Photo Gallery
|


|
Proofpoint Browser Isolation


Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
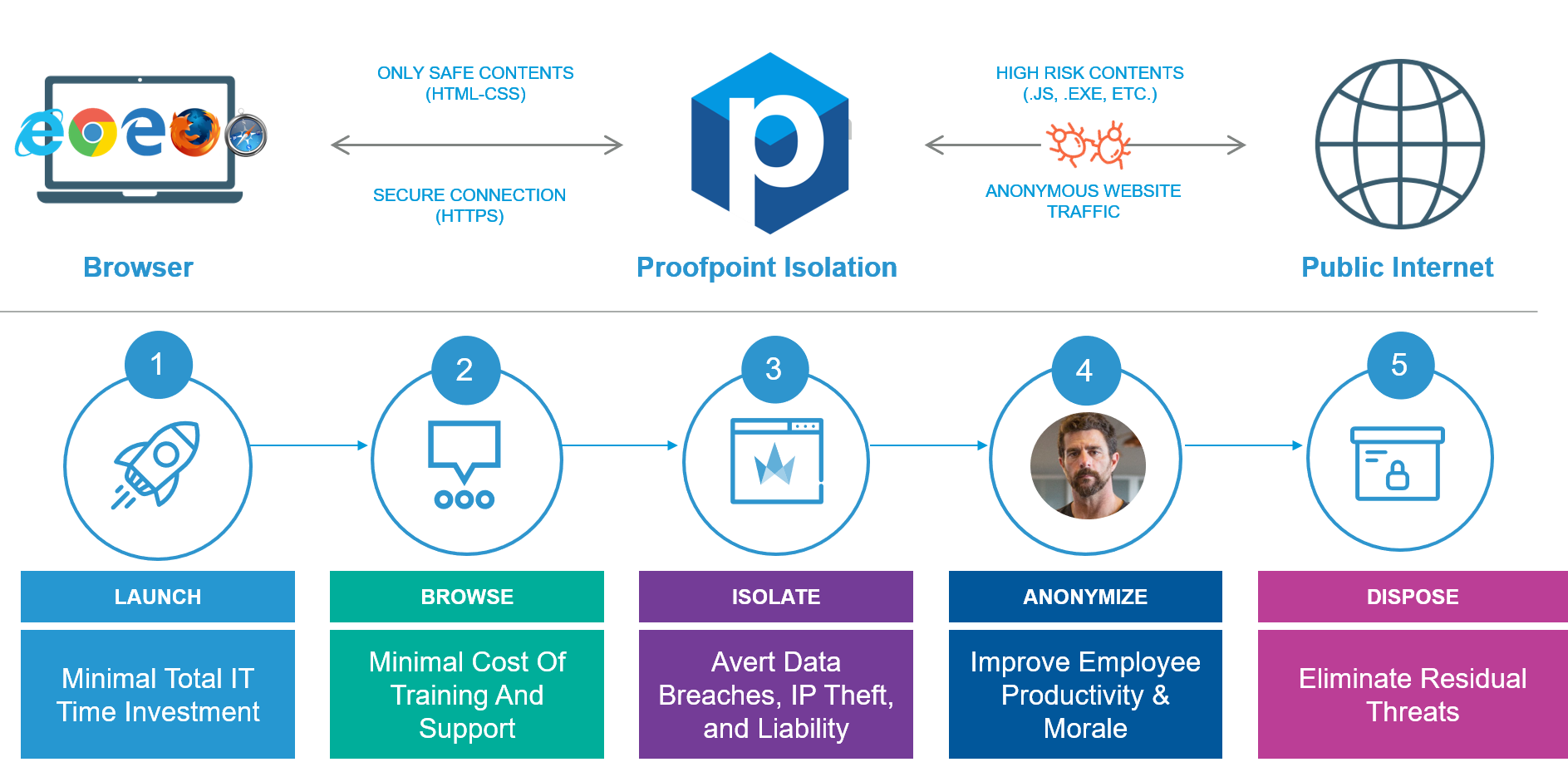
Proofpoint Browser Isolation lets your people freely access websites, personal email and corporate email without exposing your organization to malware and data loss. Drawing on threat intelligence from Proofpoint Targeted Attack Protection (TAP) it uses cloud-based isolation technology to reduce your attack surface and secure users’ web activity. Used with TAP, you can also isolate unknown and risky web links to stop URL-based threats. Browser Isolation renders browser sessions in a secure container to keep harmful content out of your environment. Users can view and interact with the web page as normal. But malware and other harmful content are removed from the page. Uploads, downloads and input forms are disabled to prevent data theft and loss. And our proprietary real-time anti-phishing scan analyses the site and automatically blocks further use of the page if it finds a threat.
Today’s attackers target people in your organization, often through phishing emails. Adaptive controls can help protect your riskiest users as threats evolve.
