Ordr Platform — Discover every connected device (IoT, IoMT, OT), analyze behavior and automate action
Recognized in the Category:
Photo Gallery
 |

 |
Ordr Platform -- Discover every connected device (IoT, IoMT, OT), analyze behavior and automate action

Additional Info
| Company | Ordr |
| Company size | 50 - 99 employees |
| Website | http://www.ordr.net |
NOMINATION HIGHLIGHTS
Across all industries, unmanaged IoT and IoMT devices are a significant part of the network ecosystem. In Ordr’s recent Rise of the Machine report, 5 million unmanaged, IoT and IoMT devices were analyzed — ranging from consumer devices like Smart Speakers (ie. Amazon Alexa, Google Home, etc.) to MRIs and infusion pumps. Many of these devices provide mission-critical business operations and even life-saving services, but if not properly managed and secured, can also pose unique security challenges.
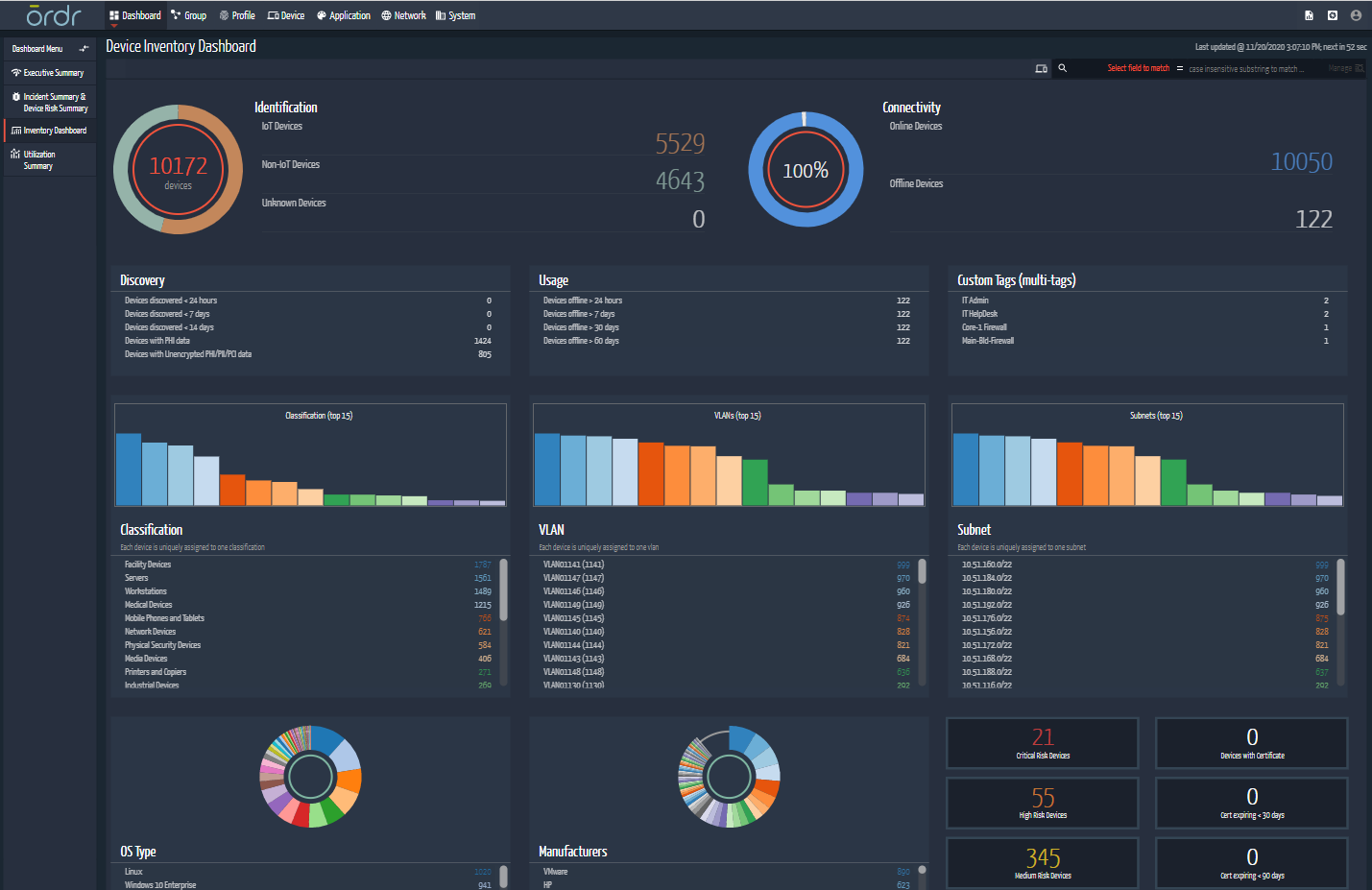
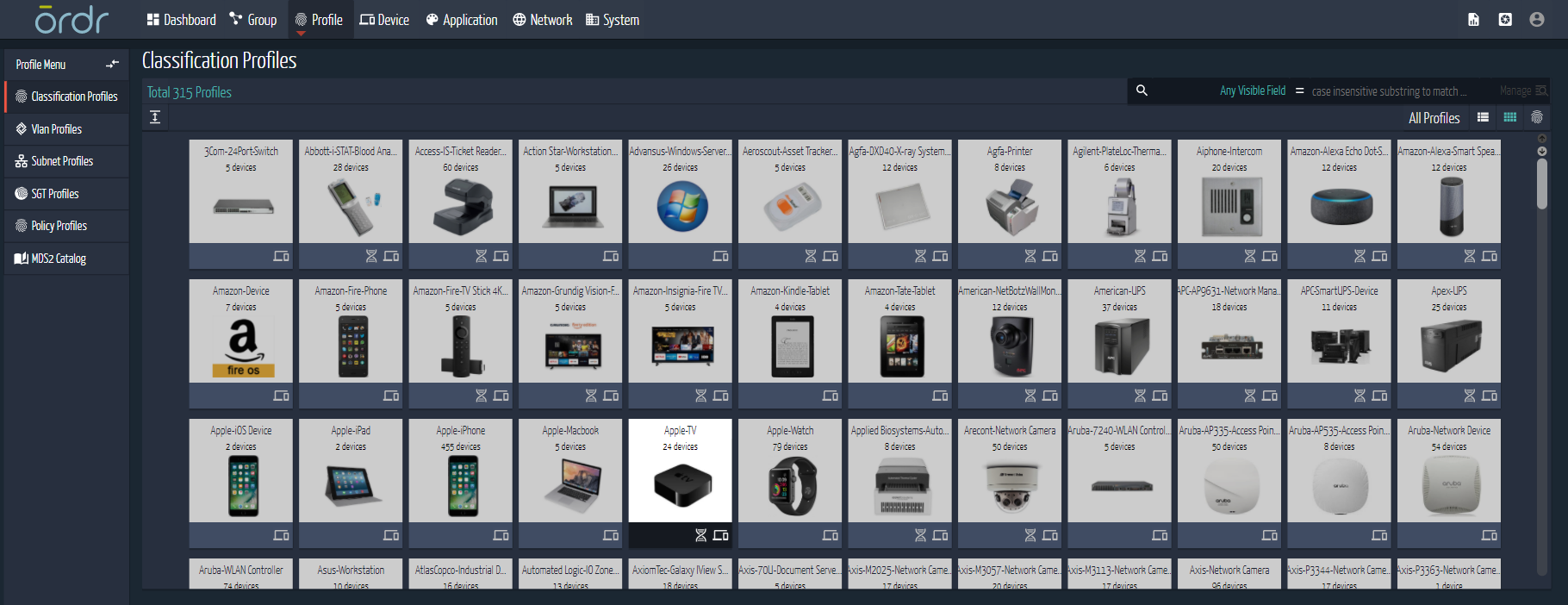
Within a few hours of deployment in an enterprise — via network tap or SPAN — the Ordr Platform discovers high-fidelity information about every connected device including make, location, serial number, and application/port usage. Enterprises can evaluate vulnerabilities, discover recalled products on the network, identify weak passwords and weak certificates on every device.
Next Ordr uses advanced machine learning to map device communications patterns and behaviors at a granular level. These communications patterns allow security and networking teams to visualize device flows within their networking architecture, baseline normal behavior, and identify anomalous or suspicious behaviors. Ordr provides complete visualization of device communications and show what internal or external entities device profiles are communicating with.
Finally, Ordr does not simply showcase the problem — it provides actionable responses to secure an organization. Ordr allows organizations to baseline device communications and then automatically creates Zero Trust segmentation policies to only allow sanctioned communications for every device profile. This is a critical approach to manage the hundreds of thousands of unmanaged and IoT device that can exist in organizations today. Ordr can also integrate into existing incident response and event management, or asset inventory workflows. Ordr’s deep 3rd party integrations provides the ability to enforce these policies on any security or networking infrastructure in the organization; these include next-generation firewalls, network access controls, wireless LAN controllers, IT Services Management, Network Access Control, Security Information and Event Management, and Configuration Management Database solutions.
