Photo Gallery
 |
 |
LogicHub SOAR+

Additional Info
| Company | LogicHub |
| Company size | 50 - 99 employees |
| Website | https://www.logichub.com/ |
NOMINATION HIGHLIGHTS
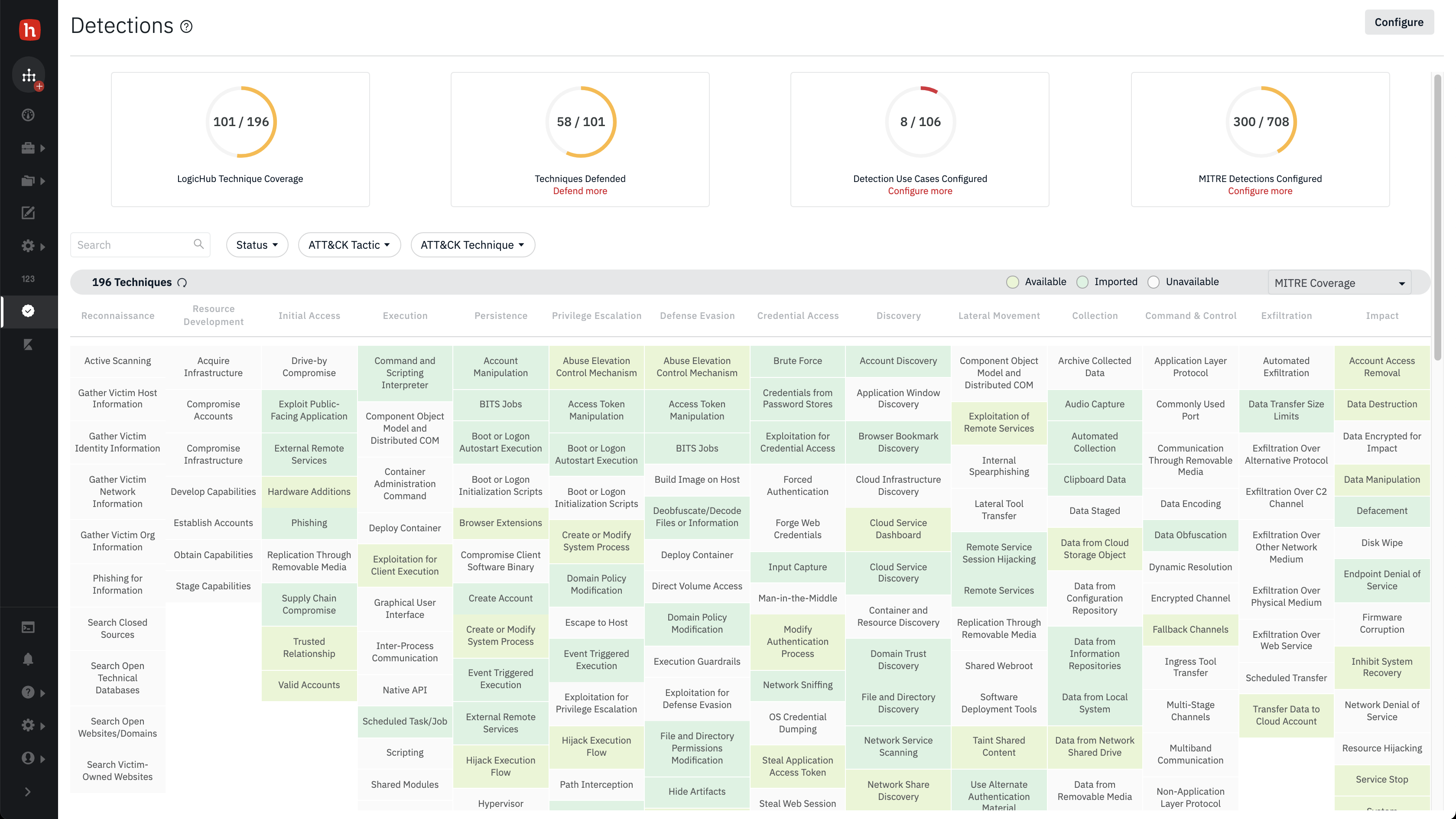
LogicHub’s SOAR+ platform is the industry’s most powerful automation platform for security operations, empowering SOC teams with end-to-end automation and orchestration that automates the entire threat lifecycle – from threat detection and analysis, alert triage, incident response, threat hunting, and forensic investigations.
Traditional SOAR solutions aren’t architected to keep up with the high volume of alert and event data necessary to accurately detect true positive threats at scale. Security analysts can’t manually investigate every security event and alert, leaving them dependent on legacy security tools notorious for generating false positives for threat detection.
LogicHub’s SOAR+ automatically analyzes, investigates, and detects threats at machine speeds, and is capable of processing millions of raw security events and alerts per day while eliminating 99% of false positives.
LogicHub’s detection playbooks automatically analyze and investigate all data, accurately identifying true positive threats faster and reducing mean time to detect. Automating threat analysis and investigation eliminates the traditional delay between detection and response, leading to both faster detection and response times. And automating previously manual detection activities frees your security analysts to focus on responding to confirmed threats.
How we are different
• LogicHub’s SOAR+ platform is built on expertise automation and a blend of expert systems with deep neural net architecture that is more precise and designed to work with a reduced amount of data. The engine progressively learns and updates its own logic to make more accurate decisions like a human analyst. LogicHub automatically analyzes millions of security events per day from any source to detect and hunt threats, triage alerts, and respond with consistent precision and machine speeds.
• Identifying Malicious Powershell Commands: LogicHub playbooks automate the analysis and investigation of powershell activity to identify suspicious and malicious activity rapidly and accurately. Using a combination of machine learning and external integrations, LogicHub automatically creates baselines of expected Powershell behavior and establishes profiles of known malicious Powershell activity. Any new Powershell actions are automatically analyzed and assigned an appropriate risk score. When malicious activity is detected, it can be immediately stopped and future Powershell attacks of the same kind can be automatically prevented.
• Detecting Exposed AWS Keys: LogicHub playbooks can automatically detect exposed keys and help expedite response in multiple ways. When Amazon detects exposed AWS API keys, they send an email notifying the appropriate resources. LogicHub can continuously watch for those emails and when one is received, can automatically pull the API key from the email, and disable it to prevent it from being used in an attack. LogicHub can also automatically hunt for exposed keys on repositories like Github or Pastebin and then notify the appropriate personnel while disabling the exposed key. LogicHub can also use machine learning to baseline normal activity tied to the use of AWS API keys to automatically detect and respond to malicious activity.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



