Photo Gallery

|
|
Magnet Forensics – Magnet Response

Additional Info
| Company | Magnet Forensics |
| Company size | 500 - 999 employees |
| World Region | North America |
| Website | http://www.magnetforensics.com |
NOMINATION HIGHLIGHTS
Magnet Response empowers DFIR analysts and non-technical users to easily collect and preserve critical data relevant to incident response investigations from local endpoints (offline).
Magnet Response is a free and easy-to-use solution to quickly collect and preserve data from local endpoints before it is potentially modified or lost. A pre-set collection profile gives you the ability to target a comprehensive set of files and data relevant to incident response investigations, including RAM.
Minimal to no training is required—it’s as simple as running it on the endpoint, configuring the collection and clicking “start capture.” This makes Magnet Response useful in situations where non-technical users may need to collect and preserve data on behalf of law enforcement investigators as part of a cyber incident investigation.
Key Capabilities / Features
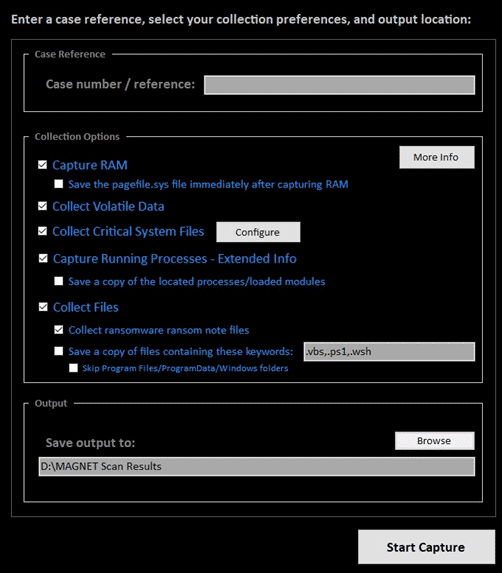
> Data collection options:
Configure a collection by selecting from a comprehensive set of options, including RAM, pagefile.sys, ransomware ransom note files, capture running processes, and volatile data. Saves the following items:
- Network connections
- Running processes (basic list)
- Logged-on users
- Scheduled tasks
- IP config info
- Firewall info
- Wi-Fi info
- Windows services
- Local users accounts
- Windows version details
Note: Data is saved to individual text files to enable quick review
> Collect critical system files:
Collects the following files/locations:
- Master file table ($MFT)
- Registry hives
- NTUSER.DAT files
- UsrClass.dat files
- Recent link files
- Amcache data
- Jumplist files
- PowerShell history
- SRUM data
- Scheduled tasks
- Windows timeline data
- Windows event logs
- Prefetch files
- Firewall logs
- TeamViewer logs
- AnyDesk logs
- LogMeIn logs
- Recycle bin
- Chrome browser history
- Edge browser history
- Firefox browser history
> Collect by keyword and skip large files:
Configure free-form collections using your own set of keywords (or the defaults provided), with the option to limit the size of files collected to maintain speed.
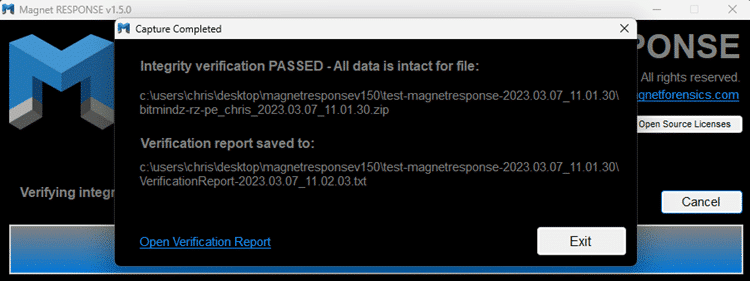
> Consolidated output:
Output is consolidated and saved as a .zip file for easy delivery or processing and analysis in Magnet Axiom and Magnet Axiom Cyber
> Data integrity:
An embedded hash value is provided to verify the integrity of the data
How we are different
Easy-to-use: A guided two-step process and progress bar is straightforward for even non-technical users.
Fast and comprehensive: Collect and preserve data starting with the most volatile using the built-in Comae RAM capture (Magnet DumpIt) functionality, as well as volatile data and files commonly associated to cybercrime, such as Windows event logs, Registry hives, Jumplist files, and many other log files in minutes—no need for multiple tools to get the IR data you need.
Portable: It is comprised of a single executable file, is easily downloaded, and can be stored and run from a USB key.


