Photo Gallery
|
|
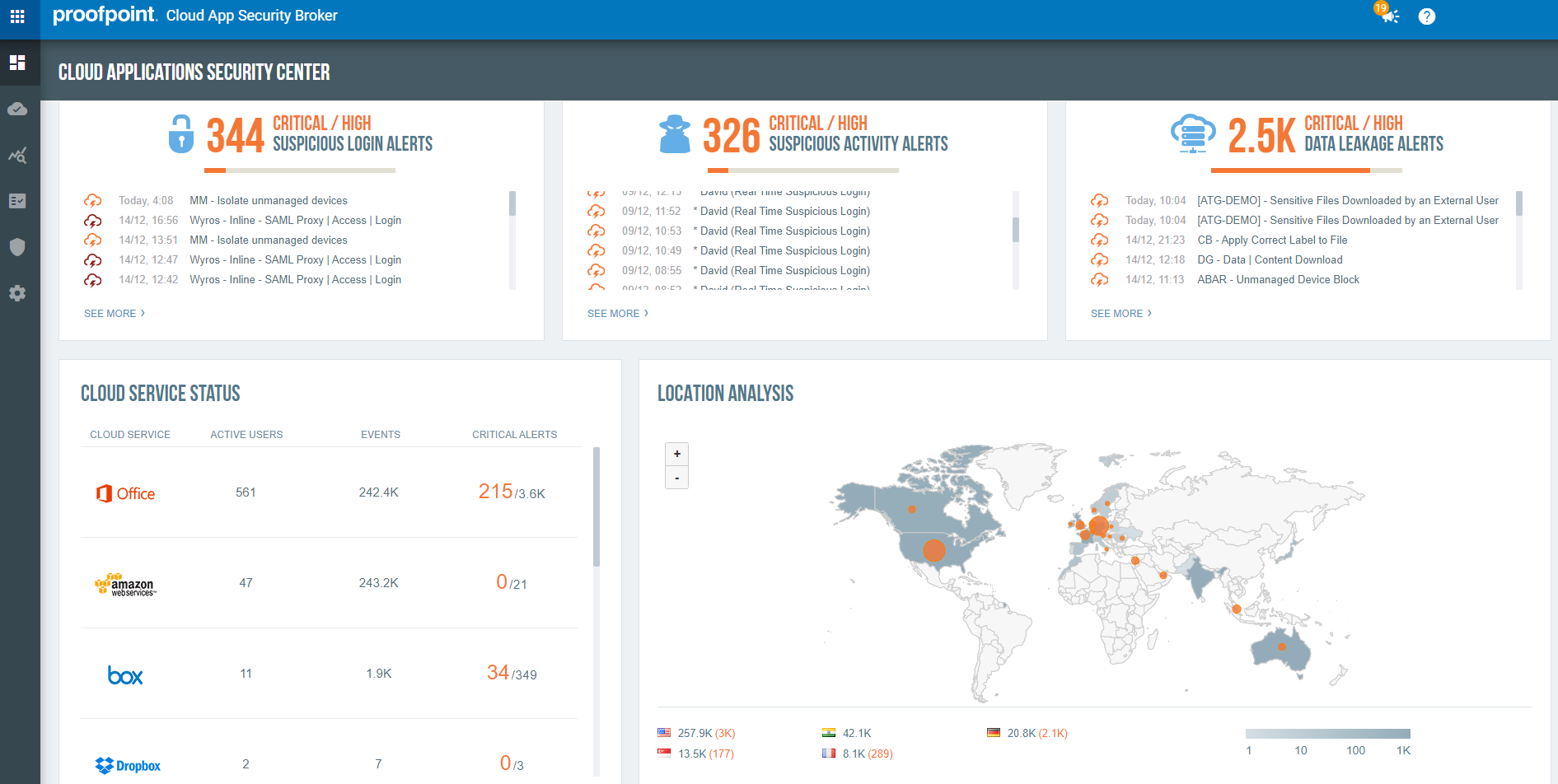
Proofpoint Cloud App Security Broker (CASB)

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
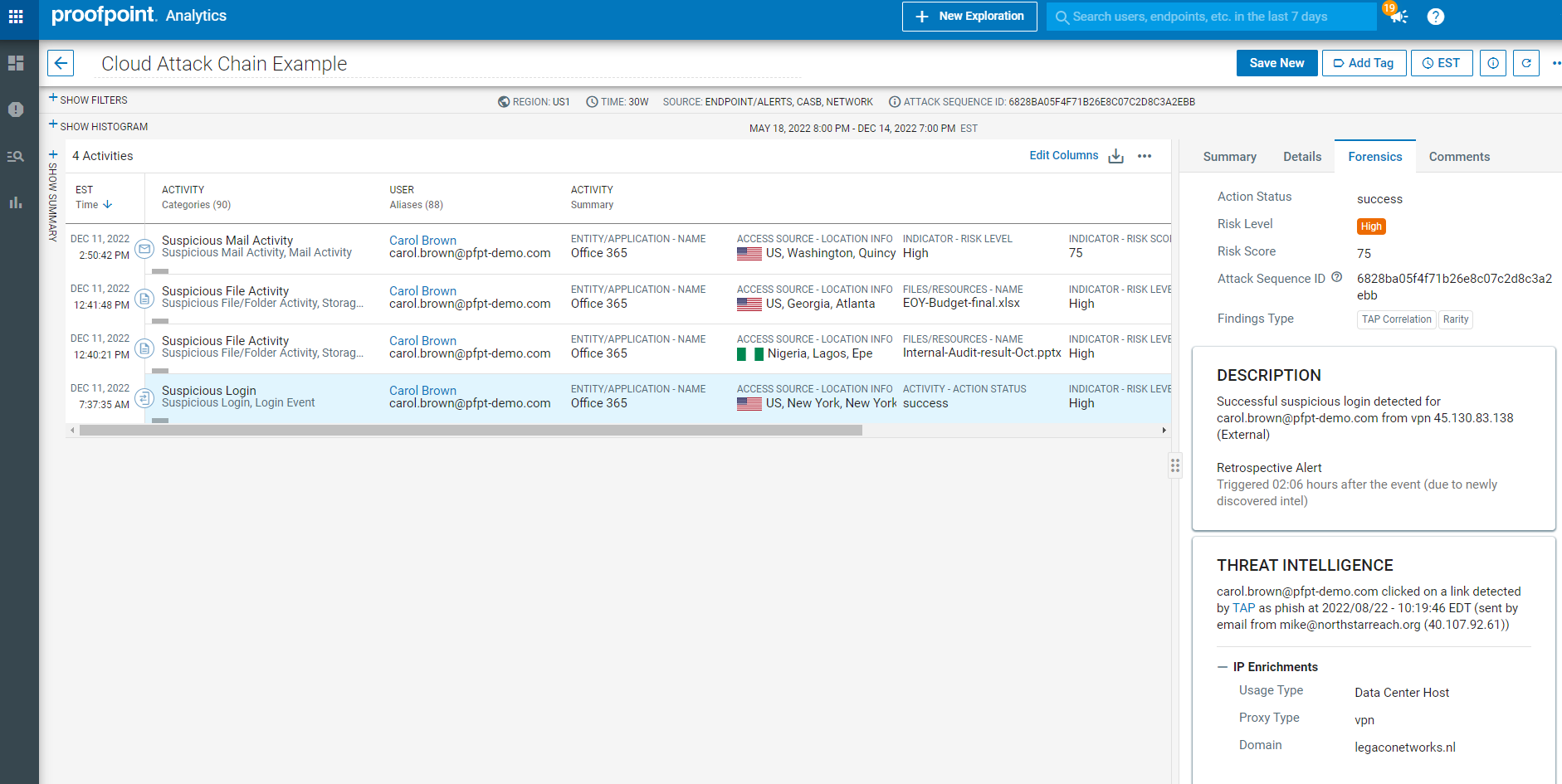
Email continues to be the #1 threat vector. And threat actors are using email to get inside organization’s cloud environments, especially SaaS and web apps. Proofpoint uniquely focuses on protecting users and sensitive data from cloud threats at the intersection of email, web and SaaS worlds.
Proofpoint CASB is a cloud-native and an easy to deploy and use solution highly targeted on today’s top SaaS threats: account takeover, malware, misconfigurations, OAuth abuse and mailbox abuse. By protecting organizations against these SaaS threats and risks, we stop business problems such as business email compromise (BEC), fraud and cloud ransomware.
Our multi-mode solution combines:
-Compromised account detection and automated response
-Protection against malicious files uploaded or created within SaaS apps
-SaaS and third-party apps governance including third-party OAuth apps
-IaaS protection
-Real-time detection of malicious files
-Granular controls such as risk-based authentication, read-only access and micro-segmented application access
-Rich, cross-vector threat intelligence on user risk
-Controls over IT-approved and tolerated SaaS apps that are used in the browser or within native clients
How we are different
