Photo Gallery
 |
 |
Proofpoint Email Security

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
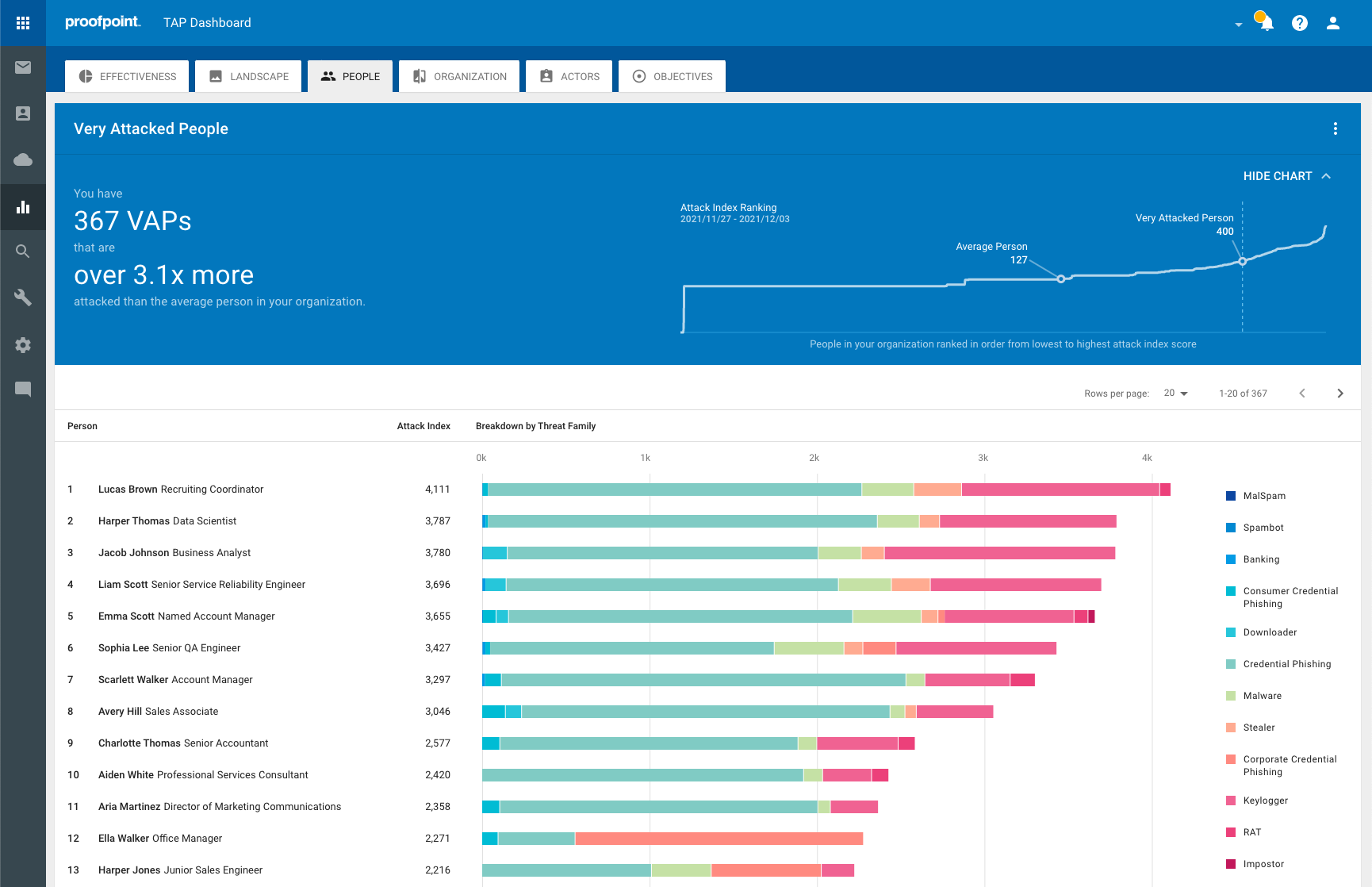
● According to the Verizon Data Breach Report, 96% of phishing attacks are delivered via email. Proofpoint provides an integrated, end-to-end solution to comprehensively prevent and remediate phishing attacks. It delivers actionable visibility into Very Attacked People (VAPs) and detailed forensics of phishing campaign; protects VAPs against credential phishing with adaptive controls; trains end-users to spot identity deception tactics.
● Proofpoint utilizes a combination of dynamic, static and protocol analysis techniques to inspect the full attack chain. Powered by our Nexus Threat Graph that aggregates and correlates over a trillion threat data points across email, cloud network, and social media, Proofpoint Email Security delivers visibility into the ever-changing threat landscape, and provides unparalleled phishing threat detection and response. It also uses NexusAI, our proprietary machine-learning technology that learns in real time, to accurately classify phishing email.
