Photo Gallery
 |
 |
Onward Security HERCULES SecFlow

Additional Info
| Company | Onward Security |
| Company size | 50 - 99 employees |
| Website | https://www.onwardsecurity.com/ |
NOMINATION HIGHLIGHTS
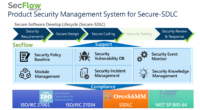
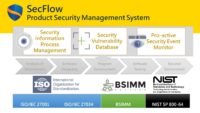
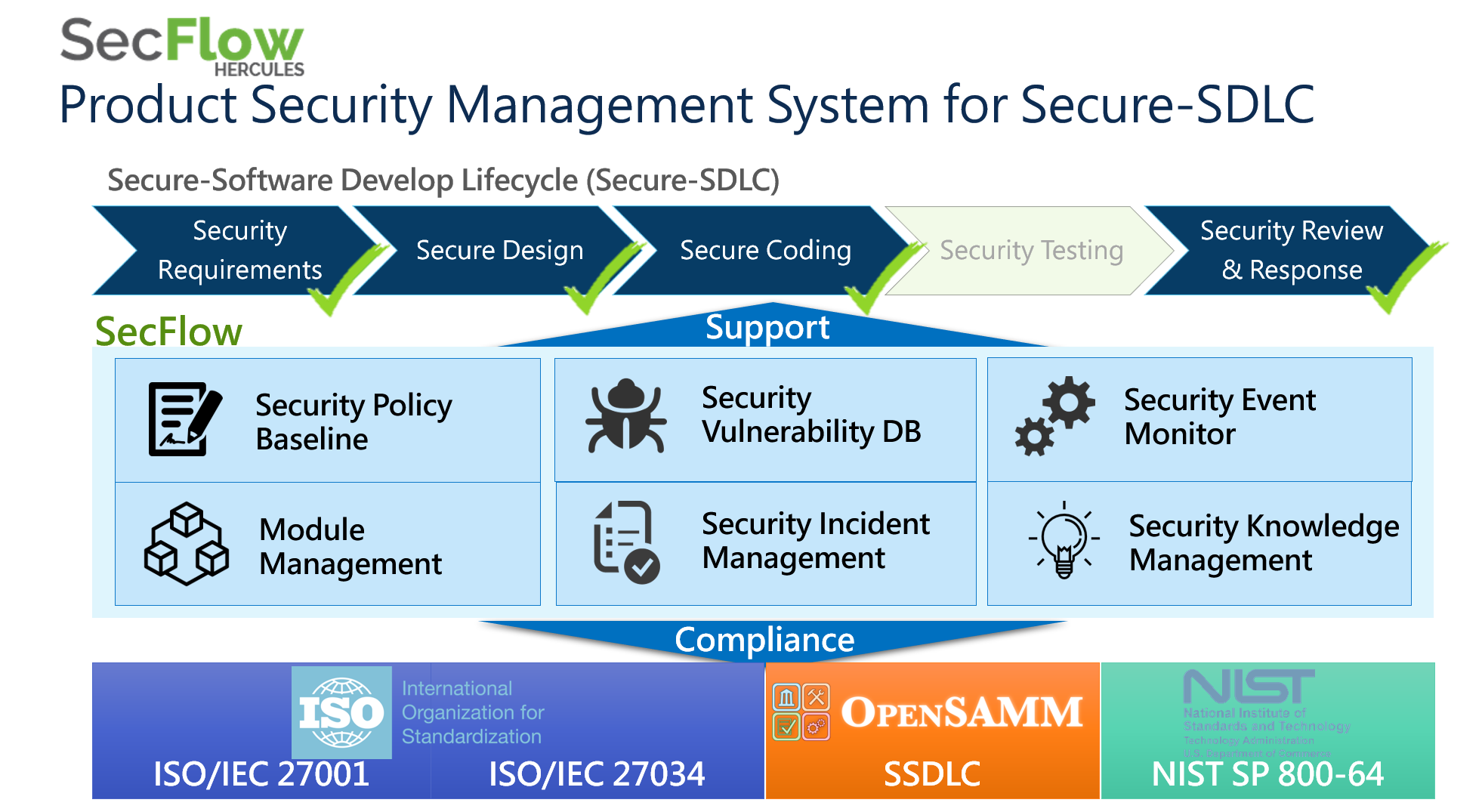
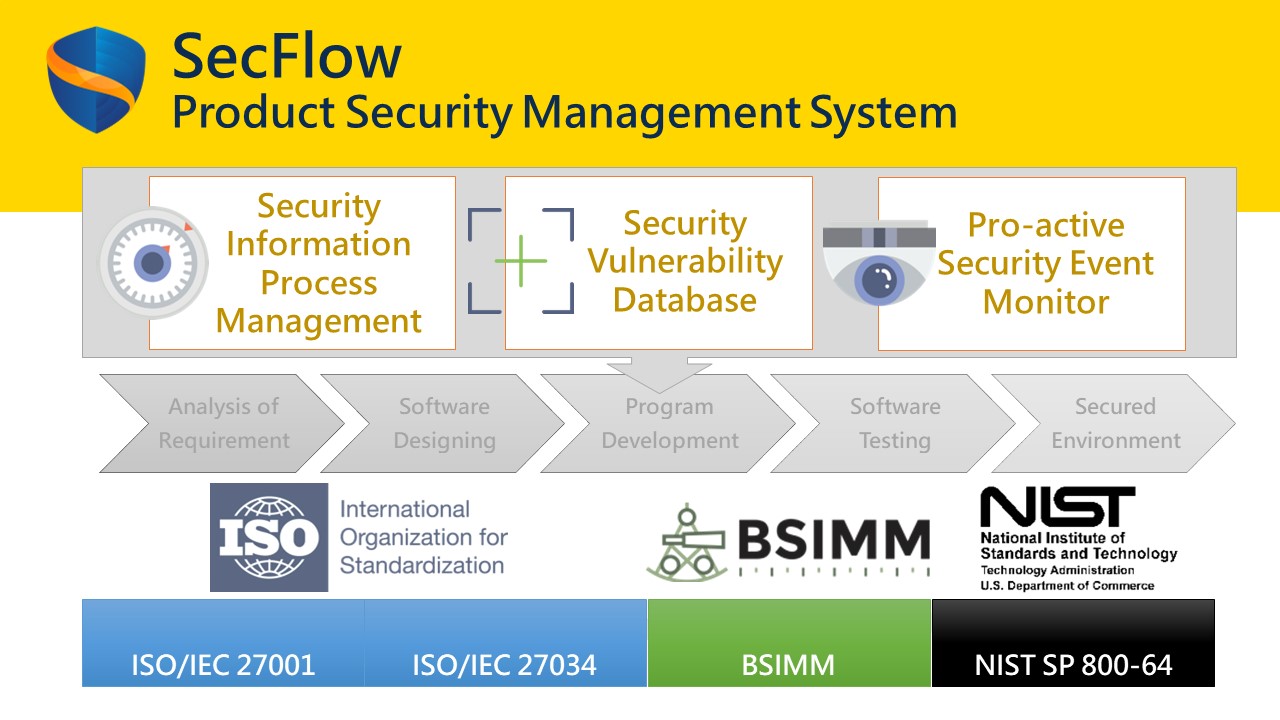
HERCULES SecFlow is a leading security management platform, providing security information process management, comprehensive security vulnerability database, and pro-active security event monitor.
The system of HERCULES SecFlow can be applied in the following four phases of Secure Software Development Lifecycle (SSDLC); Design, Implementation, Testing, and Maintenance. Design phase covers the security issue to inspect the requirement and compliance of security, and the risk model of this phase is used to verify the integrity of the security test plan. Implementation supports the relevant security development to follow the guideline and ensure the correct implementation is used. Testing focuses on multiple security testing to ensure the safety of products. The last phase, Maintenance, includes incident notification, proactive notification, and incident tracking. The four phases applied in the system of HERCULES SecFlow assist the team to integrate security development process and adopt SSDLC.
The development team applies HERCULES SecFlow with SSDLC to obtain the vulnerability information and solve product security issues effectively. HERCULES SecFlow helps the development team establishes the software security development process to comply with the requirement and compliance of security, including ISO27001, ISO27034, IEC62443, OpenSAMM, and NIST SP800-64 standard.
HERCULES SecFlow will update the built-in CVE and Non-CVE vulnerability information automatically and regularly to ensure that the other is up-to-date for users. The proactive notification mechanism provides the latest vulnerability and a security issue for users and filters out the information that users concern via E-mail notification by adopting advanced technology for data collection.
