Photo Gallery
 |
 |
Mandiant Advantage Security Validation

Additional Info
| Company | Mandiant |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.mandiant.com/ |
NOMINATION HIGHLIGHTS
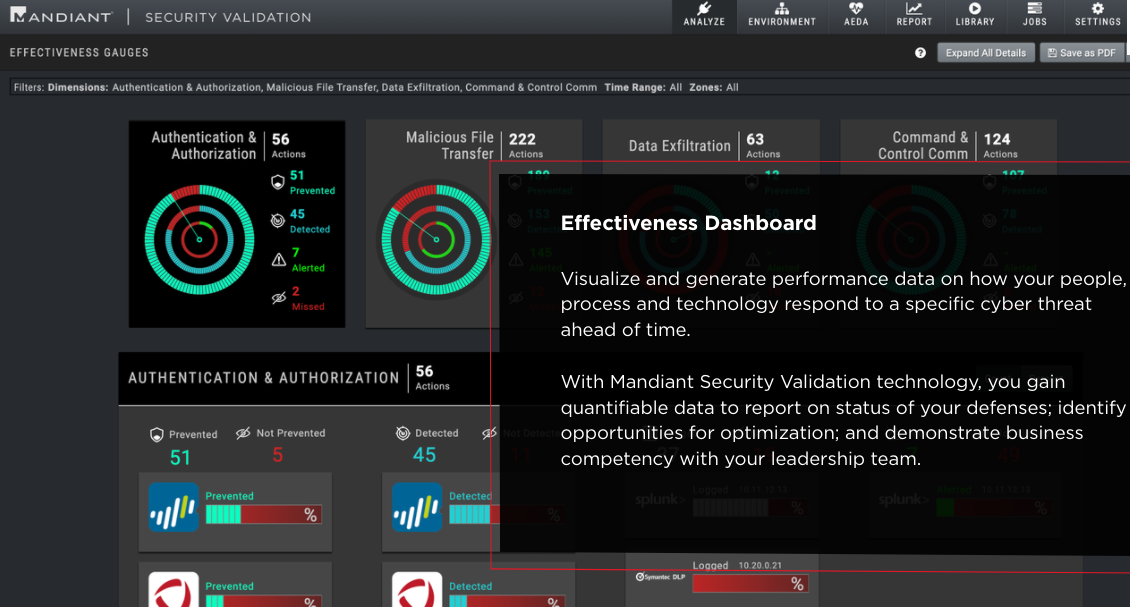
Gain evidence of your cyber readiness against adversary threats targeting your organization. Until now, there has been no measurable way for security organizations and leaders to prove their cybersecurity programs are working and the value of security investments. Knowing you’re prepared against today’s adversaries requires expertise, intelligence and innovative technology. Mandiant Advantage Security Validation arms security teams with the ability to test their security controls against the threats that are most relevant to their organization. Security Validation is powered by Mandiant frontline threat intelligence to use active and relevant threat actor TTPs and automate a testing program that gives teams real data on how their security controls are performing. Visibility and quantifiable data gained through automated and continuous validation enables security teams to optimize their security environment and make the right investments in the future.
Mandiant Advantage Security Validation enable defenders to:
– Visualize and capture data based on how their security controls respond to authentic cyberattack scenarios ahead of time, assisting organizations with quantifiable data to report on the status of its defenses, identify opportunities for improvement and demonstrate business competency to leadership
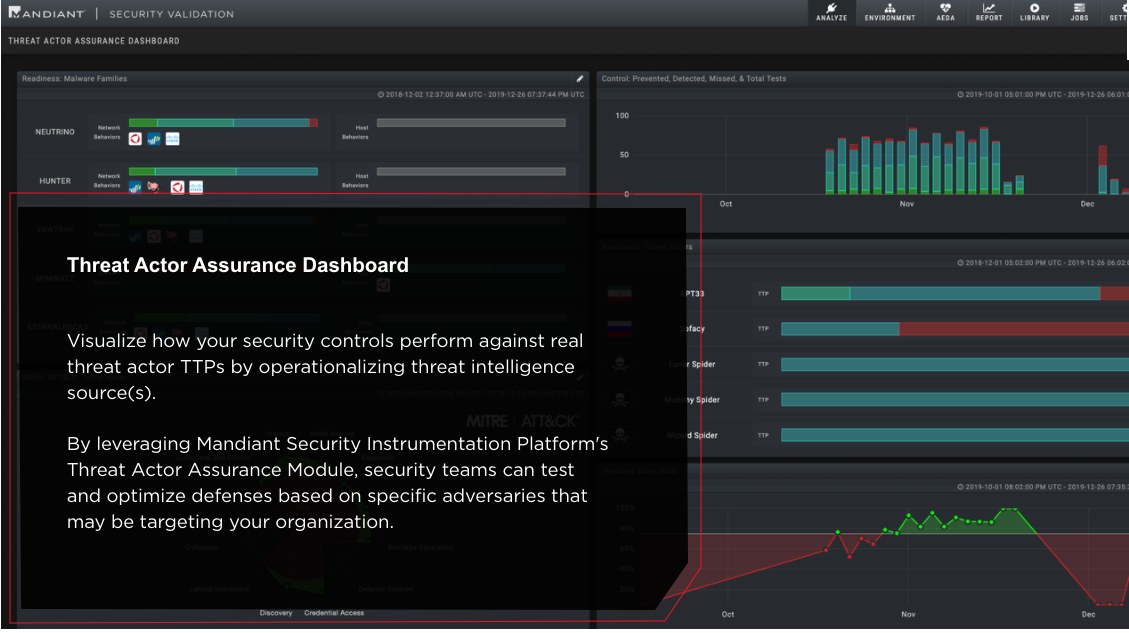
– Visualize, prioritize and test how controls measure up to the MITRE ATT&CK Framework in real-time. Intelligence led validation arms security teams with attacker TTPs (tactics, techniques and procedures)—a depth and breathe of validation content to align with MITRE ATT&CK or other industry attack frameworks.