● To effectively mitigate risk of phishing attacks and credential theft, Proofpoint enables organizations to apply various risk-based adaptive controls, including email isolation, predictive sandboxing, and security awareness training to risky users. It dynamically isolates URL clicks based on the risk profile of the recipient and provides real-time anti-phishing scans. It preemptively sandboxes file-sharing URLs before users click on them rather than relying solely on reputation, successfully addressing collaboration platform phishing where attackers host and deliver malicious payloads via legitimate file-sharing sites. It also allows security professionals to safely assess how users would engage with impostors by simulating real-world phishing attacks and to auto-enroll those who require additional training.
● Proofpoint also automates threat remediation and streamlines abuse mailboxes. It automatically removes phishing emails containing URLs poisoned post-delivery, even if they’re forwarded or received by others. It allows end-users to easily report phishing emails with a single click. User reported messages are automatically analyzed and quarantined if found to be malicious, significantly reducing manual work and IT overhead.
How we are different
● Stop More Threats, Faster: Proofpoint leads the way in new detection techniques that stop various types of email threats, including credential phishing and email fraud. Our effectiveness is powered by the Nexus Threat Graph, which is built on billions of emails, millions of cloud accounts, and thousands of malware samples every day from over half of the Fortune 1000, and by NexusAI, our dynamic, multi-layered threat detection engines that continuously learn from the threats we analyze. We continuously update our detection engines to address changes in the threat landscape. Through product evaluations against other vendors, Proofpoint always identifies a host of phishing and payload-less threats evading existing systems.