The intelligent technology of the security management system combines vulnerability database, security issue, and incident analysis of the product, which allows developers to respond to issue immediately, reduce the risk of the incident and minimize the impact on the enterprise.
How we are different
- User Behavior Learning and adaptive Feature
SecFlow uses machine learning and statistical analysis techniques to understand the information that users are interested in, staying time of particular contents, the user-defined condition, and other operation behaviors. Based on the above features, SecFlow automatically adjusts and optimizes the Notification Service to assist the clients in evaluating the priority of incidents for allocating the resource to process the most important issues. Through the relevant analysis mechanism, the Notification Service provides "Additional Suggestion Context" to predict the potential information that has not been subscribed by customers. In addition, this feature reduces the potential security risks and maximizes the effectiveness of security.
- Security Vulnerability Information and Solution
The security vulnerability database of HERCULES SecFlow is comprehensive and abundant, which contains a wide range of vulnerability information and over 120,000 vulnerabilities, including CVE and Non-CVE vulnerabilities. SecFlow adopts the daily collection and analysis mechanism to ensure that the vulnerability information is up-to-date. In addition, the system provides first-hand information to assist the user in handling the incident and controlling losses by comparing the product specification with the above vulnerabilities.
- Pro-active Security Event Monitor
The intelligent technology of HERCULES SecFlow collects international security issues and provides customized notifications and reports about the latest vulnerabilities for users. Additionally, HERCULES SecFlow allows users to receive the notification in real-time through E-mail notification so users can respond to the security event immediately. The notification contains incident detection, recommendation, and solution, which improves incident response time and decreases the impact of a breach.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



