Photo Gallery
 |

 |
ManageEngine Log360

Additional Info
| Company | ManageEngine |
| Company size | 5,000 - 9,999 employees |
| Website | https://www.manageengine.com/ |
NOMINATION HIGHLIGHTS
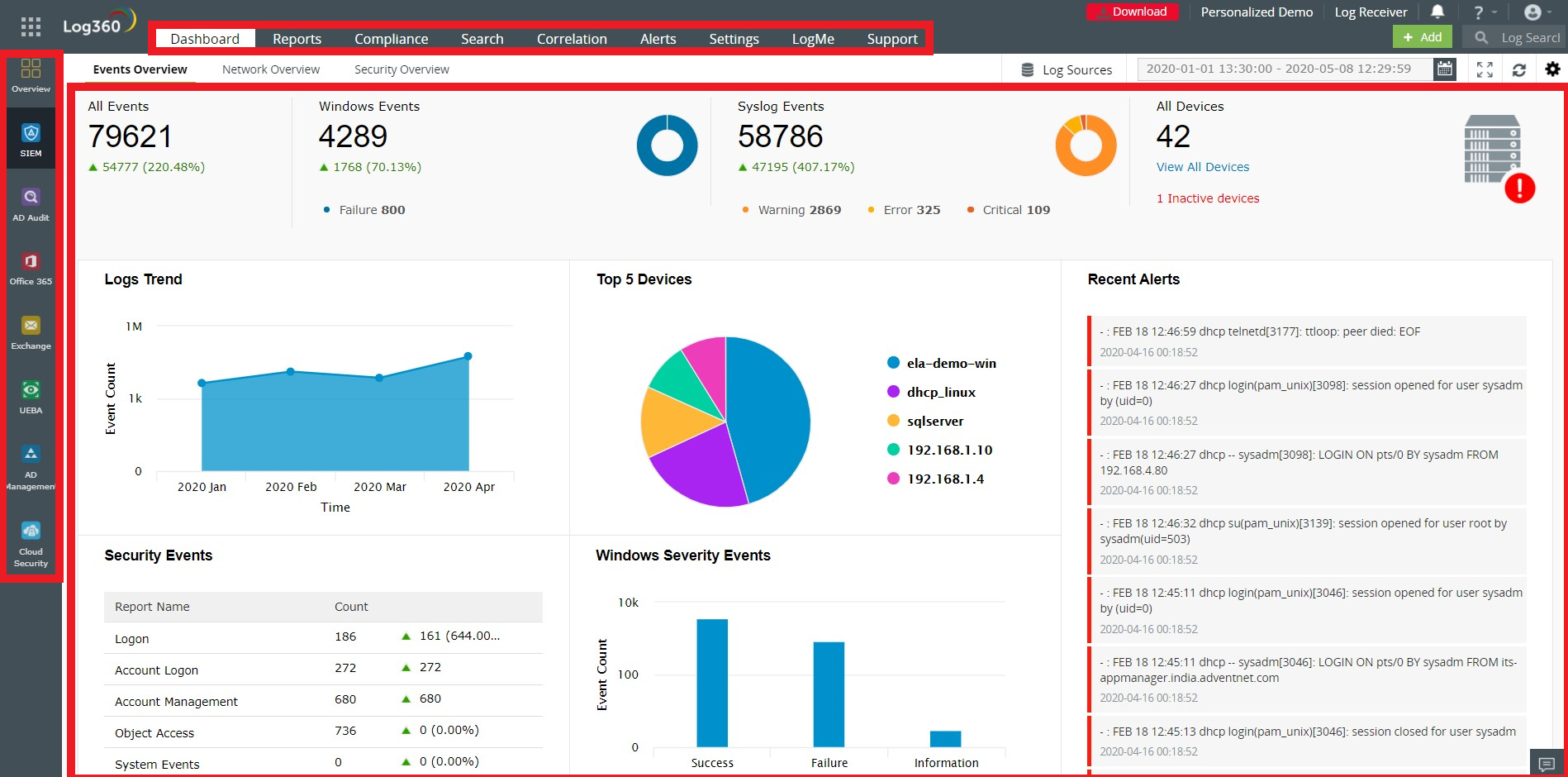
Log360 is a unified SIEM solution with integrated DLP and CASB capabilities to detect, investigate, and respond to security threats. With Log360, you can improve the productivity of your SOC.
Several capabilities from a single console: Network infrastructure security, data security, log forensics, anomaly detection using machine learning algorithms, compliance management, threat intelligence, cloud monitoring, a CASB, user and entity risk analysis, and incident detection and resolution.
1. Data ingestion from over 750 types of log sources: This includes Active Directory, network devices, databases, workstations, endpoint solutions, data loss prevention systems, vulnerability scanners, applications, and cloud services. Organizations can also parse logs from custom applications.
2. Security analytics: Insightful and actionable security analytics are provided for activities that happen in every part of the network. Analytics are logically arranged so that it is easy to find them. Users can also configure alerts based on unique security use cases.
3. Incident response: You can configure workflows and playbooks for mitigating incidents. The solution can be integrated with various third-party help desk and ticketing tools. Technicians can be assigned incidents automatically using rules, and the incident resolution status can be tracked continuously.