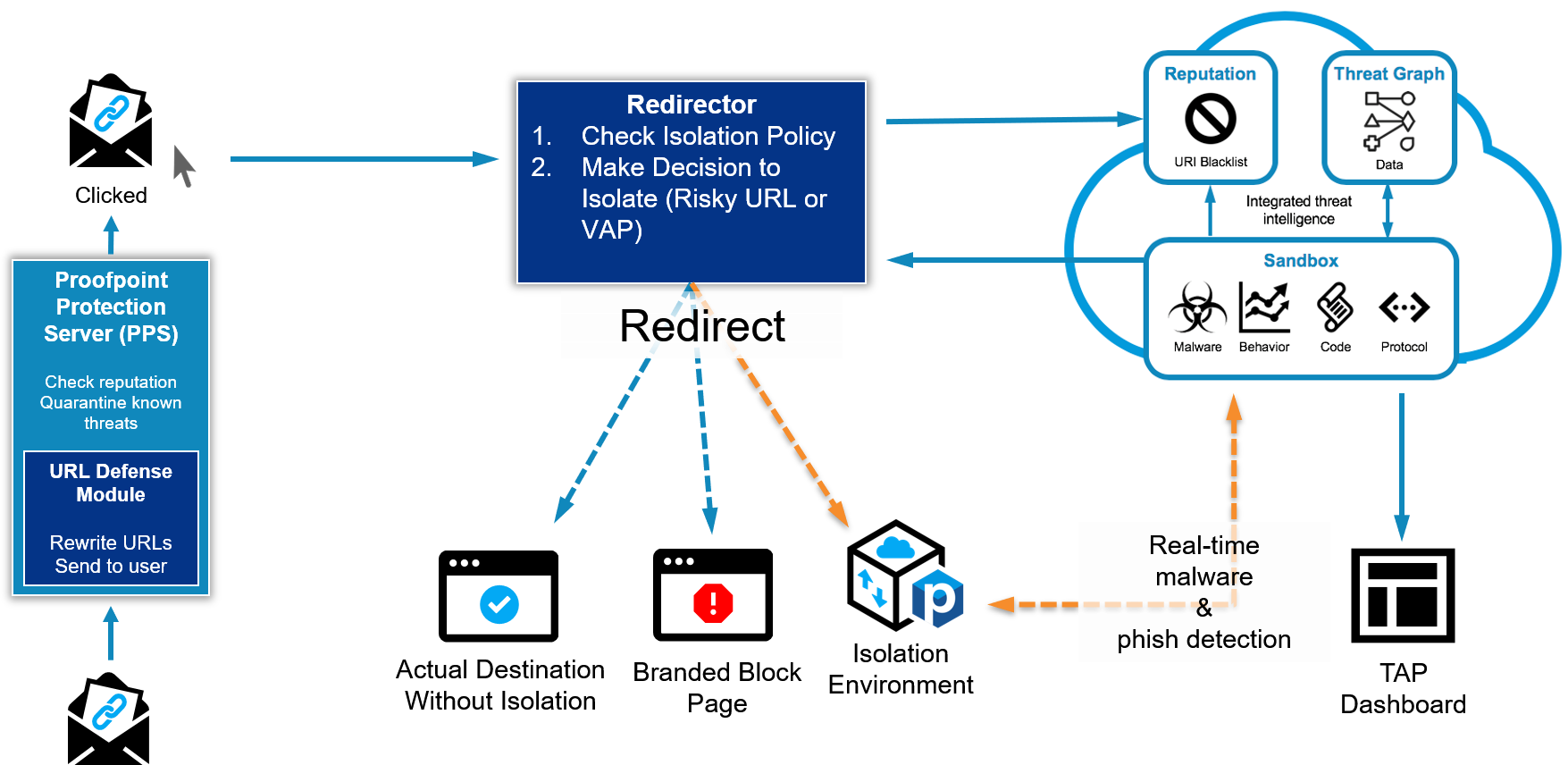
Browser Isolation protects against malicious web-based content in corporate email. Browsing sessions triggered by URLs in email are isolated automatically based on your policy. Through its integration with TAP, Browser Isolation can also isolate URLs in email sent to your riskiest users. You can apply isolation to corporate email users based any combination of risk factors. The integration also provides you with real-time phishing detection and scanning. When an isolated browser session is triggered, it’s reported to the TAP dashboard to unearth new threats and track risk. Integrating adaptive, people-centric controls and TAP is an effective way to lower risk.
How we are different
• Proofpoint’s TAP URL Isolation also gives you further ability to provide adaptive controls to help protect your very attacked people or VAPs by isolating suspicious content in patient zero scenarios.
• Proofpoint’s isolation leverages our integrated threat intelligence to defend against malicious URLs and safely removes any malicious content to view and print files in a safe manner.
• Proofpoint integrates seamlessly with any existing gateway solution and is deployed 100% in the cloud without requiring any additional hardware or endpoint agents.


