Noetic Continuous Cyber Asset Management and Controls platform
Recognized in the Category:
Photo Gallery
 |
 |
Noetic Continuous Cyber Asset Management and Controls platform

Additional Info
| Company | Noetic Cyber |
| Company size | 10 - 49 employees |
| Website | http://www.noeticcyber.com |
NOMINATION HIGHLIGHTS
The Noetic platform is a Continuous Cyber Asset Management and Controls Platform, a modern, cloud-native solution that is designed to continuously discover, inventory, enrich and remediate assets based on their attributes, configurations, relationships, and behaviors. The platform is built using graph database technology, which allows security analysts to understand the relationships between different assets and look at business criticality, context, and potential risk to help prioritize the workload.
The Noetic solution maps assets and business context in a temporal model that allows security teams to understand their current state, model their desired state using internal controls or industry frameworks and build automated workflows to continuously assess, report and remediate unsecure assets, non-compliant applications, or misconfigured cloud services. By correlating insights from existing tools, the Noetic platform can:
• Help security teams make faster, more accurate decisions. The context and insights provided help improve security posture accuracy and remediation.
• Leverage existing investments – pre-built, customizable connectors generate insights from existing IT management and security tools, without requiring additional agents on the endpoint.
• Deliver rapid time-to-value. Operationalize your data to close security gaps in days, not months.
How we are different
1. Noetic has based our cybersecurity asset management approach around an innovative graph database model. This delivers significant benefits to our customers. We are aggregating and correlating data from existing security and IT management tools into the graph, building an abstract model where each asset is a ‘node’ in the graph, and the cyber relationship between assets are ‘edges’ in the graph. This allows us to think like an attacker, moving laterally between assets and understand and visualize the multi-dimensional relationship between them. We don’t just include security information, but also business context from the CMDB, ERP, HR and other systems, supplying critical insights. Understanding which internet-facing machines have critical vulnerabilities is important but knowing if they support a share price-affecting application is vital to the business.
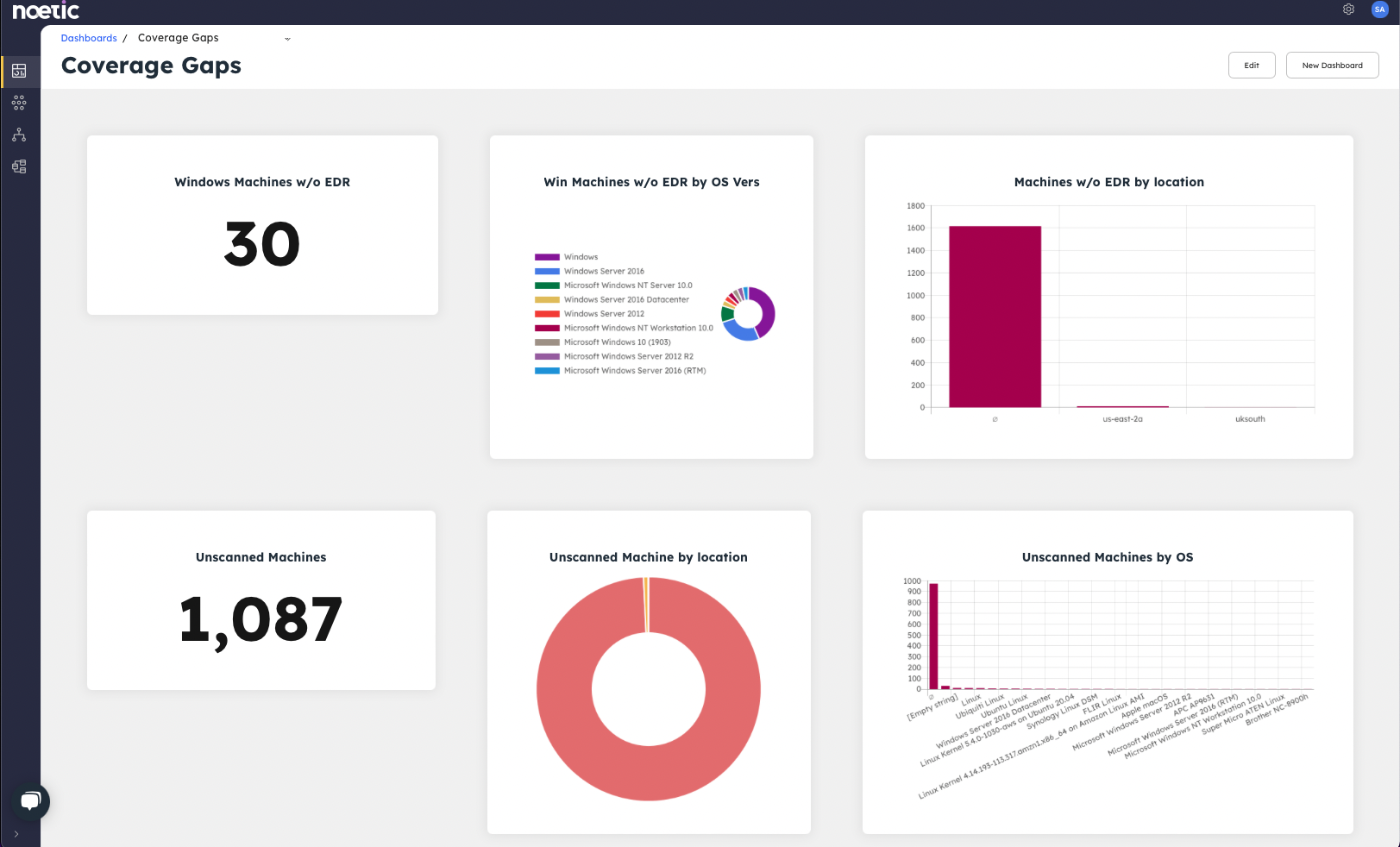
2. We have adopted an API aggregation approach to working with existing data sources. Based on the OpenAPI industry standard, we can connect with any cloud service or on-premises application to ingest information on assets and their relationships. These Noetic connectors are easy to create, extend and deploy. They also provide immediate value for security teams as we package them with common queries, automated workflows and dashboards to generate specific results, such as coverage gaps and common security violations.