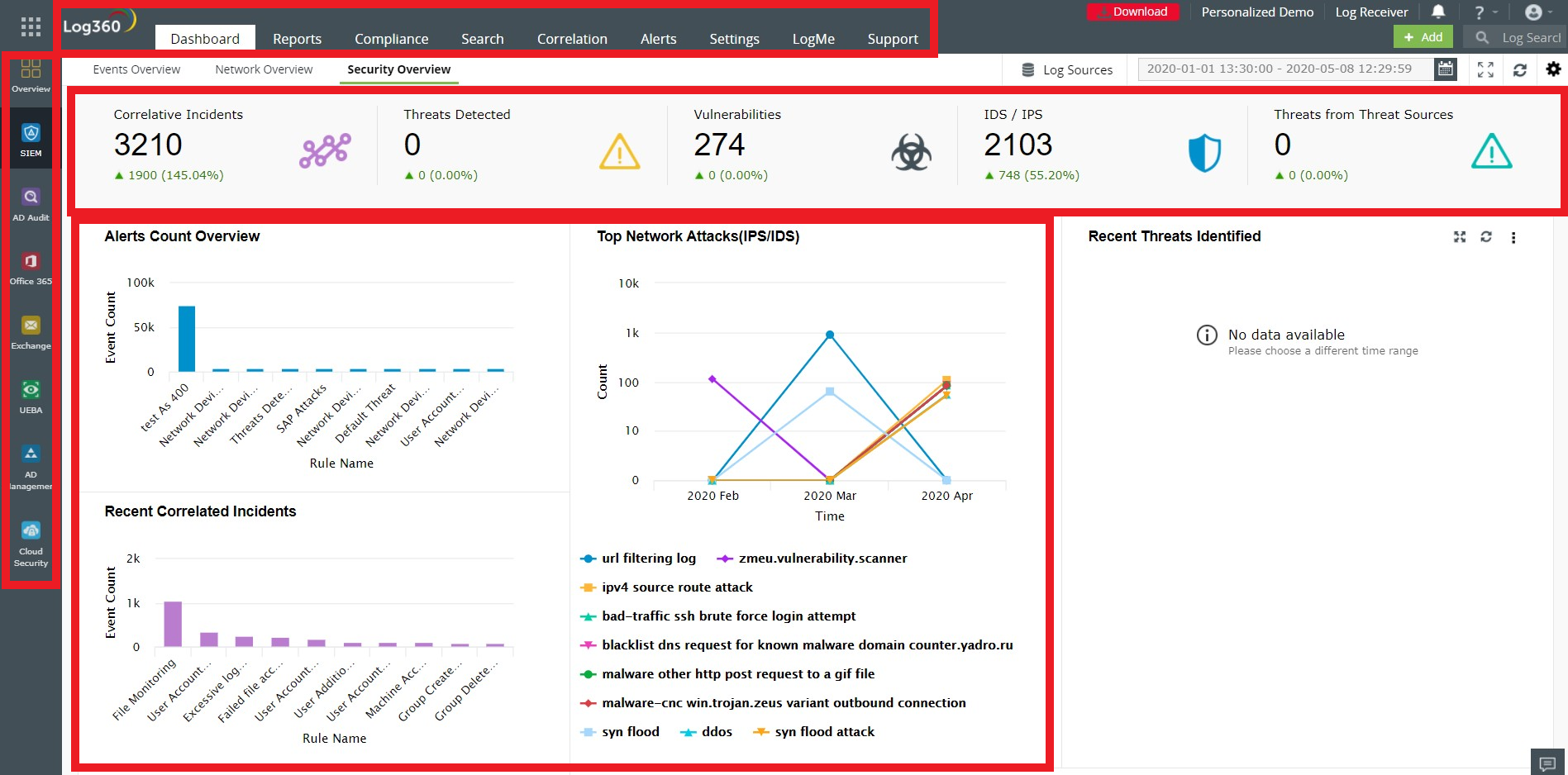
4. Correlation of events: The correlation engine enables users to put together seemingly unrelated events from across the network and classify them as potential threats. Built-in correlation rules are provided within the solution along with the option to build custom correlation rules.
5. Anomaly detection: The anomaly detection engine within Log360 can spot behavior abnormalities in users and hosts in a network. Based on the extent of abnormal deviation, a risk score is assigned to every entity. This helps IT teams focus on the most pressing threats first and decreases the number of false positives. There are also options available to customize risk scoring and build your own anomaly models.
How we are different
1. Caters to organizations' security use cases: There are more than 30 predefined analytics and reports pertaining to popular security use cases such as brute-force attacks, denial-of-service attacks, ransomware, cryptojacking, and more. Analytics provide the entire timeline of the possible attack along with the ability to search for, find, and drill down the root cause.
On top of this, you also have the flexibility to build your own rules for unique use cases. When building your rules, you can leverage Log360's integration with the MITRE ATT&CK framework to identify different tactics and techniques that cyberattackers use. This will give structure to your threat detection capabilities. We will keep adding capabilities so that out-of-the box analytics are provided for new use cases and new attack tactics.
2. Reduces the number of false positives: Each incident lists all the involved entities, users, and processes along with the activity timestamp. You can perform your analysis quickly and follow up on only the incidents that need to be investigated further. You can also use the log collection and alerting filters so that only relevant alerts are generated. Furthermore, the anomaly detection engine powered by user and entity behavior analytics (UEBA) helps to significantly reduce false positives. It introduces risk scoring so you can prioritize incidents. You can modify alert rules to fit with the requirements of your organization. This can, in turn, reduce false positives.
3. A CASB-integrated SIEM solution: The cloud security module of Log360 can monitor activities that happen on public cloud platforms such as AWS, Azure, Salesforce, and Google Cloud Platform. It can also audit changes that happen on Azure Active Directory. It can also ensure effective data loss prevention by monitoring data that flows out of the organization onto the cloud. It can also monitor the use of banned and shadow applications.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



