Photo Gallery
 |
 |
Portshift Identity-Based Cloud Workload Protection

Additional Info
| Company | Portshift |
| Company size | 10 - 49 employees |
| Website | http://www.portshift.io |
NOMINATION HIGHLIGHTS
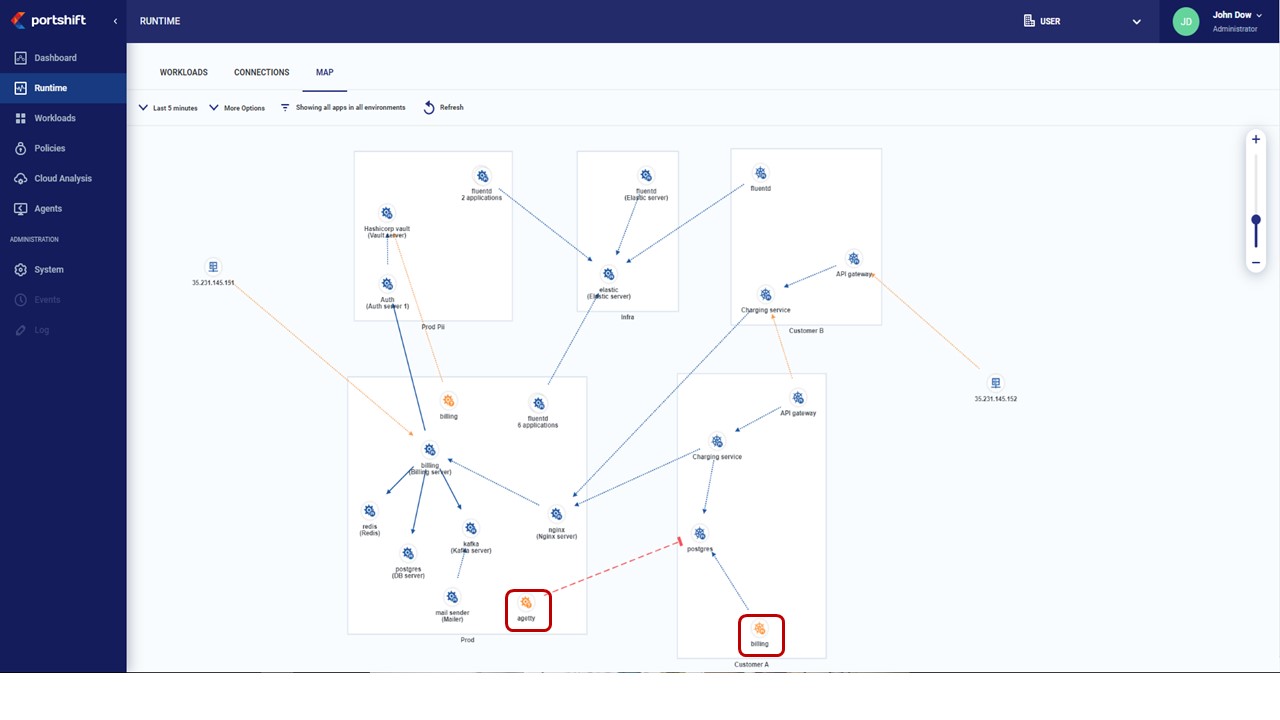
Portshift is an identity-based cloud workload protection platform that secures applications from CI/CD to runtime. Portshift enables organizations to know which applications are running on their cloud environments, to see and enforce how the applications communicate and to easily find information that is associated with their development and deployment cycles enabling DevOps teams to orchestrate security as part of their day-to-day job. Portshift’s unique model introduces a security framework that is decoupled from network and operations, allowing for accelerated software delivery at any scale. Portshift was spun out of think tank and company-builder Team8.
How we are different
1. Portshift addresses Kubernetes security challenges. Portshift seamlessly integrates with Kubernetes, and enables the delivery of continuous security for Kubernetes workloads, using identity based protection baked into the CI/CD pipeline. Combined with real-time visibility of Kubernetes containers and pods, and a robust policy enforcement tool, your entire Kubernetes pipeline is secured from code to runtime.
2. Portshift is a paradigm shift for application security using a zero-trust approach. Zero-Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters, and instead must verify anything and everything trying to connect to its systems before granting access. Zero-trust, in fact, addresses the threat of lateral movement within the network by leveraging micro-segmentation and granular perimeter enforcement.
3. Compliant container security. Enterprises moving operations to the cloud face more and more regulatory requirements to ensure the safety and privacy of data, and to protect against fraud and other threats. Containerization and microsegmentation are trends that contribute to data protection, while allowing for dynamic scalability of enterprise applications, as business needs require.
Portshift works seamlessly with this new environment, providing full visibility of all services (workloads) active in your environment, both known and unknown, and applying workload-based runtime policies to these workloads. You can now see instantly who is accessing sensitive data services, and identify (and isolate) anomalous, possibly malicious agents trying to penetrate your perimeters.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



