Photo Gallery
|
|
Proofpoint Email Security

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
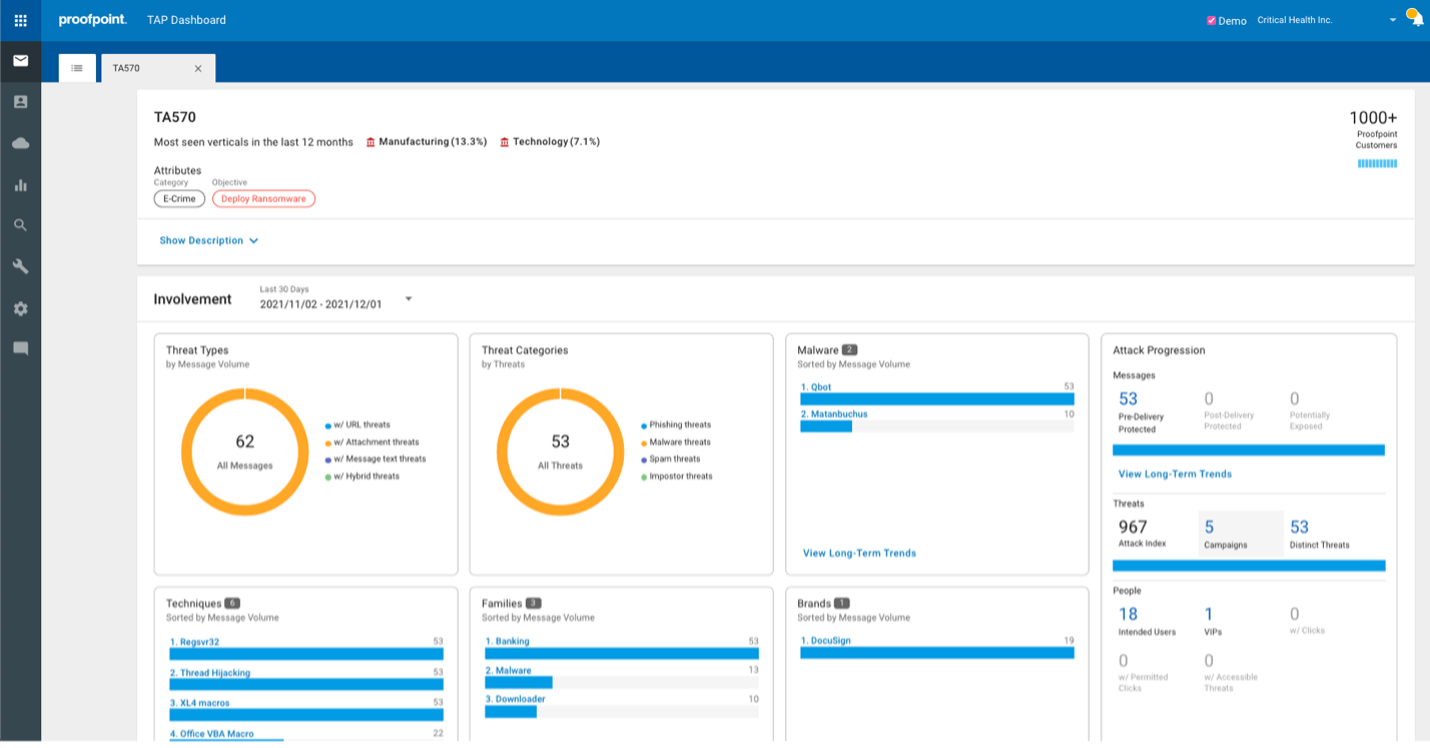
According to Palo Alto’s Unit 42 Ransomware Report, 95% of ransomware incidents observed in 2021 were human activated, including 75%+ which came specifically through email. Proofpoint Threat Protection Platform effectively detects and blocks advanced malware and ransomware spread via email. No matter how it’s delivered, through malicious attachments, URLs, or even file-sharing sites, Proofpoint Email Security shifts the attack chain left to stop malware before it reaches end users’ inboxes.
To better detect advanced malware, such as ransomware and polymorphic malware, Proofpoint utilizes a combination of dynamic, static, and protocol analysis techniques to inspect the full attack chain. Powered by our Nexus Threat Graph, which aggregates trillions of threat data points across email, cloud networks, and social media, Proofpoint Email Security delivers unique visibility into the ever-changing threat landscape and provides unparalleled malware protection.
This technology prevents access via credential theft and stops first stage delivery by blocking initial downloaders, thus protecting users against malware, ransomware, and other malicious content. This is especially true for emails that contain compromised URLs which only become unsafe post-delivery.