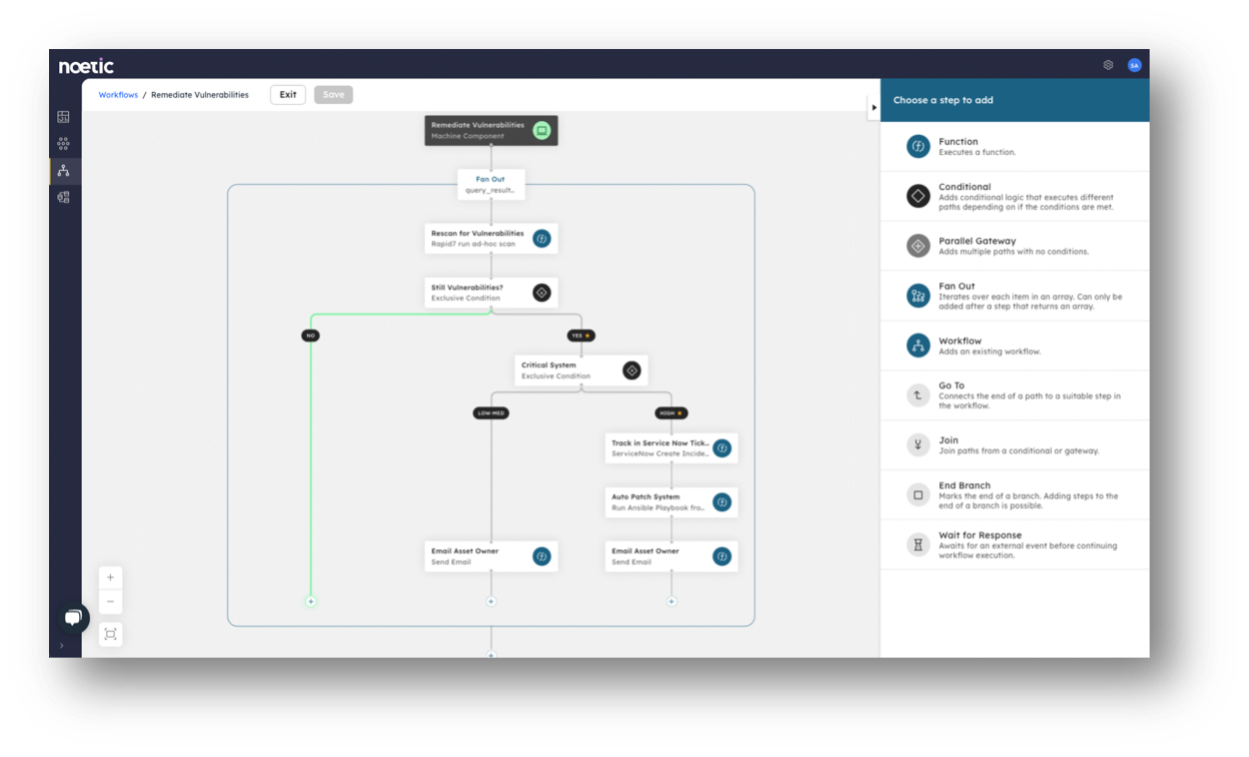
3. The Noetic platform has automation at its core. Our founding team’s background in pioneering the SOAR market is reflected in our approach to CAASM. Noetic has a comprehensive, easy to use automation and workflow engine that enables security analysts to save and schedule their queries and build out the right automation to restore out-of-policy assets to their desired state. This could include raising a ticket in an ITSM tool, triggering the deployment of a required security agent, or tapping into an existing vulnerability management or Infrastructure as Code process.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



