Photo Gallery
 |
 |
Proofpoint Cloud App Security Broker (Proofpoint CASB)

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
Proofpoint provides the only CASB to meet the needs of security people serious about cloud threats, data loss and time-to-value. Proofpoint CASB protects you from account compromise, oversharing of data and compliance risks in the cloud. Our agentless solution combines:
• compromised account detection and automated response,
• protection against malicious files,
• data security including DLP,
• cloud and third-party apps governance,
• IaaS protection
• adaptive access controls
We secure Microsoft 365, Google Workspace, Salesforce, Box, Slack, AWS, Azure and more. People-centric visibility to email and cloud threats helps organizations identify at-risk users and protect their accounts and data.
With Proofpoint, organizations can deploy consistent DLP policies across cloud, email and endpoint. You can also centralize alert management across these channels on a single console. Our powerful analytics and adaptive controls help companies grant the right levels of access to users and third-party apps based on the risk factors that matter most.
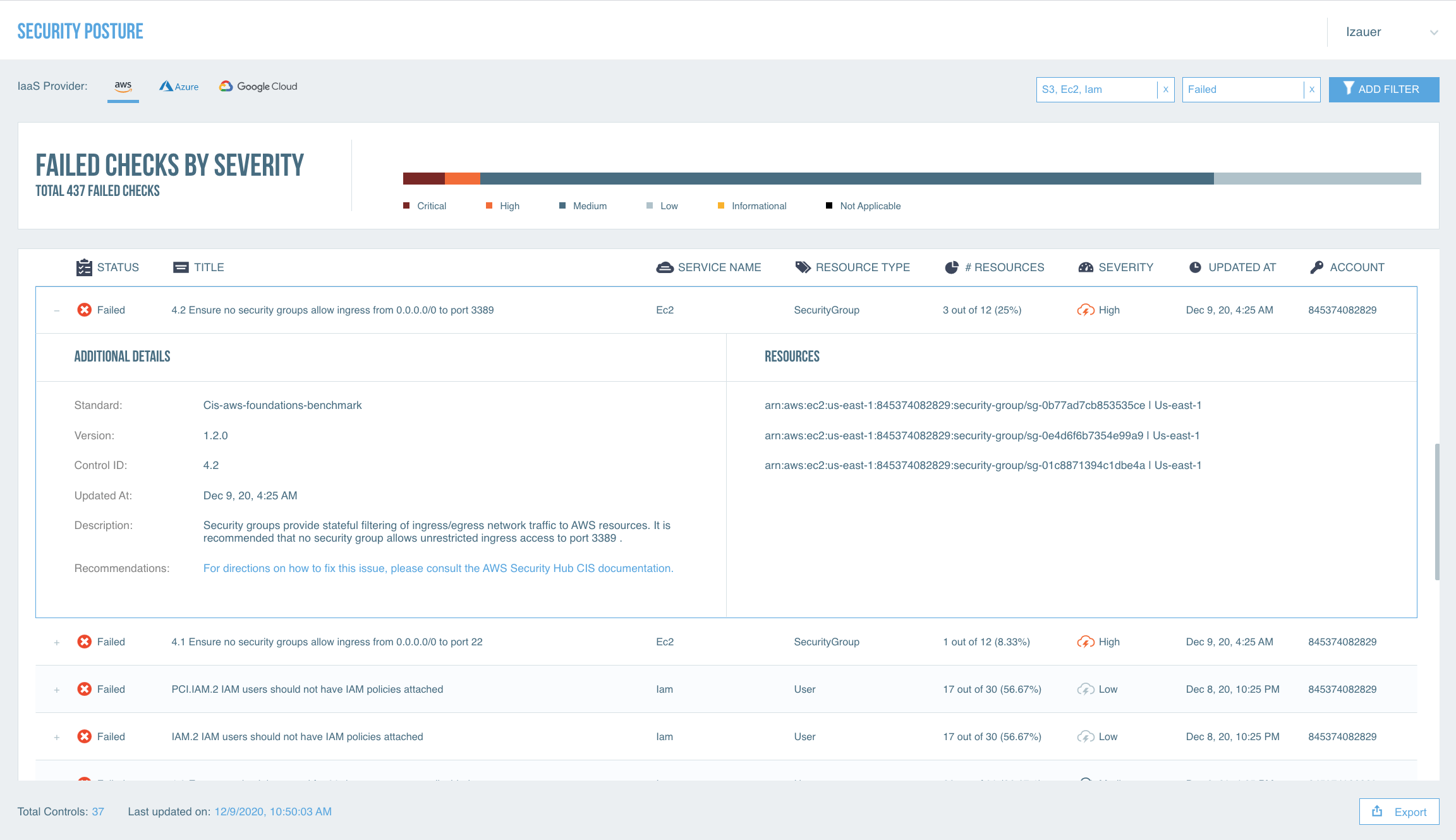
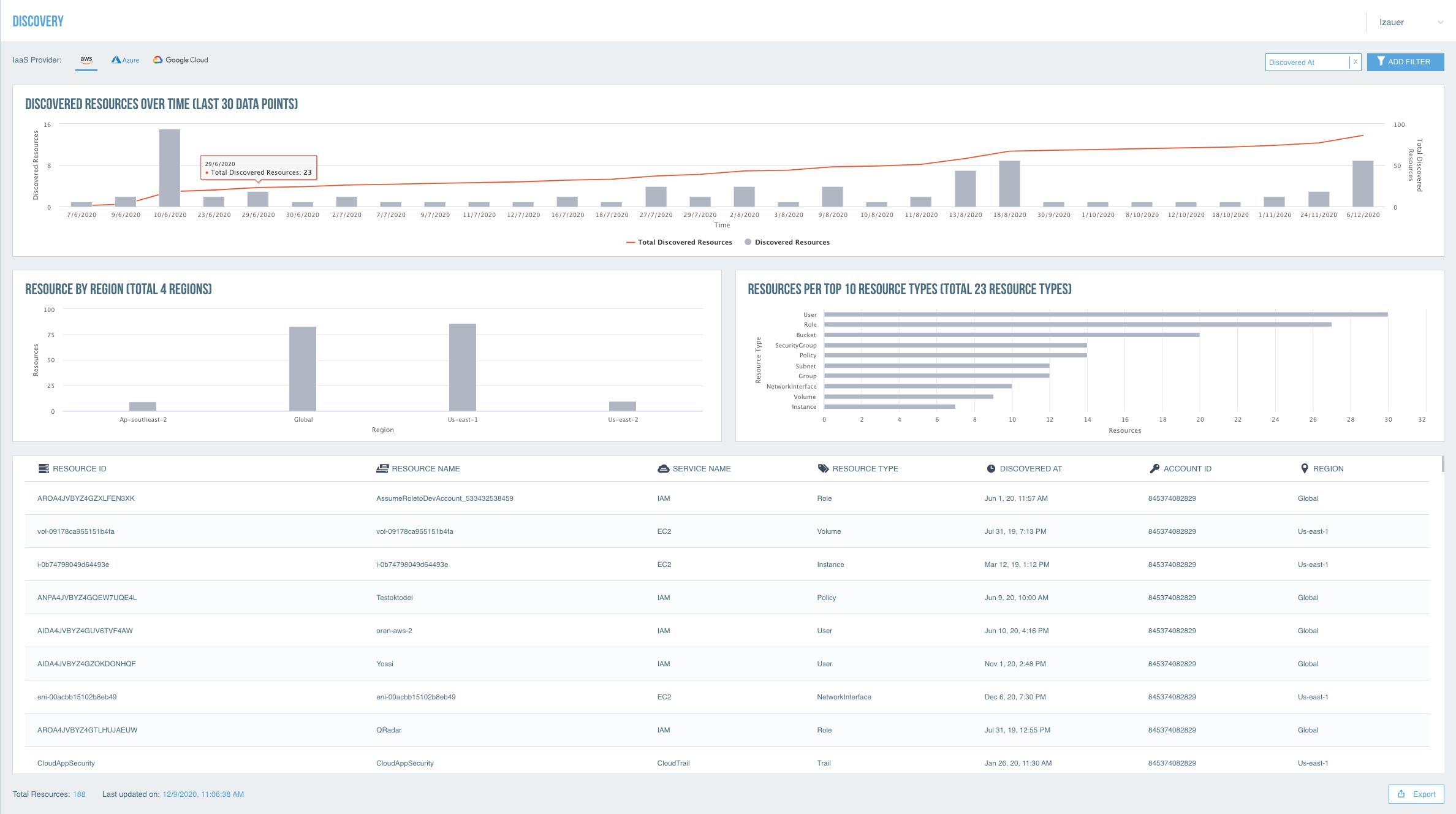
To protect your IaaS environments and ensure compliance, Proofpoint CASB IaaS Protection (IaaS Protection) provides:
• IaaS discovery
• Cloud Security Posture Management (CSPM)
• Data security, including DLP for IaaS buckets and containers
• Threat protection, including cloud account compromise detection
• Adaptive access controls
With our IaaS Protection add-on module, you can:
• Identify misconfigurations in IaaS environments
• Monitor and control privileged user activity
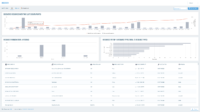
• Discover all IaaS resources and unprovisioned IaaS accounts
• Discover sensitive data in cloud storage and remediate excessive sharing of buckets with sensitive data
• Prevent unauthorized access to IaaS environments
How we are different