In addition, it successfully addresses attackers hosting and delivering malicious payloads via legitimate filesharing sites, such as SharePoint and OneDrive. Proofpoint’s predictive sandboxing technology preemptively opens file sharing URLs before users click rather than relying solely on reputation, making it more effective at stopping multi-stage attacks that hide the payload within these sites.
With actionable visibility into complex attack campaigns, Proofpoint provides security teams with insight around who and what is being targeted and how, as well as information around the threat actors involved and the malware and tools they use. It sees everything – from advanced malware attacks targeted at the people within the organization to files in your SaaS file storage for a far-reaching view of the threat landscape.
How we are different
Stop More Threats, Faster: Proofpoint provides the most effective threat protection and leads the way in new detection techniques that prevent various types of email threats, including ransomware and multi-stage malware. Our effectiveness is powered by the Nexus Threat Graph, which is built on data collected from billions of emails per day, millions of cloud accounts, and 400k-600k malware samples per week. Our detection engines see more data than the competition and constantly adjust to provide protection for to-the-minute changes in the threat landscape. Our world renown threat research team aids in detection, and in product evaluations against other vendors, Proofpoint consistently identifies more malicious emails evading existing systems.
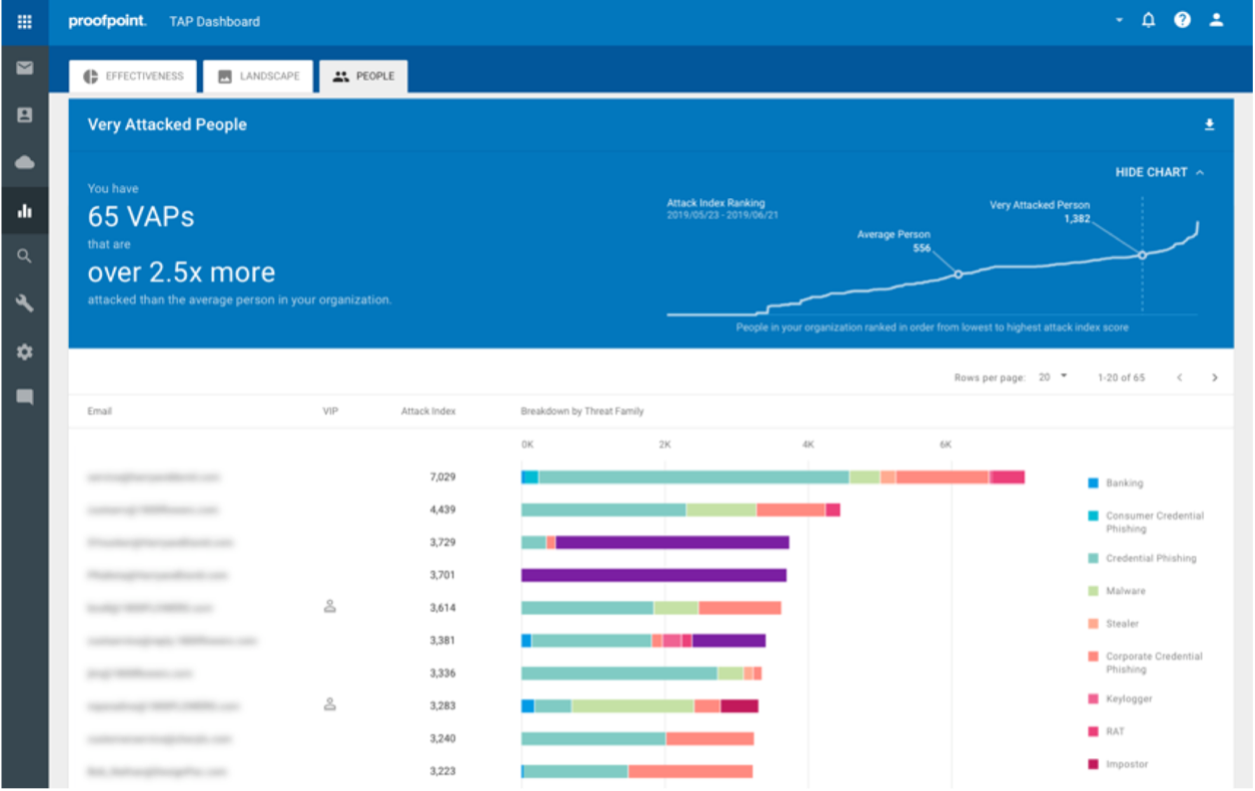
Unmatched Visibility: Proofpoint offers unique, actionable visibility into the human attack surface, revealing a company's Very Attacked People (VAPs) and providing peer comparisons to help organizations better analyze and mitigate risk. We offer detailed forensics on individual threats, threat campaigns, and attackers, which show organizations how they're being targeted and how to prevent breaches. Our unique VAP insights allow organizations to implement adaptive controls to add layers of protection around risky users. We’ve also created our Supplier Risk Explorer to extend this visibility to trusted contacts who may be compromised, as well as provide insight into attacker’s intentions with threat objectives and show user timelines to give context to the threats and actions of individuals.