– Measure how security controls perform against real threat actor TTPs by operationalizing threat intelligence source(s).
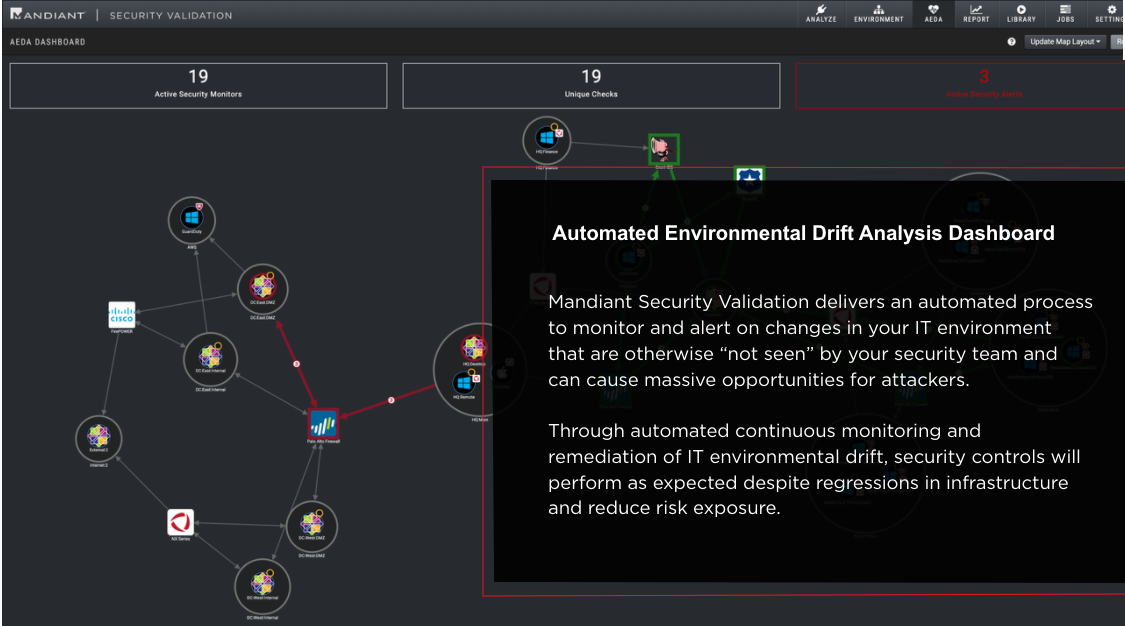
– Monitor and alert on changes in IT environments that are otherwise “not seen” by security teams and can cause massive opportunities for attackers. Through automated continuous monitoring and remediation of IT environmental drift, security controls will perform and reduce risk exposure.
How we are different
Security validation is more important now than ever before, with adversaries becoming increasingly sophisticated and targeted in their attacks. Yet, despite knowing just how devastating a cyberattack can be, many organizations are not able to consistently prove that they can prevent or detect threats within their environment. One of the causes of this low detection rate is the “set it and forget it” scenario. Security teams install security tools in their default configurations and may fail to perform updates. Another challenge is when an organization lacks insight into the threats that are most relevant to their specific environment and need access to active, authentic attacker TTPs to support testing for security controls effectiveness. Without active threat intelligence to guide relevant testing and the ability to safely validate defenses in an authentic way, many security teams blindly trust that their controls are working and protecting critical assets
Mandiant Advantage Security Validation overcomes these challenges with innovative validation technology informed by Mandiant Threat Intelligence. Below are just a few industry-leading differentiators that are unique to Security Validation:
- Access to leading threat intelligence: Mandiant frontline intelligence and incident response data that can focus resources on specific and relevant threats facing your organization.
- Real Attacks: Emulations of real attack binaries across the full attack lifecycle with deep and comprehensive integration with your entire security infrastructure. This includes safe deployment of top malware and ransomware families into an organization’s production environment to validate defenses against today’s most formidable threats.
- Prevent environmental drift: Continuously monitor your IT environment to detect and remediate unseen changes to your security architecture.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



