Photo Gallery
|
Proofpoint Email Security

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
Proofpoint Email Security is an integrated solution that provides multi-layered protection across the email attack chain. Proofpoint invests 20% of revenue back into R&D – one of the highest in the industry – to ensure our customers stay ahead of emerging threats.
Proofpoint’s unique people-centric approach offers deep visibility an organization’s human attack surface. Through an easy-to-consume, integrated threat dashboard, security teams can quickly identify and focus on their biggest risks – the people being targeted by malware and non-malware threats like phishing and business email compromise (BEC).
Proofpoint Email Security effectively detects email carrying advanced threats such as ransomware, polymorphic malware, and weaponized documents/URLs, blocking threats before they cause any damage. With machine-learning and dynamic classifiers, as well as content and reputation analysis, Proofpoint accurately identifies phishing and impostor emails that have no malicious payload to detect. It also prevents fraudulent use of organizations’ domains by providing DMARC authentication capabilities and services, combatting Business Email Fraud (BEC) more effectively.
Proofpoint also automates threat response and remediation, such as removing malicious email from an end user inbox if determined to be malicious after delivery (such as a URL that is weaponized post-delivery). Additionally, email isolation enables risk-based isolation for URL clicks within corporate email and allows safe access of personal email on corporate devices.
Email data loss prevention (DLP) and encryption capabilities automatically detect a wide variety of confidential information and regulated data, allowing security teams to block, quarantine, or encrypt a message in an automated fashion, based on organizations’ unique policies. With Proofpoint Email Security, customers can not only contain the spread of an unsafe message if it somehow gets through, but also ensure that no sensitive information leaves their environment.
How we are different
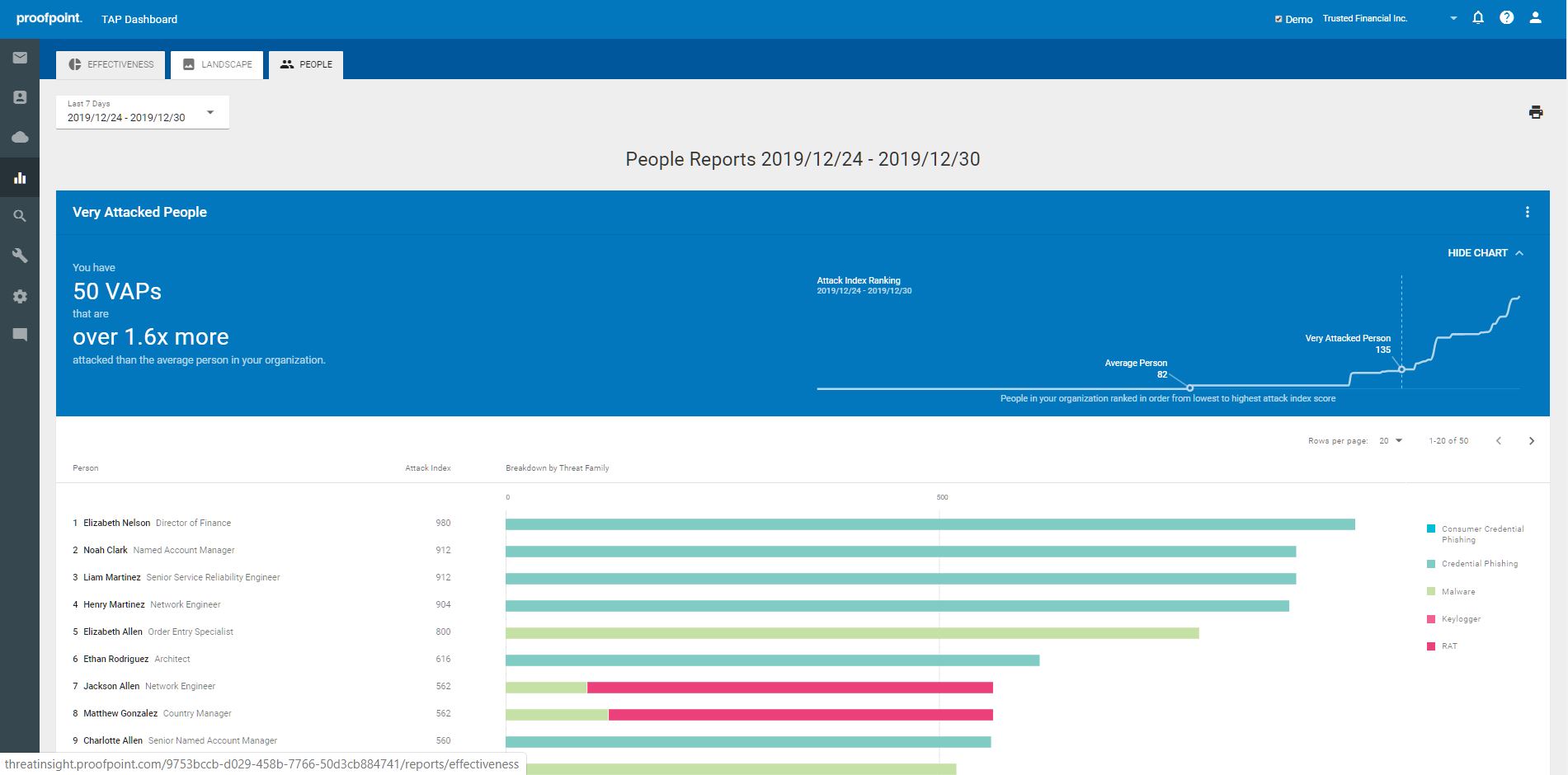
•Actionable visibility: Proofpoint’s unique people-centric approach delivers actionable visibility into the risks that matter – who is being attacked and how. Proofpoint’s Attack Index identifies the very attacked people (VAPs) within an organization and provides a weighted composite score of all threats sent to an individual in an organization. With this critical insight, security teams can tailor their security policies help mitigate their VAP risk and prioritize where and how to apply adaptive controls to protect those individuals that represent the greatest risk.
•Security effectiveness against business email compromise and advanced threats: Proofpoint Email Security consistently detects and stops email threats including, malicious attachments or URLs and non-malware threats like phishing and business email compromise (BEC).
Unlike other solutions that only rely on a single detection technology, Proofpoint leverages an ensemble approach that inspects the entire attack chain using static and dynamic techniques as well as multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification and evolving page design classification.
•Automated threat response and remediation: Proofpoint automates the identification and removal of these threats from end user inboxes, reducing threat exposure and simplifying remediation process without IT overhead. This also extends to abuse mailbox monitoring, enabling messaging and security teams to roll-out an abuse mailbox reporting program while eliminating the additional workload associated with investigating if reported emails are malicious and searching for all delivered emails and removing them from inboxes. A health system experienced operational savings of more than $300,000 with Proofpoint Email Security.
Proofpoint is the only vendor who can provide an integrated solution that addresses all attackers’ tactics while automating threat response and remediation with multiple response options.