The unique capabilities of the Ordr platform have resulted in many awards (SINET 2020, KLAS 2020 Healthcare IoT, CRN Most Innovative Startup and more), in addition to proven RoI for customers. A healthcare organization used the Ordr Flow Genome to profile device behavior and baseline communications. Ordr detected medical devices communicating to Russia. In a LifeScience organization, Ordr found 7,000 IoT devices running Windows 7, an obsolete operating system with known vulnerabilities. Ordr was able to proactively segment these devices. Over a 7-year period, a manufacturing organization was only able to gain visibility into 20% of their environment. Ordr was able to deliver comprehensive asset inventory for NAC.
How we are different
Ordr is the industry’s most comprehensive platform to secure all connected devices including unmanaged, IoT, OT and IoMT devices – discovery and classification, risk identification and automated action. We differentiate in the following areas:
- Real-time visibility for every connected device: Within a few hours of deployment – via a network tap or SPAN – Ordr automatically discovers high-fidelity information about every connected device, including make, classification, location, and application/port usage. This visibility is provided in real-time for any connected device. The Ordr deployment is agentless, zero touch and has no impact to the device or the environment.
- Comprehensive understanding of device behavior and risks: Ordr identifies security issues and risks that may impact devices -- vulnerabilities, FDA recalls, manufacturing recalls, weak ciphers and certificates. Risk scores and prioritization are provided. Ordr also fully maps every device communication pattern using advanced machine learning. This unique capablity, called the Ordr Flow Genome enables customers to establish a baseline so that identifying suspicious and anomalous behaviors, such as new communications to a malicious command and control, or to a new country, is automated.
- Automate action on existing security and networking infrastructure: Ordr does not simply showcase the problem -- it provides actionable responses to secure an organization. Using Ordr Flow Genome and understanding of device behavior, customers can dynamically create policies for every single device profile to only allow “sanctioned communications” critical to its role. This is important because unlike user communications, unmanaged, IoT, OT, and IoMT devices should only have specific patterns of behavior. Ordr dynamically generates these Zero Trust policies and can enforce them on existing infrastructure such as switches, firewalls, wireless LAN controllers, and more.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



