Photo Gallery
 |
 |
Proofpoint Email Security

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
75%+ of ransomware originates from email according to Unit42 of Palo Alto Networks. To stop more ransomware, you can move left in the attack chain. Additionally, limiting data exposure in the cloud is important to minimize potential ransomware impacts.
Proofpoint Threat Protection and Cloud Security platforms prevent and protect against them. Our comprehensive, integrated platforms layers controls that:
• Prevent the initial infection:
– Advanced ML & AI to detect malware, malicious code and evasion detection in emails
– Identify and protect sensitive information exposed in cloud accounts attackers could exploit
– Providing time-of-click protection for URLs and isolation controls for very attacked person (VAPs)
– Providing targeted security awareness on ransomware based on real-life attacks
– Empowering users to report suspicious emails via our button or HTML tags
– Automating the investigation and remediation of user-reported and malicious email
• Detect initial access and prevent discovery, lateral movement and persistence:
– Providing real-time adaptive access controls for users by automatically blocking access to cloud apps from risky locations and from known threat actors.
– Define access policy controls such as enforcing MFA and restricting access from unmanaged devices
– Actively monitor and quarantine cloud file share
– Alerts you about potentially infected files
– Blocking connections to compromised sites preventing machine control from ransomware operators
– Limiting visibility of ransomware actors by providing users with micro segmented secure access to help identify and remediate over-permissioned or sensitive files
• Prevent data exfiltration:
– Provide granular data controls like read-only access
– Allowing or blocking for cloud apps and web
– Visibility into suspicious file activity linked to suspicious logins so responders can quickly separate attacker-initiated file activity from user-initiated file activity
