Photo Gallery
 |
 |
MetaAccess

Additional Info
| Company | OPSWAT |
| Company size | 100 - 499 employees |
| Website | https://www.opswat.com/ |
NOMINATION HIGHLIGHTS
Using OPSWAT’s industry-leading endpoint security and advanced threat prevention technologies, MetaAccess empowers organizations to enforce internal security standards and meet security and regulatory compliance across all devices accessing corporate data, whether the devices are corporate-owned or not.
With MetaAccess companies can:
Protect Corporate Data
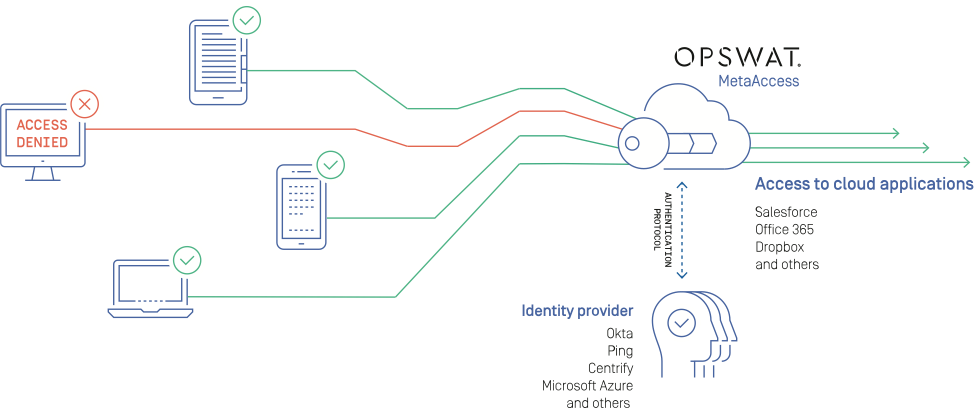
MetaAccess protects corporate data by ensuring that only compliant devices are allowed to access local networks and cloud applications. In addition, MetaAccess provides enterprise-wide visibility into all managed devices, allowing for easy identification of security and compliance issues as well as detailed device information.
Aid Regulatory Compliance
MetaAccess helps organizations meet regulatory requirements by preventing risky devices from accessing corporate data, as well as increasing insight into unmanaged devices by linking user identity to devices when accessing cloud applications. MetaAccess further provides reports that can be useful for assisting with regulatory compliance audits, such as required by FINRA, HIPAA, Sarbanes-Oxley and others.
Streamline User Experience
MetaAccess offers simplified control over endpoint device posture without requiring any actions of the end user. Unlike the traditional VPN and network access control (NAC), through seamless authentication protocol integration such as SAML, MetaAccess enables cloud applications and SSO solutions to enforce device posture on an application-by-application basis with ease.
How we are different
• MetaAccess exposes the broadest set of endpoint security checks on the market, including endpoint security application status, patch level, threat detection and indication of device compromise.
• MetaAccess uniquely addresses the complex BYOD ownership problem by showing the user's identity (IdP or application user name) for each device when accessing cloud applications, increasing unmanaged device control without requiring any IT infrastructure changes, network traffic manipulation, or mobile device management (MDM).
• MetaAccess offers comprehensive policy configuration options and customizable remediation pages that enable organizations to customize the solution to their specific business needs. REST APIs are provided to enable developers to add cloud access control to their existing security solutions, avoiding the need to develop their own endpoint solutions.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



