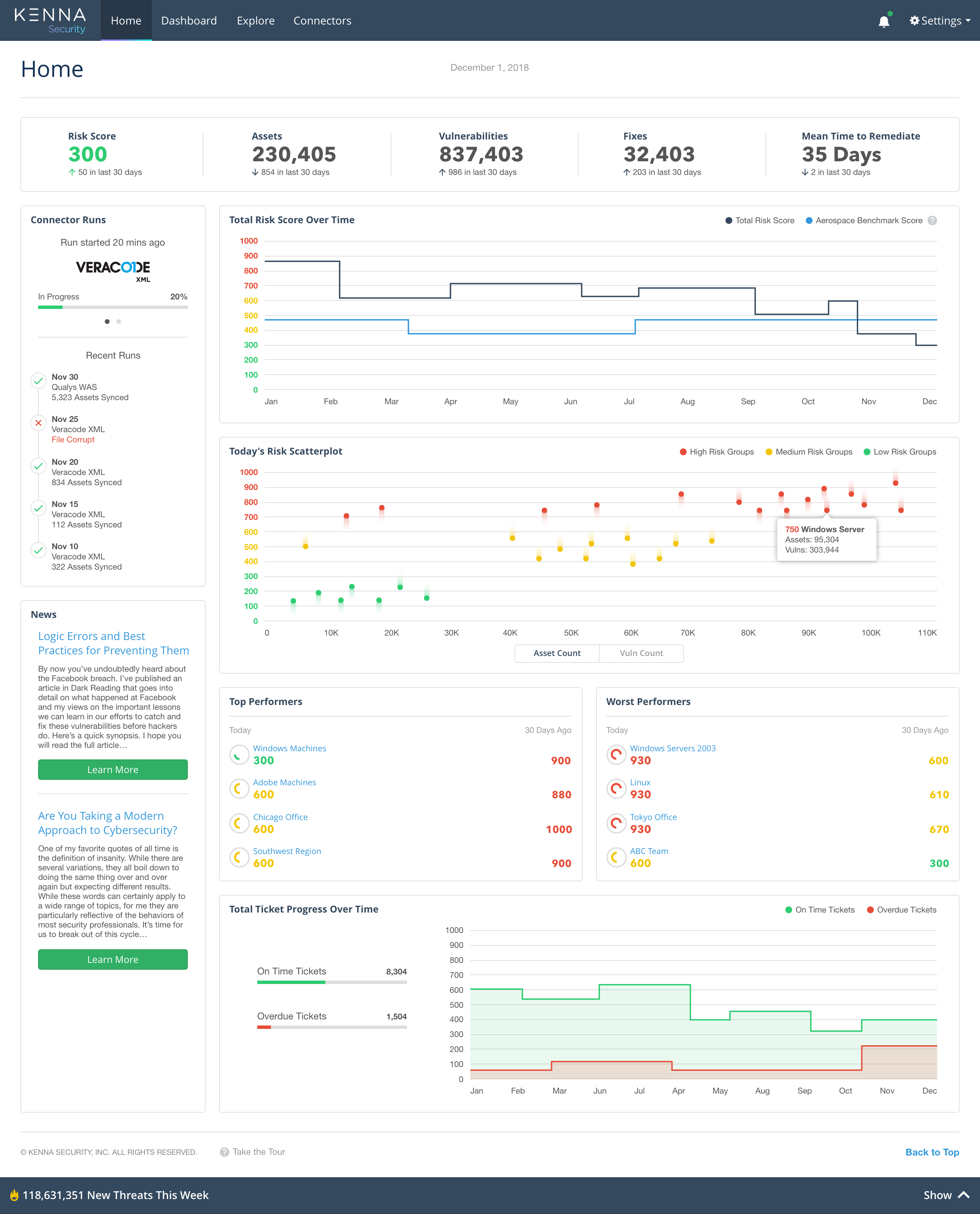
Unlike traditional vulnerability scanners and management systems, Kenna leverages both external and internal data from enterprise assets and “in the wild” threat intelligence. This real-time, reality-based context enables Kenna to prioritize vulnerabilities by their impact on the business to assure that work is prioritized to optimally and demonstratively improve security posture. This Data Science and “in the wild” context approach behind Kenna is unique – no other company has achieved the results that Kenna has to date, or is as widely deployed in more than 350+ IT departments.
Kenna extends its proactive cyber risk to predictive cyber risk with its Exploit Prediction capabilities that leverage Kenna Cyber Risk Context Technologies™. Kenna Exploit Prediction model has been third-party tested (https://www.kennasecurity.com/prioritization-to-prediction-report/) to deliver greater efficiency, far less effort, fewer false positives, and better coverage of an organization’s attack surface over other common vulnerability remediation strategies.
Kenna Security’s patented technologies cover vulnerability identification based on breach data, internet breach correlations, and ordered computer vulnerability remediation reporting. (https://www.kennasecurity.com/news/kenna-security-granted-patent-for-machine-learning-methods-used-to-predict-exploits/) These protected technologies are all necessary to compute risk for IT assets and risk-based remediation.
How we are different
- The primary tool industry competitors use to evaluate vulnerability risk, the Common Vulnerability Scoring System (CVSS), is not designed to predict weaponization - rather, it predicts the damage a vulnerability would do if it were weaponized. While CVSS scores contain much of the data that could predict the likelihood of weaponization, that data is not organized or analyzed to do so. Kenna Security’s platform, Kenna.VM, uses data science to identify vulnerabilities that are under attack in the wild, predict which vulnerabilities are likely to be weaponized, and determine which vulnerabilities organizations can safely ignore.
- Kenna.VM, leverages more than 15 exploit intelligence feeds, a knowledge base of 7+ billion (and growing) managed vulnerabilities, and data-backed predictive modeling all presented in easy-to-use dashboards that offer high levels of visibility into which factors make some vulnerabilities more dangerous and which actions will drive the largest reduction in overall risk.
- Kenna Security’s patented technologies cover vulnerability identification based on breach data, internet breach correlations, and ordered computer vulnerability remediation reporting. These protected technologies are all necessary to compute risk for IT assets and risk-based remediation.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