– Blocking sensitive content from being exfiltrated via command and control, downloaded to unmanaged (ransomware operator’s) devices, and being emailed out
How we are different
● Unparalleled Protection – TAP leverages numerous techniques to protect against the everchanging threat landscape. This includes leveraging both our Nexus Threat Graph and NexusAI which provides sharing of threat intelligence from trillions of real-time data points across multiple threat vectors around the world, advanced AI and machine learning and a global research team that keeps you ahead of today’s biggest cyber threats as well as being the market leader in email and leading in other vectors such as cloud, network and social.
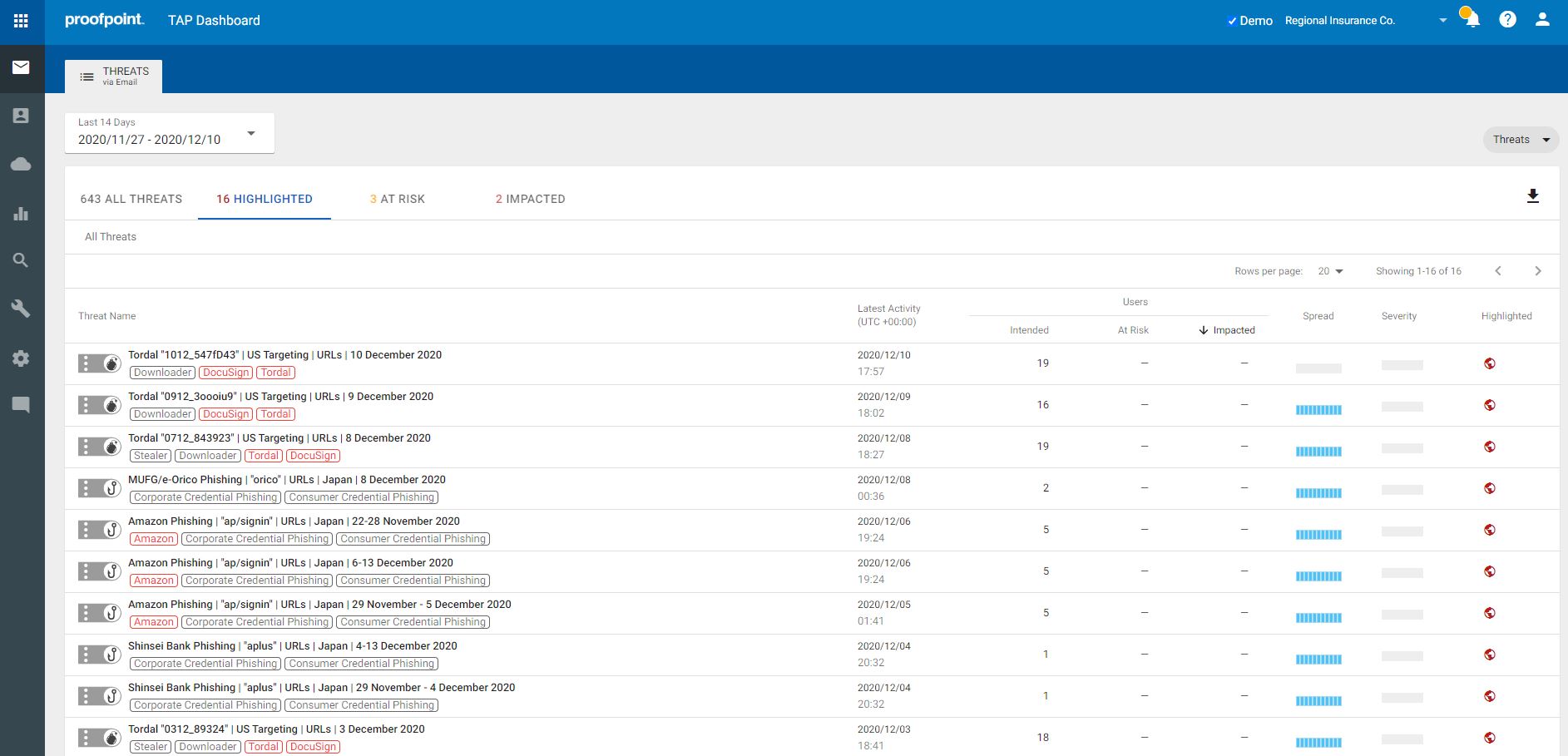
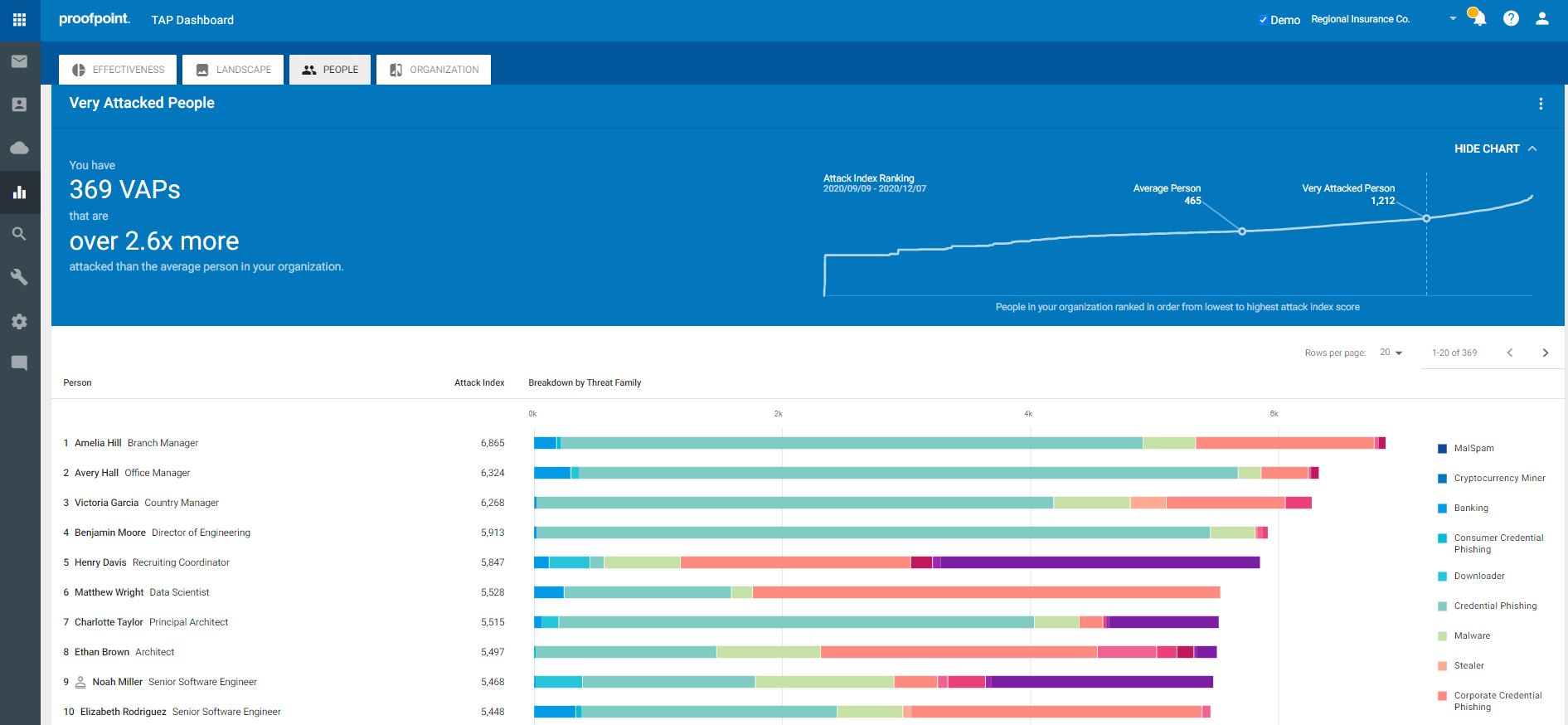
● Unmatched Visibility – Proofpoint provides detailed information on threats and campaigns in real time. You gain visibility into both widespread and targeted attacks. It gives you details around the threat itself from impacted users, attack screenshots, and very in-depth forensics. Proofpoint helps your security teams understand who your most attacked people, or VAPs, are in order to protect them against the threats and ransomware that target them. Proofpoint helps you understand the level of threat actor sophistication targeting your users, the spread and focus of targeted attacked, the different types of attacks, and the overall attack volume. By better understanding how you are being targeted, you can then prioritize the most effective ways to resolve threats and defend against ransomware.
● Integrated Across Security Ecosystem – The threat forensics and VAP information can be integrated with Proofpoint solutions as well as other industry leading vendors such as CrowdStrike, Okta, SailPoint, CyberArk, Palo Alto Networks and Splunk.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



