Photo Gallery
|
Proofpoint Email Protection

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | proofpoint.com |
NOMINATION HIGHLIGHTS
Proofpoint Email Protection protects end users from malware, credential phishing, and email fraud, enabling administrators to quickly respond to security incidents. Email threats are rapidly evolving and Proofpoint invests approximately 20% of revenue (roughly $100M in 2017) back into R&D ensuring its products stay ahead of emerging threat tactics.
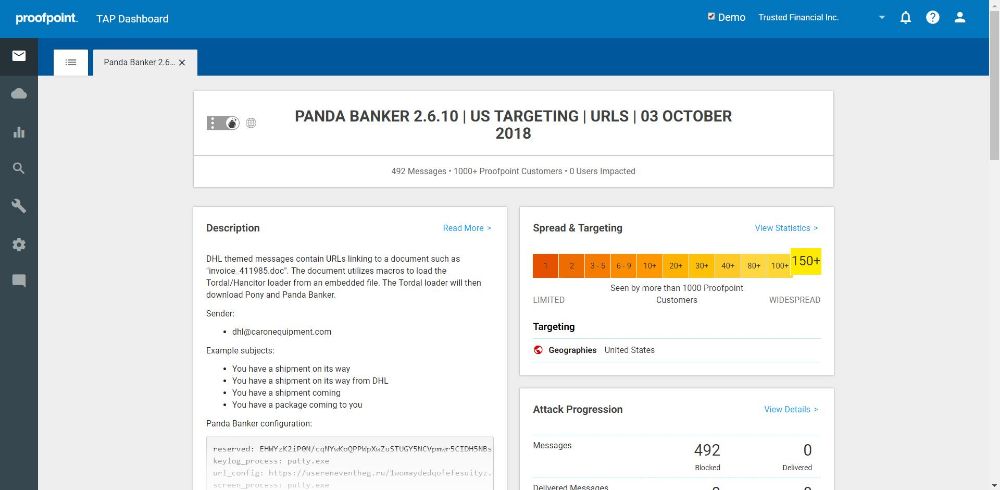
Proofpoint offers an integrated threat dashboard spanning malware, phishing, and email fraud, that organizations can use to understand the threats targeting them, who in the organization is being targeted, and the campaigns and threat actors that are attempting to steal data.
In 2017, Proofpoint introduced automated discovery of lookalike domain registration, a rapidly emerging tactic, allowing organizations block suspicious lookalike domains before an attack is even launched. Email Protection customers have visibility into their supply chain partners and their security posture as it relates to email authentication policy and enforcement.
With accurate malware detection and blocking, coupled with credential phishing and email fraud protection, Proofpoint Email Protection drastically reduces potential information loss and financial consequences due to infection and compromise.
Proofpoint also automates response actions such as removing malicious email from an end user inbox if determined to be malicious after delivery (such as a URL that is weaponized post-delivery). In addition, Proofpoint provides deep visibility into threats, campaigns, and groups targeting the organization. DLP capabilities automatically detect a wide variety of private information and block, quarantine, or encrypt as appropriate, customized by the customer.
As businesses move email inboxes to the cloud, Proofpoint business continuity maintains control so, in the event of a service outage, IT teams can also enable normal business operations.
How we are different
Proofpoint Email Protection is the only solution offering complete, effective protection against malware, email fraud, and credential phishing, while enabling automated response. When compared against competitors, Proofpoint provides:
• Increased Effectiveness against both malware and malware-free threats: Proofpoint consistently provides more enhanced capabilities to detect and block threats than competitors. Proofpoint incorporates detailed email analysis/classification (identifying BEC threats) with full kill-chain analysis, including dynamic sandboxing, and innovative techniques. This includes threats such as email fraud and credential phishing, signaturing the output of the kits attackers use to generate phishing pages and proactively detecting against spoofing and lookalike domains.
• Greater Visibility & Control: Granular classification of email into 7 separate email quarantines (spam, adult, impostor, bulk, low priority, phishing, and suspect). Granular threat forensics enable organizations to understand how they are targeted. Automated remediation removes potentially malicious email from inboxes. Threat visibility includes detailed insight into threats, campaigns and threat actors enabling organizations to have visibility into who is targeting them, why, and how to prevent them.
• Automated claw back of malicious emails from end user inboxes: Given the complexity of threat adversaries, some threats are only weaponized after successful delivery. Proofpoint automates the identification and removal of these threats from end user inboxes; reducing risk without additional overhead for administrators. This also extends to abuse mailbox monitoring, enabling messaging and security teams to roll-out an abuse mailbox reporting program while eliminating the additional workload associated with identifying if reported emails are malicious and searching for all delivered emails and removing them from inboxes.
Image (required)


