Photo Gallery

|
|
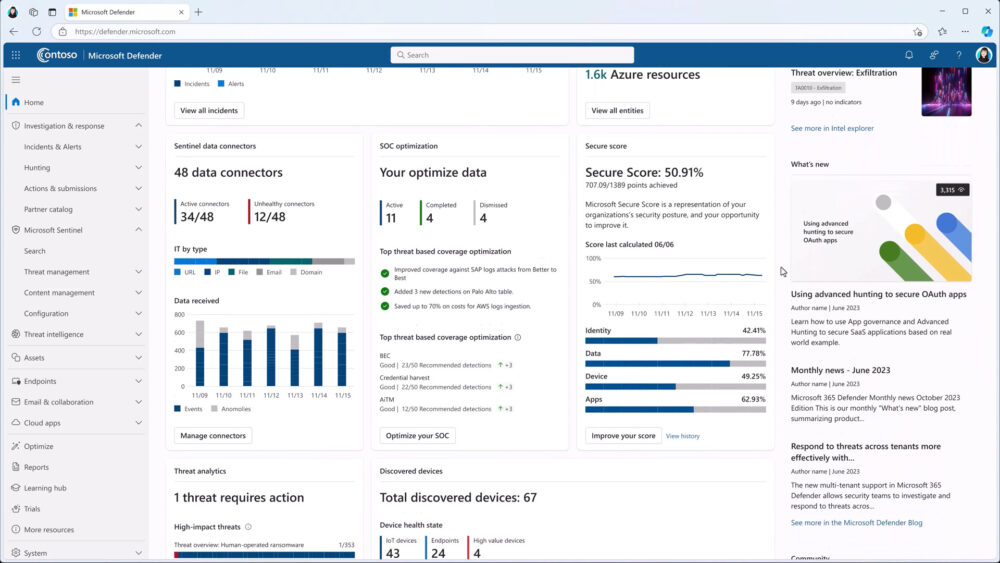
Microsoft Defender for Endpoint

Additional Info
| Company | Microsoft |
| Company size | 10,000 or more employees |
| World Region | North America |
| Website | https://www.microsoft.com/en-us/security/business/endpoint-security/microsoft-defender-endpoint |
NOMINATION HIGHLIGHTS
Microsoft Defender for Endpoint is an enterprise-grade security platform designed to prevent, detect, investigate, and respond to advanced threats across endpoints. It integrates seamlessly with other Microsoft services to provide comprehensive protection.
Microsoft Defender for Endpoint stands out in the endpoint security market by offering a comprehensive, integrated, and proactive approach to threat management, making it a strong candidate for recognition in the endpoint security category.
Outmaneuver sophisticated adversaries with AI – Stop cyberattacks such as ransomware and move at machine speed with industry-transforming AI that amplifies your security team’s strengths.
Boost prevention with global threat intelligence – Minimize vulnerabilities with a clear view of your cyberattack surface and adversaries, along with best practices for cyberthreat prevention.
Secure devices end to end – Help protect your multiplatform and IoT devices with a comprehensive, industry-leading next-generation antivirus, detection, and response solution at the core of Microsoft Defender XDR.
Key Capabilities / Features
- Next-Generation Protection: Offers behavior-based, heuristic, and real-time antivirus protection, along with cloud-delivered updates for near-instant detection and blocking of new and emerging threats.
- Endpoint Detection and Response (EDR): Provides real-time surveillance across all endpoints, collecting and analyzing data to flag suspicious activities promptly.
- Automated Investigation and Remediation: Utilizes automated processes to investigate detected threats and neutralize issues without manual intervention, minimizing disruptions.
- Threat and Vulnerability Management: Continuously scans for vulnerabilities, prioritizes them, and recommends fixes to proactively strengthen security posture.
How we are different
- Unified Platform: Combines various security functions into a single platform, reducing complexity and improving manageability.
- Advanced Threat Intelligence: Leverages insights from Microsoft's extensive security research and global threat monitoring to stay ahead of emerging threats.
- Scalability: Designed to protect enterprises of all sizes, offering robust features suitable for diverse organizational needs.
- Continuous Improvement: Regularly updates with new features and improvements, ensuring that the platform evolves to meet the changing threat landscape.