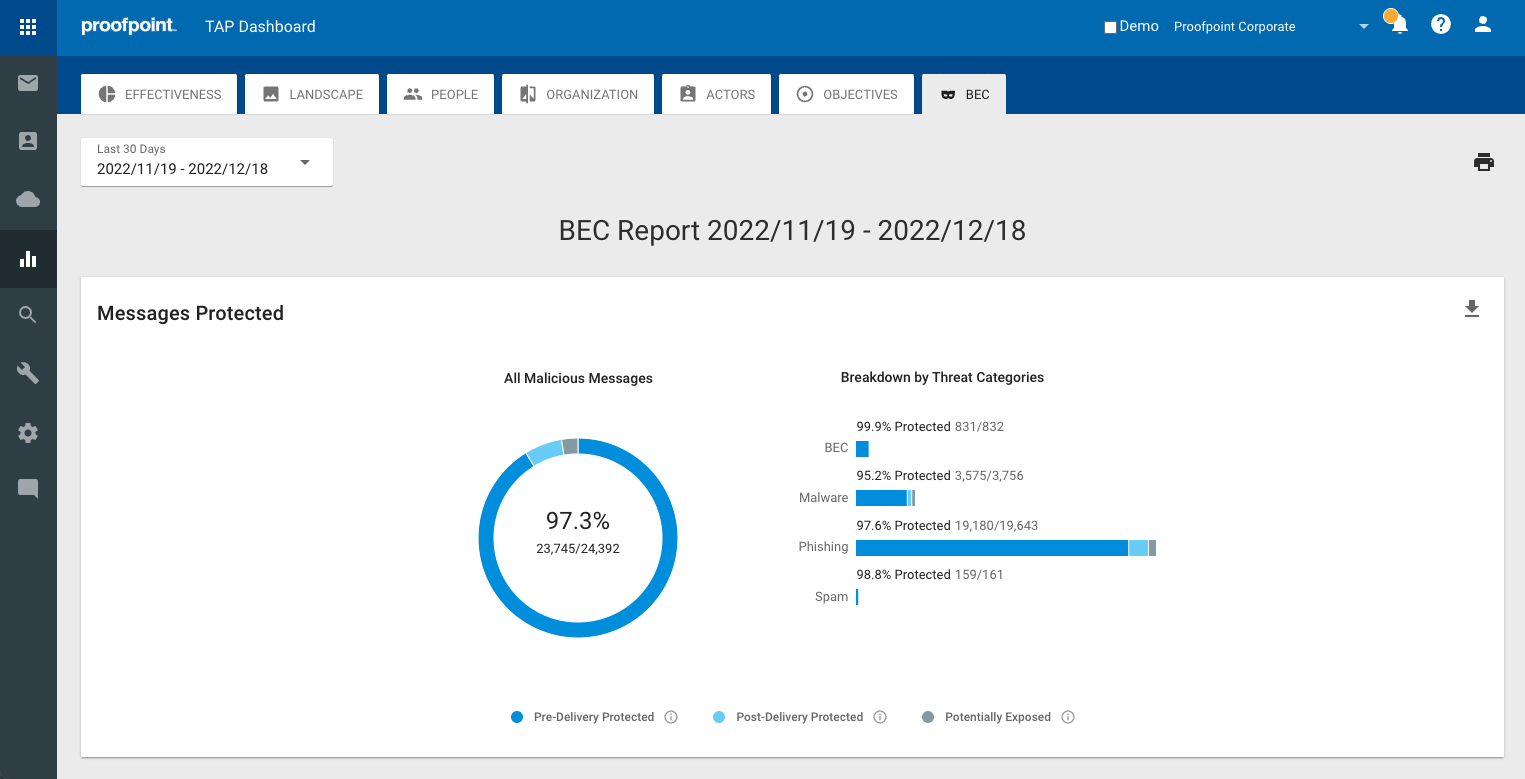
Improve Operational Effectiveness: Proofpoint delivers operational savings by providing a well-integrated solution that automates threat detection and remediation. We detect and automatically remove email threats that are weaponized post-delivery, including unwanted emails from compromised internal accounts. We streamline abuse mailbox management, eliminating the manual, labor-intensive work associated with identifying whether user-reported emails are malicious. We search for all delivered emails, remove them from inboxes, and provide users positive feedback so our customers don’t have to.