Proofpoint CASB is purpose built for SaaS threats and cloud app governance problems with people-centric security analytics and risk-adaptive access controls. We correlate threat intelligence across email to cloud phishing attempts, known threat infrastructure, prior credential dumps, and bruteforce campaigns. Legacy solutions provide shallow protection against the top SaaS threats because they are missing visibility into email channel where most threats begin.
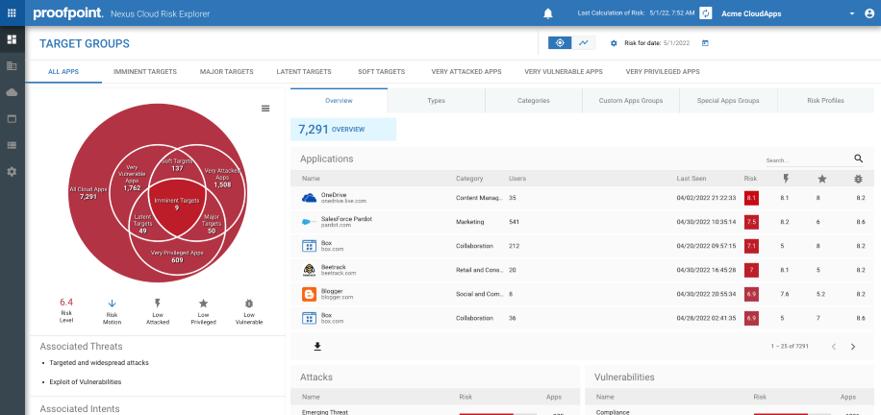
Proofpoint CASB provides instant visibility into SaaS threats when customers connect their cloud apps to Proofpoint. With native integrations across Proofpoint products, we can remediate issues across email, cloud and web channels. Network centric approaches have to wait for IT to install agents and reroute user traffic before providing any visibility.
With Proofpoint CASB, IT and security can more easily work together to discover and govern SaaS apps, third party OAuth apps, and IaaS services without complicated deployment models. In one view, customers can analyse their riskiest cloud services based on factors such as the most attacked or abused cloud services, those containing the most sensitive data, those accessed by the privileged users and the most vulnerable services. This includes first-party cloud apps (such as Microsoft OneDrive) as well as third-party OAuth apps (such as those in Google Workspace Marketplace and Microsoft AppSource federated through OAuth tokens). Legacy approaches fall short by either focusing only on static vulnerabilities in apps or by lacking the depth of detection capabilities in third-party OAuth apps.


