Photo Gallery
|

|
Perimeter 81: Zero Trust Secure Network as a Service


Additional Info
| Company | Perimeter 81 |
| Company size | 100 - 499 employees |
| Website | http://www.perimeter81.com |
NOMINATION HIGHLIGHTS
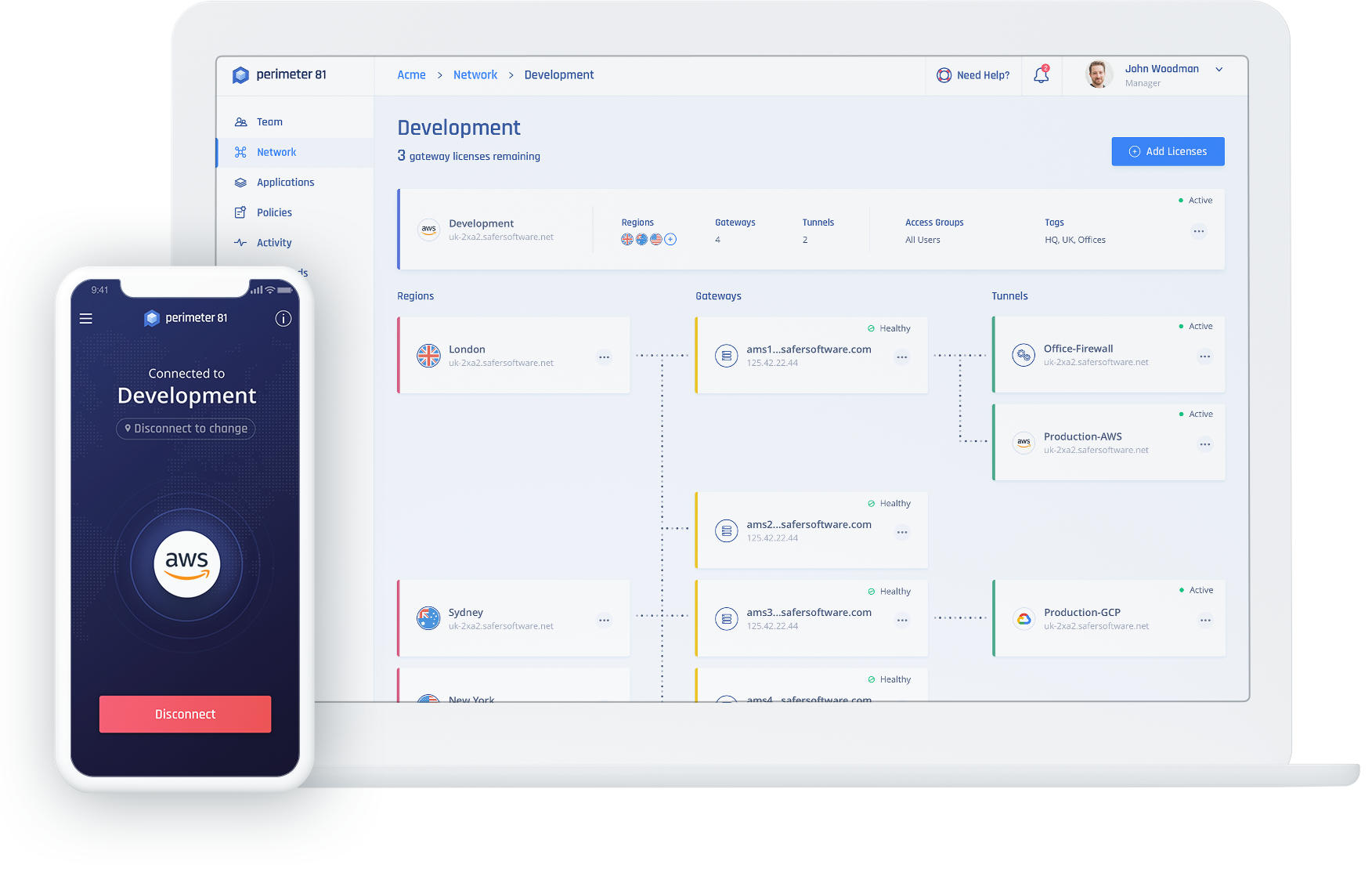
Perimeter 81 is simplifying network security for the modern and distributed workforce by transforming the outdated, complex, hardware-based network security technologies of the past into one unified, easy-to-use and scalable software solution. As a holistic SaaS solution providing customizable networking and the highest levels of security in the cloud, Perimeter 81 is revolutionizing the way organizations consume network security. We have built a solution that gives companies of all industries and sizes the power to be securely mobile and completely cloud-confident in this age of remote work and cloud transformation.
Our platform combines network and security functions into one unified network security service solution that adheres to the SASE (Secure Access Service Edge) Model. The network and endpoint security solutions managed and delivered through the Perimeter 81 platform provide user-centric network and granular policy management for organizations of all sizes.
Perimeter 81’s Zero Trust Network Access (ZTNA) provides policy enforcement and protection by isolating applications and segmenting network access based on user permissions, authentication, and verification. The platform’s comprehensive software-defined perimeter (SDP) solution offers simple cloud migration security, seamless least privilege access to resources and secured access to cloud environments including IaaS and PaaS.
For complete endpoint security, Perimeter 81 delivers multiple endpoint protection capabilities, including WiFi protection, next-generation malware protection and support for visibility into encrypted traffic. With endpoint compliance, Perimeter 81 scans for security feature updates including Firewalls, Antivirus, Windows patches and malware for a more secure network and threat-free network.
Our microservice infrastructure allows us to provide our clients with a highly scalable solution. Meanwhile, our zero-touch and user-friendly SaaS subscription approach eliminates the dependency on long sales cycles. Clients can create and set up their networks in a matter of minutes, connecting to the internal cloud and on-premises resources without requiring any external assistance.
How we are different
- Intuitive UX/UI and Ease-of-Use: Our single-click, highly intuitive interface allows clients to create and set up their networks as well as onboard team members, without requiring any external assistance. Originally coming from a B2C background, we have learned how to design a single-click product for the end-user, ensuring seamless product adoption. Over 40% of our customers are no-touch and completely DIY and can even service small organizations with no CISO or IT manager.
- Network Infrastructure: The competition offers a partial solution to securing the perimeter. We provide a global gateway backbone for deploying security and resources to the edge, and with our Software-Defined Perimeter model, allow easy integration with all local and cloud resources. Customers typically set up their organizations' networks in as little as 15 minutes, and then enjoy total visibility via a thorough variety of segmentation and custom access tools in the cloud. This multi-tenant cloud-based network infrastructure represents the ultimate one-stop shop cyber security platform.
- Pricing and Scalability: Our pricing is extremely competitive and the deployment, scalability, and on-boarding of our product is seamless and fast. As a SaaS solution with no manual configuration or hardware involved, our customers can easily onboard to the platform, deploy their entire network automatically, and scale as they grow. Our cost-effective solution allows clients to “land and expand” by starting off with a minimum of 5 users and growing to an unlimited number of users. Our flexible subscription model is tailored to the number of users, networks and gateways. IT managers can lighten their burden by instantly scaling up a network and onboarding new users, rules, and policies. As opposed to many of our competitors, we operate a global network of over 50 data centers, and are responsible for all maintenance and patching.