• Proofpoint CASB differentiates from competitors with people-centric and high-efficacy security analytics that excel at protecting users from threats, such as account compromise, malicious files, malicious apps and abuse of IaaS resources. To detect account compromise, Proofpoint combines contextual data (e.g. user device) and user behavior analytics with the timeliest and most accurate source of threat intel in the market. It also correlates with real-time email threats intel to connect the dots between credential phishing and suspicious logins. We issue retrospective alerts on compromised accounts previously missed. Proofpoint CASB also detects and remediates post-compromise suspicious activities such as email forwarding, malicious file uploads, etc. We detect and block malicious files and URLs using a blend of Proofpoint’s industry-leading hash checking and sandboxing technologies. We detect and control third-party apps, including malicious ones. The solution’s fine-grained forensics provide unique visibility into at-risk users and account compromise. People-centric adaptive access controls prevent unauthorized access to your cloud apps and IaaS accounts.
• Data loss originates with people. They can be negligent, compromised, or malicious. Understanding user intent enables you to apply the appropriate DLP response to mitigate risk. Proofpoint is the only vendor that brings together the telemetry of content, user-behavior and threats across the most critical DLP channels – email, cloud (SaaS and IaaS storage), and endpoint. Proofpoint’s unified threat and DLP alerts management, data classification, robust policy templates, investigative workflows and reports delivers consistency and simplified day-to-day operations, minimizing DLP complexity for optimal manageability for small team or limited resources.
• With Proofpoint CASB, you can govern SaaS apps and IaaS services in a centralized management console. We help you discover Shadow IT, including unapproved cloud apps, third-party apps and unprovisioned IaaS accounts. Proofpoint helps you manage compliance risk. We risk-score cloud apps and third-party apps and identify IaaS misconfigurations.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