● Unmatched Visibility: Proofpoint provides actionable visibility into the human attack surface, revealing VAP risks and industry comparisons to help organizations assess, prioritize, and mitigate risk using adaptive controls. We can tailor user training using real-world attacks based on their own threats. We dynamically isolate URL clicks based on risk profile and we provide proprietary real-time anti-phishing scans that run as soon as the page is opened. We automatically identify impostor and phishing threats posed by vendors and suppliers.
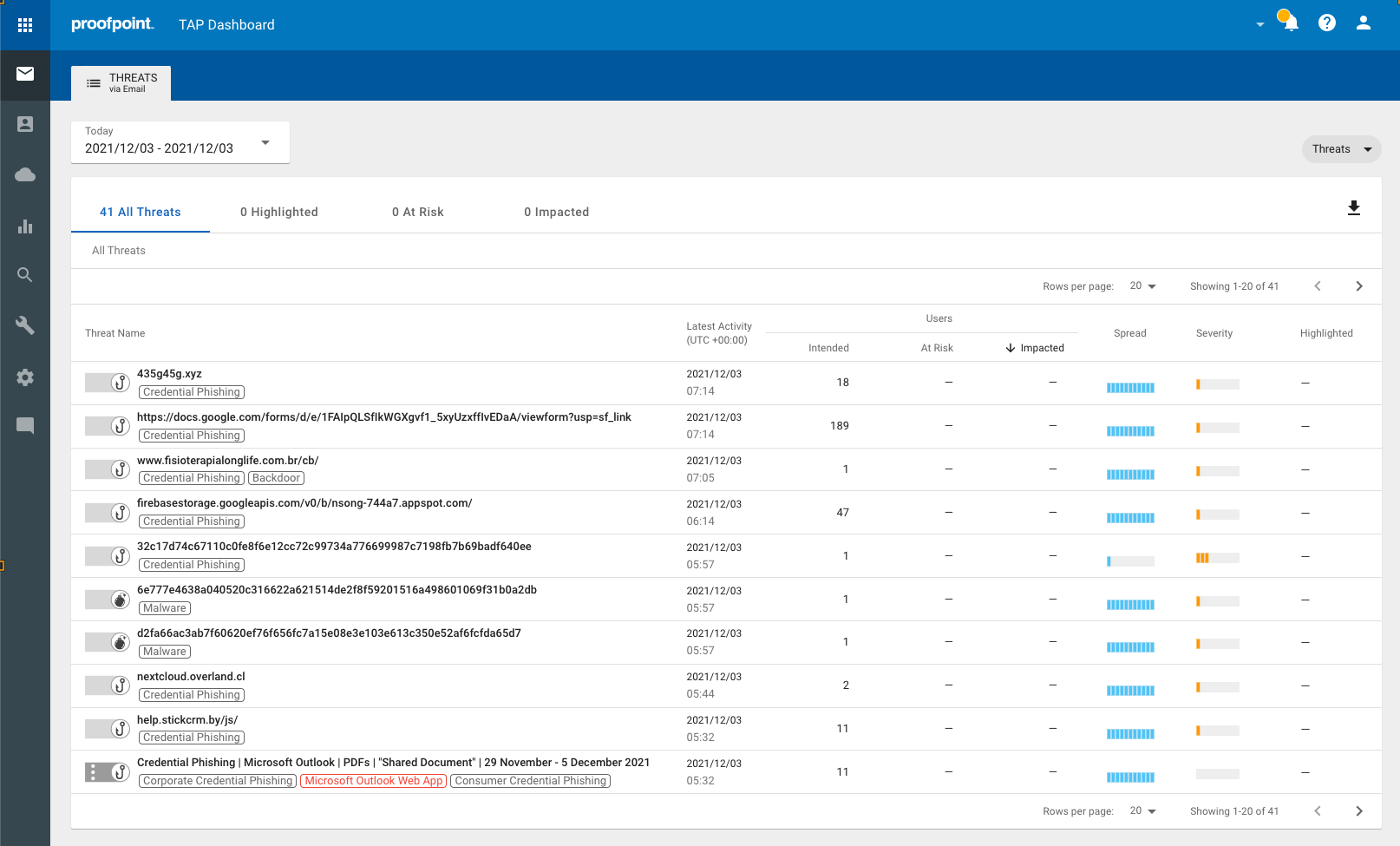
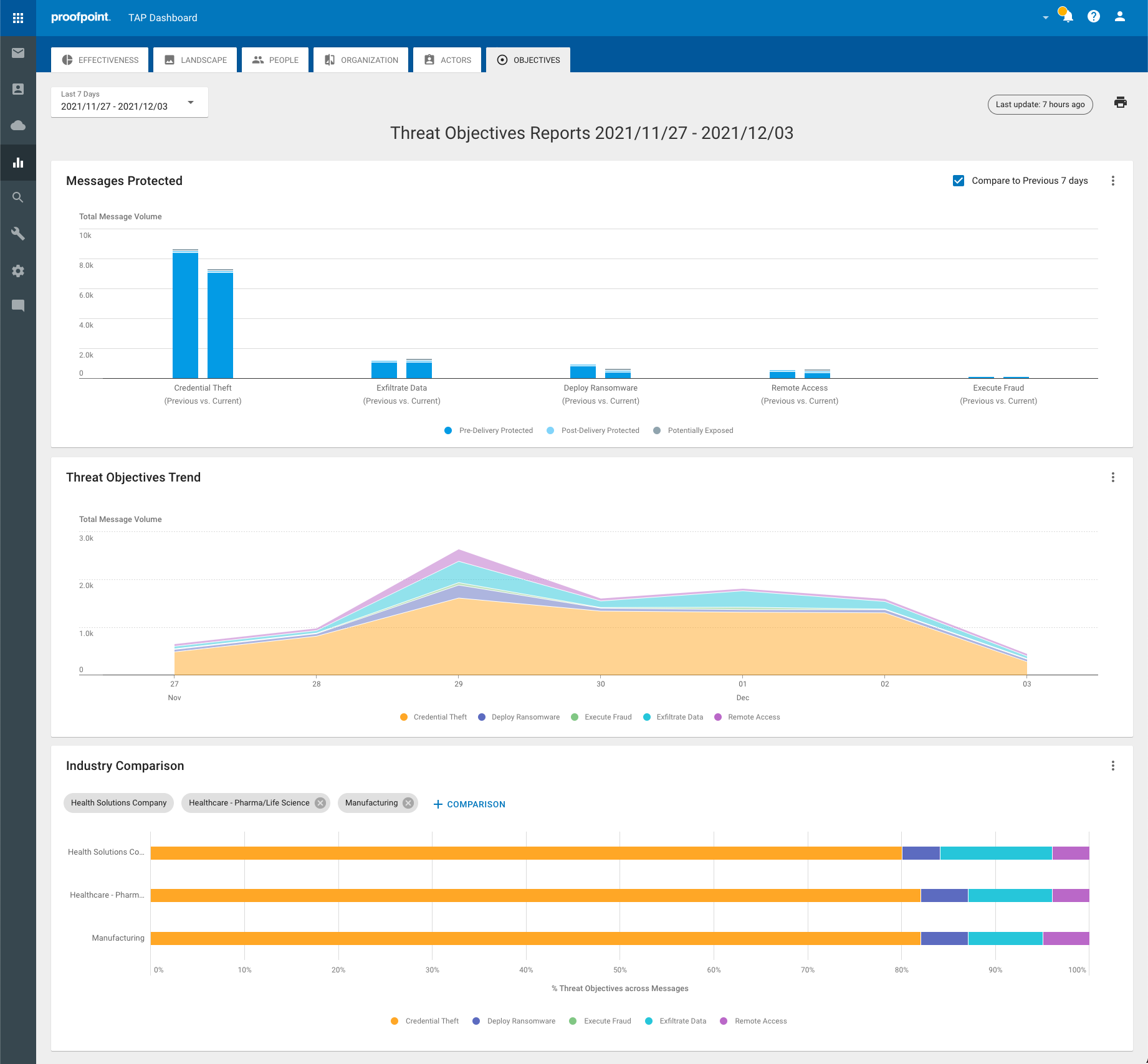
● We offer detailed forensics, enabling organizations to understand how they are targeted and how to prevent attacks. In 2021, we added the ability to see attacks over time at the actor, threat, and user level as well as insights into the possible objectives of those attacks. Both of these capabilities give analysts additional insights and information to better protect their organization.
● Improve Operational Effectiveness: Proofpoint delivers operational savings by providing integrated solutions that focus on threats that matter. We automatically remove email threats that are weaponized post-delivery. We enable users to report suspicious phishing emails through email warning tags. We streamline abuse mailbox management, eliminating the manual work associated with threat investigation and remediation.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



