Photo Gallery
 |

 |
Moule Network Technology Co.,Ltd -------Bugbank


Additional Info
| Company | Moule Network Technology Co.,Ltd |
| Company size | 50 - 99 employees |
| World Region | Asia |
| Website | http://www.bugbank.cn |
NOMINATION HIGHLIGHTS
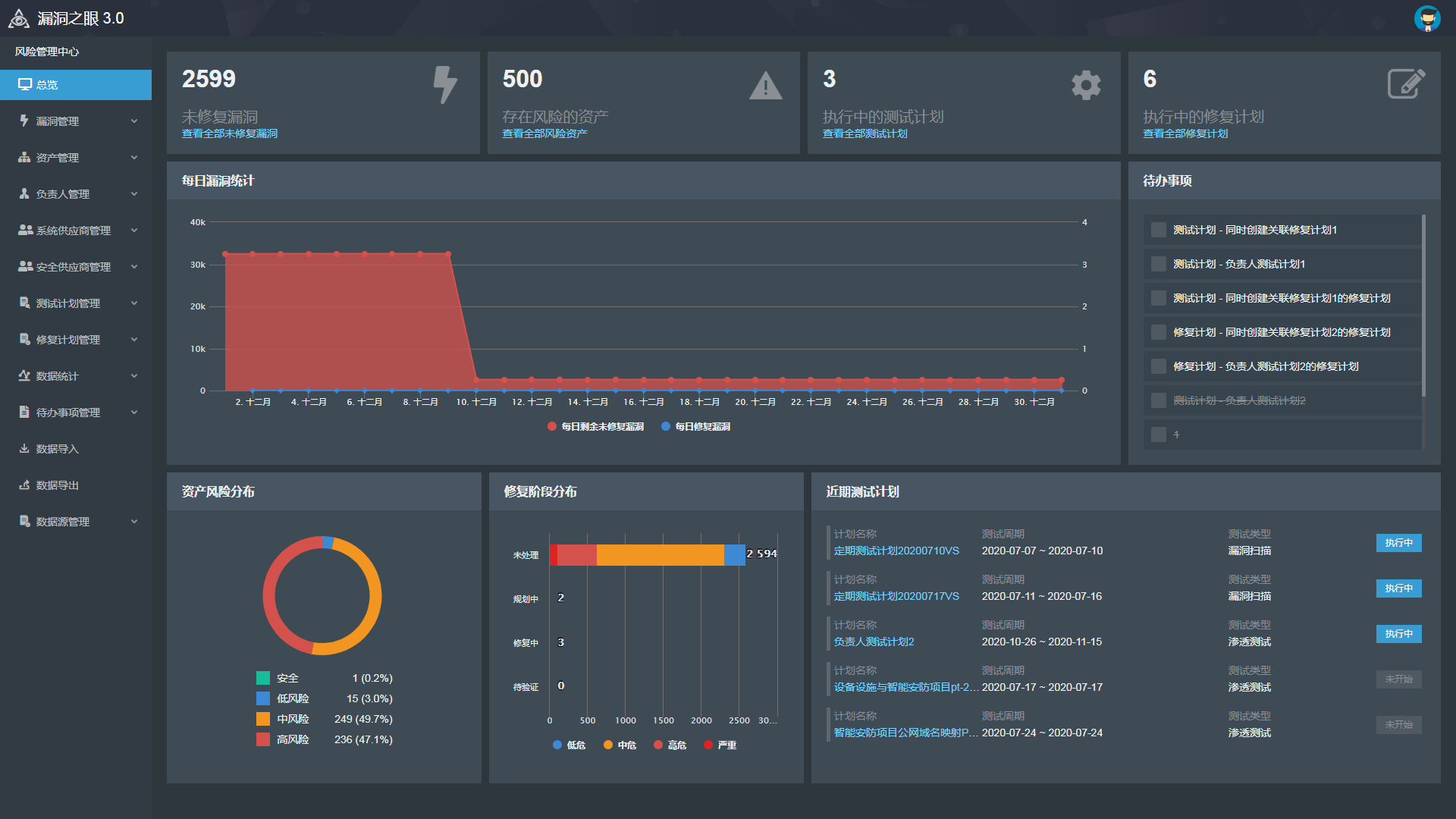
Our pruduct “Bugeyes” refers to the next-generation vulnerability management system and builds a new generation of vulnerability diagnosis and vulnerability full-life management platform based on the OWASP-TRM risk model. Bugeyes contains discovery of zero day exploits, passive scanning, automated detection, joint diagnosis and many other functions. It helps enterprises to detect assets in the network and improve the vulnerability detection. Bugeyes can help users to improve the risk management of their information system and complete the vulnerability full-life management through the tasks of discovery, diagnosis and processing. Through Bugeyes, enterprises can invest less manpower and financial resources to obtain more professional and comprehensive cybersecurity services.
Now, the analysis technology of our product “Bugeyes” has cooperated with universities and obtained more than ten patent certifications.Lower risk, higher efficiency, and more comprehensive testing make this product widely recognized by the market and many domestic and overseas authorities. Our product won the gold award of global excellence issued by the Infosecurity institution in 2019 and the winner of 2019 cybersecurity excellence awards.
How we are different
1. "Bugeyes" has three core innovative technologies, including joint vulnerability diagnosis , mirror test target machine and automatic threat disposal.
Bugeyes provides AI vulnerability detection engine and systematic vulnerability discovery engine using the joint vulnerability diagnosis which combines AI detection technology with human expert. This technology significantly improves the ability to discover vulnerability. The joint vulnerability diagnosis also uses passive detection technology to greatly increase detection coverage and achieves the best capability of vulnerability discovery.
The mirror test target machine is based on the real digital assets of the organization and automatically reproduces and generates a set of testing environments and systems used for safety testing.This mirroring system automatically handles risks in order to protect back-end data and prevent damage to the real environment.Meanwhile, the system implements penetration test audits throughout the entire process to ensure risk control during the testing process.
Automatic threat disposal can connect all security devices with the vulnerability management platform and intelligently dispose threats according to the risk level and the importance of assets. Then it can generate automated virtual patch and link with security devices to achieve dynamic defense.It does not require organizations to deal with vulnerabilities and threats frequently. It can compensate for system vulnerabilities and achieves automatic dynamic defense intelligently.
2. Our product Bugeyes completely solves the problem of exposing the testing target. Compared with the original detection, our product Bugeyes increases the speed of vulnerability detection by 50% and expands the testing coverage by 30%. It solves the problem of exposing the testing target and obtains more than ten patent certifications. For example, our product has been certified by three public security institutes (enhanced level), only ten of which are owned by the whole country and won the International award “2018 Global Excellence Awards” issued by Info Security Products Guide.
3. Lower risk, higher efficiency and more comprehensive testing make this product widely recognized by the market and many domestic and overseas authorities. Bugeyes has become an effective solution for application system security with its convenient management and configuration, comprehensive vulnerability diagnosis capability and multi-environment adaptability. Now it has been widely used in many fields, including government, universities, finance, e-commerce and other industries. It has gradually become an indispensable security product for institutions.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



