Proofpoint Cloud App Security Broker (CASB)
Recognized in the Category:
Photo Gallery
 |
 |
Proofpoint Cloud App Security Broker (CASB)

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
Proofpoint provides the only CASB to meet the needs of security people serious about SaaS threats, cloud data loss and SaaS app governance. Proofpoint CASB protects you from SaaS account takeover, oversharing of sensitive data and compliance risks in the cloud. Our multi-mode solution combines:
-Compromised account detection and automated response
-Protection against malicious files uploaded or created within SaaS apps
-Data security including real-time DLP
-SaaS and third-party apps governance including third-party OAuth apps
-IaaS protection
-Real-time detection of malicious files
-Adaptive access controls
-Controls over IT-approved and tolerated SaaS apps that are used in the browser or within native clients
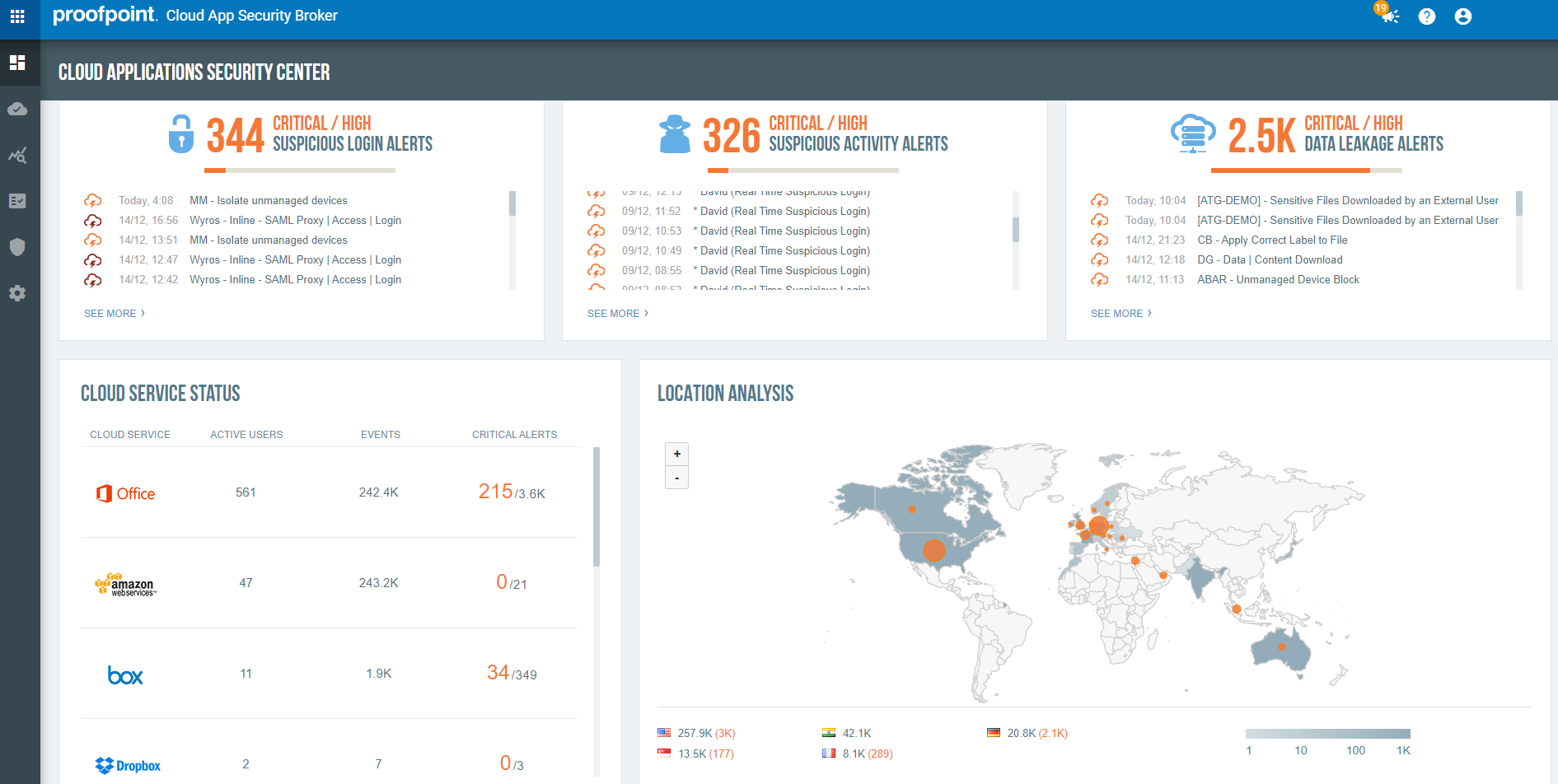
We secure Microsoft 365, Google Workspace, Salesforce, Box, Slack, Workday, Amazon Web Services (AWS), Microsoft Azure, Okta and hundreds more SaaS apps and IaaS services. People-centric visibility to email and cloud threats helps organizations identify at-risk users and protect their accounts and data.
