Photo Gallery
 |
 |
Picus Security

Additional Info
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | http://www.picussecurity.com |
NOMINATION HIGHLIGHTS
Picus Security helps security teams of all sizes to continuously validate and enhance organizations’ cyber resilience.
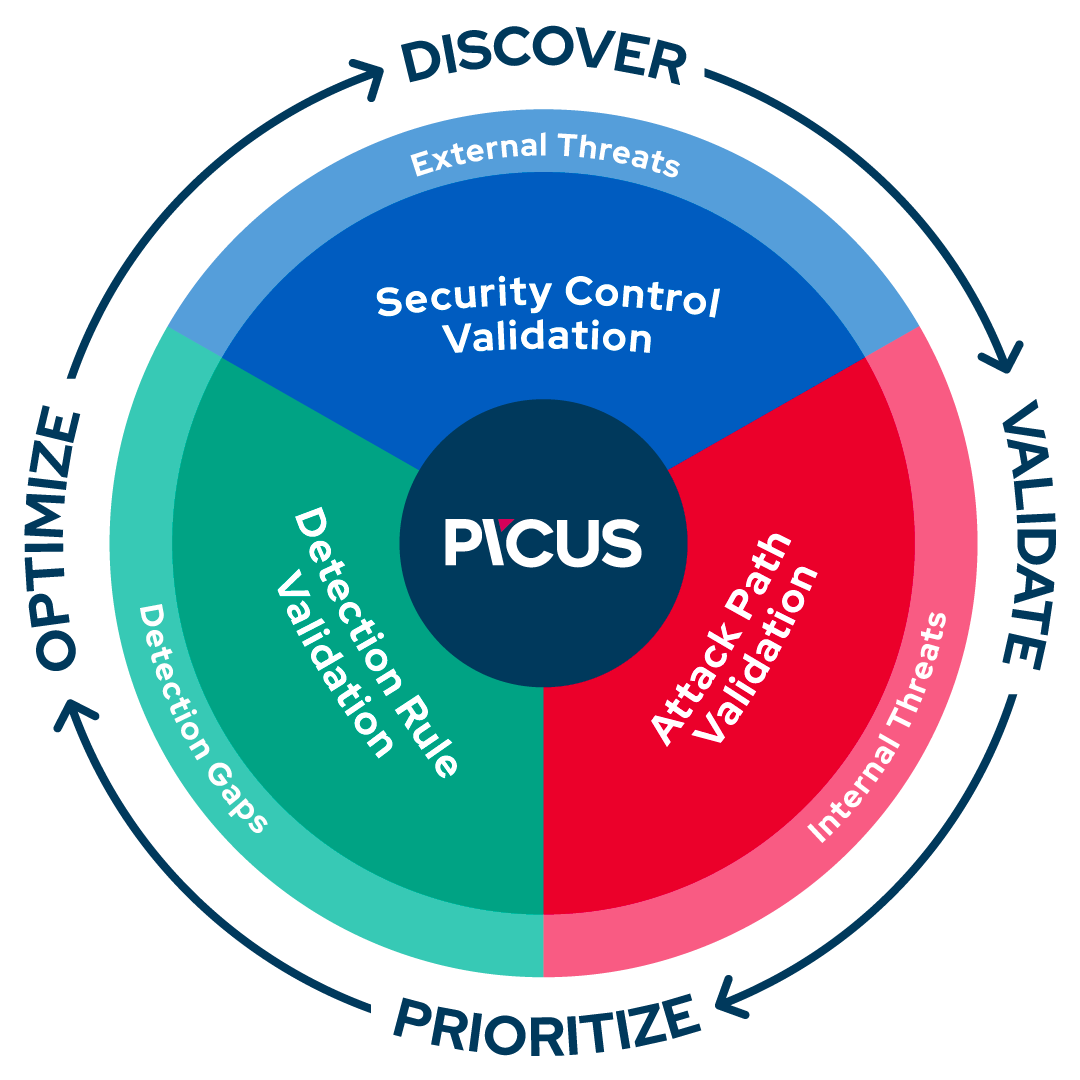
Our Complete Security Validation Platform simulates real-world threats to automatically evaluate the effectiveness of security controls, identify high-risk attack paths to critical assets, and optimize threat prevention and detection capabilities.
As the pioneer of Breach and Attack Simulation, we specialize in supplying the actionable insights our customers need to be threat-centric and proactive.
Via our online Purple Academy, we give back to the community by providing free training about the latest offensive and defensive security approaches.
How we are different
Picus Security is the pioneer of Breach and Attack Simulation and is now taking it to the next level.
• Picus believes that security validation should be performed by every organization and strives to make this process as simple and convenient as possible. Unlike other products that are complex and time-consuming to use, The Picus Complete Security Validation Platform is quick to deploy, configure and manage. Being modular, it offers the flexibility organizations need to tailor the solution to different validation use cases.
• In the past 12 months, The Picus Platform’s validation capabilities have been extended beyond security control validation to help security teams validate other aspects of organizations’ security postures. The release of Attack Path Validation and Detection Rule Validation enables security teams to improve attack path management in internal networks and further optimize detection and response capabilities,
• Picus’ outcome focus means that we’re not only committed to helping organizations identify security risks but also to address them swiftly and effectively. Picus has an extensive range of technology alliance partners and we leverage our relationships to achieve a deeper level of validation and to supply actionable insights and recommendations about how to address security gaps.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