With Proofpoint, organizations can deploy consistent DLP policies across cloud, email and endpoint. You can also centralize alert management across these channels on a single console. Our powerful analytics and adaptive controls help companies grant the right levels of access to users and third-party apps.
To protect your IaaS environments and ensure compliance, Proofpoint CASB IaaS Protection provides:
-IaaS discovery
-Cloud Security Posture Management (CSPM)
-Data security, including DLP for IaaS buckets and containers
-Threat protection, including cloud account compromise detection
-Adaptive access controls
With our IaaS Protection add-on module, you can:
-Identify misconfigurations in IaaS environments
-Monitor and control privileged user activity
-Discover all IaaS resources and un-provisioned IaaS accounts
-Discover sensitive data in cloud storage and remediate excessive sharing of buckets with sensitive data
-Prevent unauthorized access to IaaS environments
How we are different
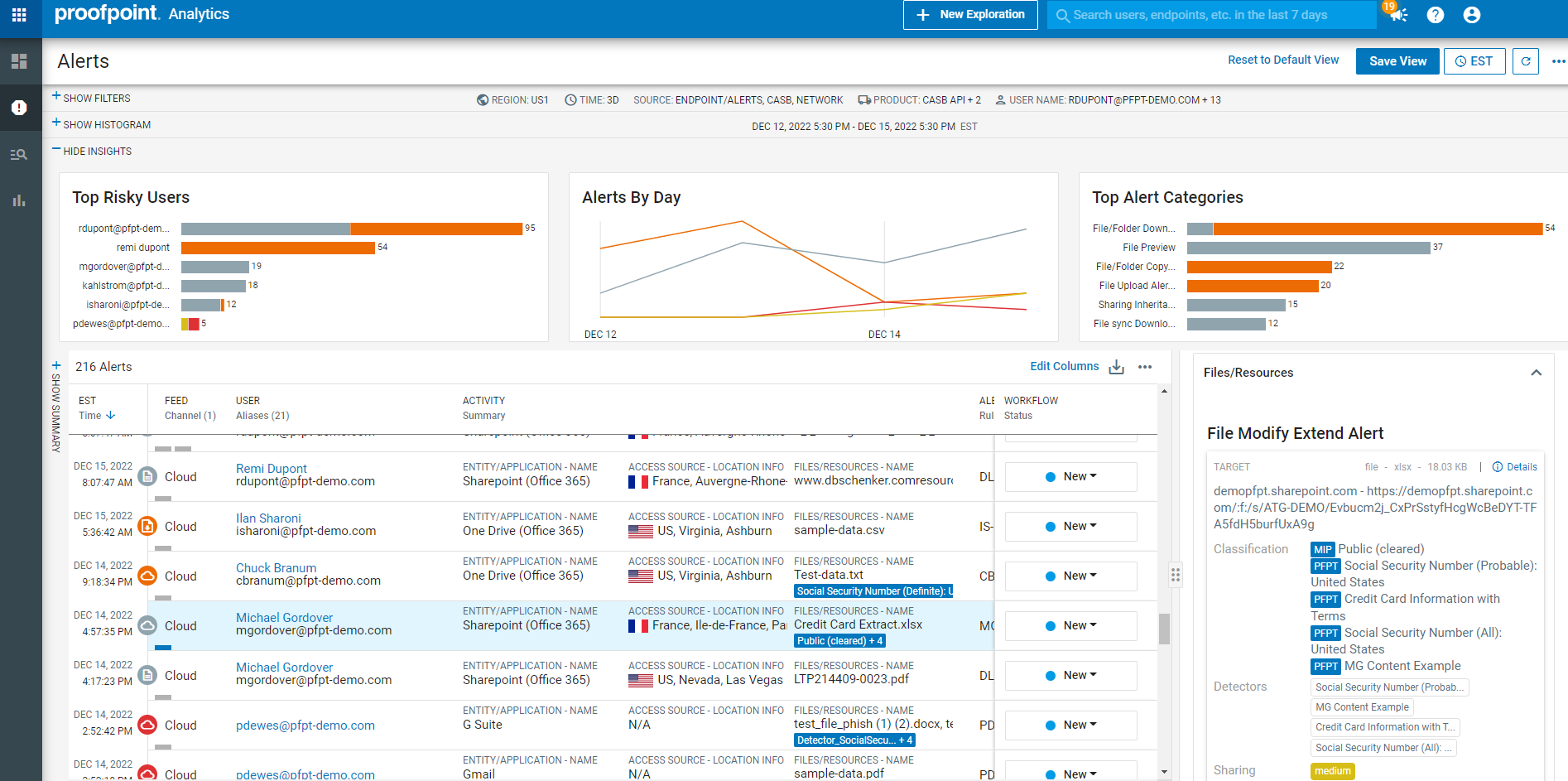
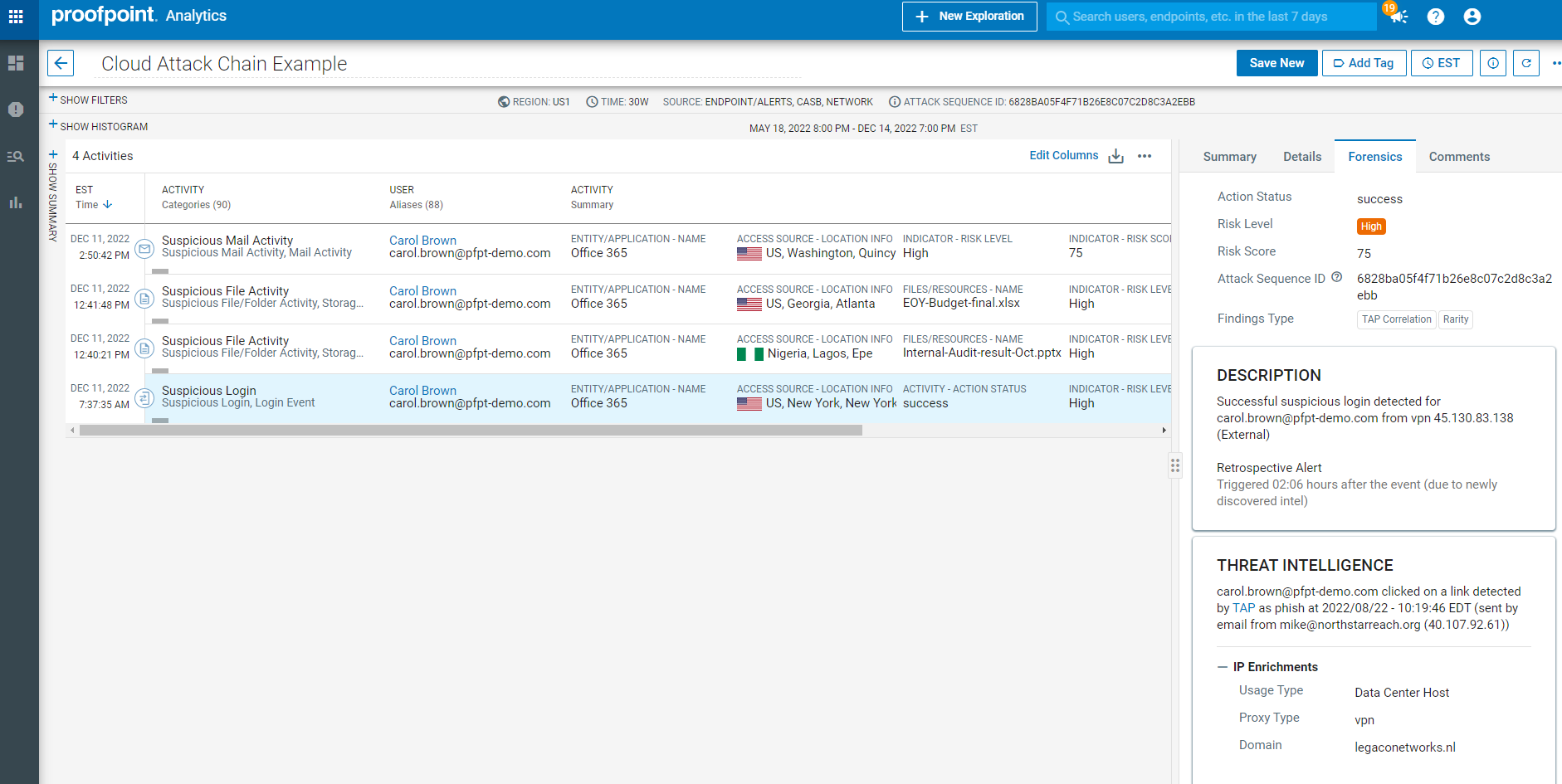
Proofpoint CASB is the only CASB that correlates threat intelligence across email to cloud phishing attempts, known threat infrastructure, prior credential dumps, and bruteforce campaigns. We correlate the entire cloud attack chain from email and initial access to the post-access activity in cloud and email apps within timeline and MITRE ATT&CK based views. This enables high-efficacy protection of users from SaaS account takeovers, preparation of cloud ransomware attacks, malicious apps and abuse of third-party OAuth app access. The results are faster time to value and zero gaps in security visibility.
Proofpoint provides the most consolidated platform to correlate telemetry on content, user-behavior and threats across DLP channels – cloud (SaaS and IaaS storage), email, endpoint and web. Data loss originates with people. They can be careless, compromised, or malicious. Understanding user intent enables you to apply the appropriate DLP response to mitigate risk. The results are greater return on investment compared to on-premise solutions, faster incident response compared to point solutions and better enabler of secure collaboration than with data-centric solutions.
With Proofpoint CASB, IT and security can more easily work together to discover and govern SaaS apps, third party OAuth apps, and IaaS services without complicated deployment models. In one view, customers can analyse their riskiest cloud services based on factors such as the most attacked or abused cloud services, those containing the most sensitive data, those accessed by the privileged users and the most vulnerable services. This includes first-party cloud apps (such as Microsoft OneDrive) as well as third-party OAuth apps (such as those in Google Workspace Marketplace and Microsoft AppSource through OAuth tokens). For our customers, Shadow IT is an area where IT and security teams collaborate easier than before. The results are fewer data leakages through unapproved sites and simplified compliance and executive reporting.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.


