Photo Gallery
|
|
Proofpoint Fraud Defense

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
Proofpoint provides a holistic fraud defense solution to protect against security, brand, and compliance risks across email, web, mobile, and social media. We effectively detect and block business email compromise (BEC); dynamically identify malicious lookalike domains registered by 3rd parties; reveals fraudulent social accounts; provides visibility into supplier fraud and trains end-users to spot identity deception tactics.
To protect organizations’ reputation from email fraud, Proofpoint authenticates all emails to and from its customers. We dynamically detect newly registered domains posing as our customers’ brand in email attacks or by phishing websites and notify organizations when a lookalike domain is sent as a malicious URL. By simplifying DMARC implementation and detecting and blocking impostor threats at the gateway with dynamic analysis, Proofpoint helps mitigate risks.
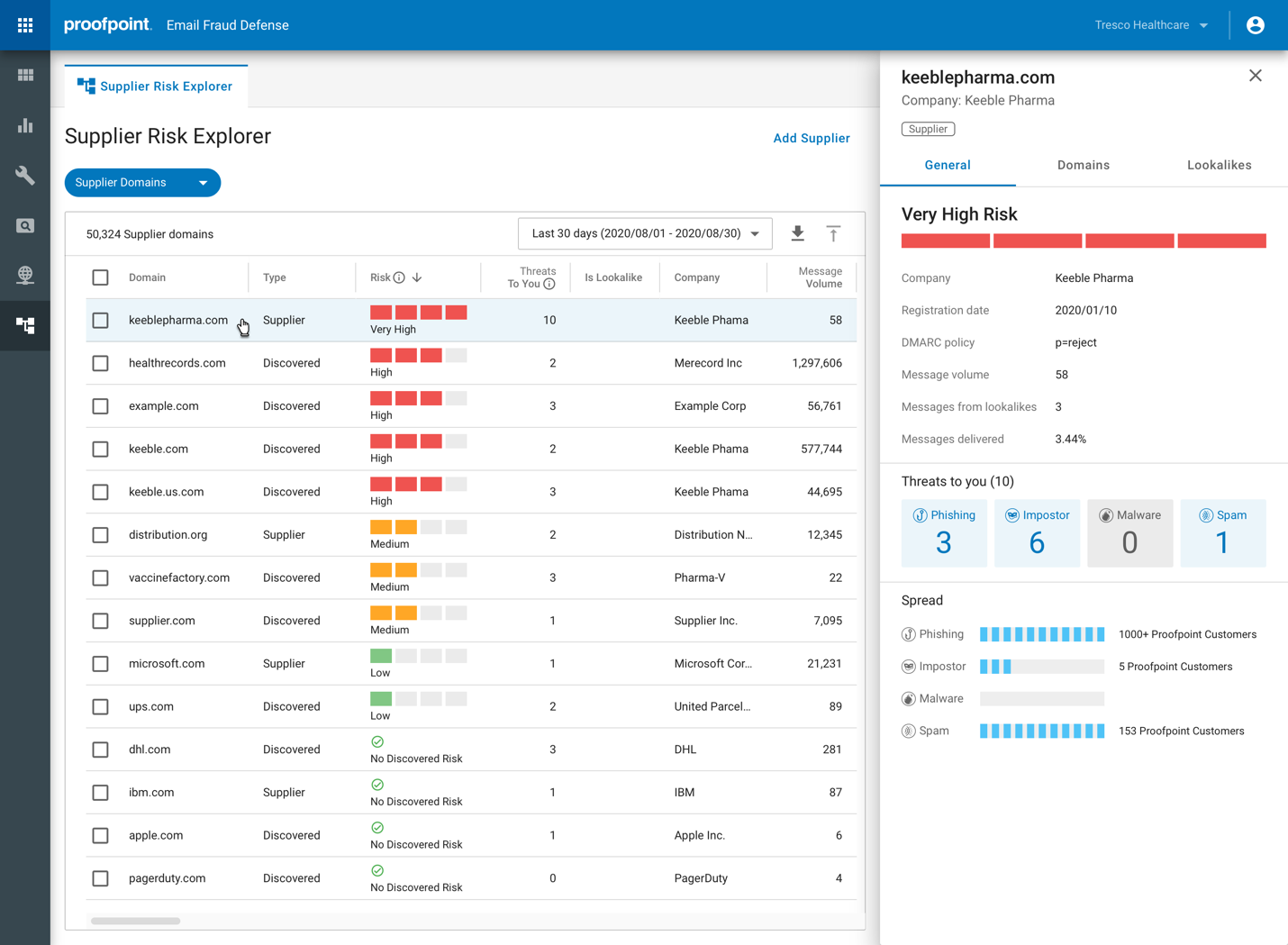
Proofpoint provides unmatched visibility into all emails being sent using its customers’ trusted domains as well as granular views of BEC threats, including targets and tactics. Supplier fraud mitigation is provided by automatically identifying an organization’ suppliers, validating their DMARC records and uncovering the risk they pose to the organization, including impostor threats. It also reveals the messages delivered from the lookalikes of those suppliers’ domain.
Earlier this year, we introduced our next generation ML/AI-based detection platform that leverages inbound and outbound gateway telemetry, supply chain risk analytics, and API data from cloud productivity platforms, like Office 365, to accurately uncover and stop email fraud, including the most sophisticated supplier invoicing fraud attacks. Our fraud defense solution also provides organizations a way to centrally discover, audit, and protect their social media presence. It identifies fraudulent social accounts imitating executives and brand; detects account takeovers in real-time and locks down compromised accounts. Using machine-learning and artificial intelligence, we analyze domain data to uncover infringing domains that pose a risk to an organization’s brand and customers.
How we are different
Detection Efficacy and Comprehensive Approach for Multiple Channels: Only Proofpoint provides a holistic solution that addresses fraud attacks across both email and digital engagement channels. Proofpoint accurately detects email fraud attacks with Supernova, our next-gen detection platform. It leverages a combination of machine-learning, stateful analytics, behavioral analytics, rulesets, and the work of researchers tracking threat actor tactics to deliver a detection platform with both high efficacy and low false-positive rate. It continuously learns from the threats we analyze and provides in-depth scanning across various digital channels, including social media, surface web, and the dark web. Additionally, we enable end-users to become more resilient to fraud attacks by providing threat-guided training, email warning tags, and one-click reporting.
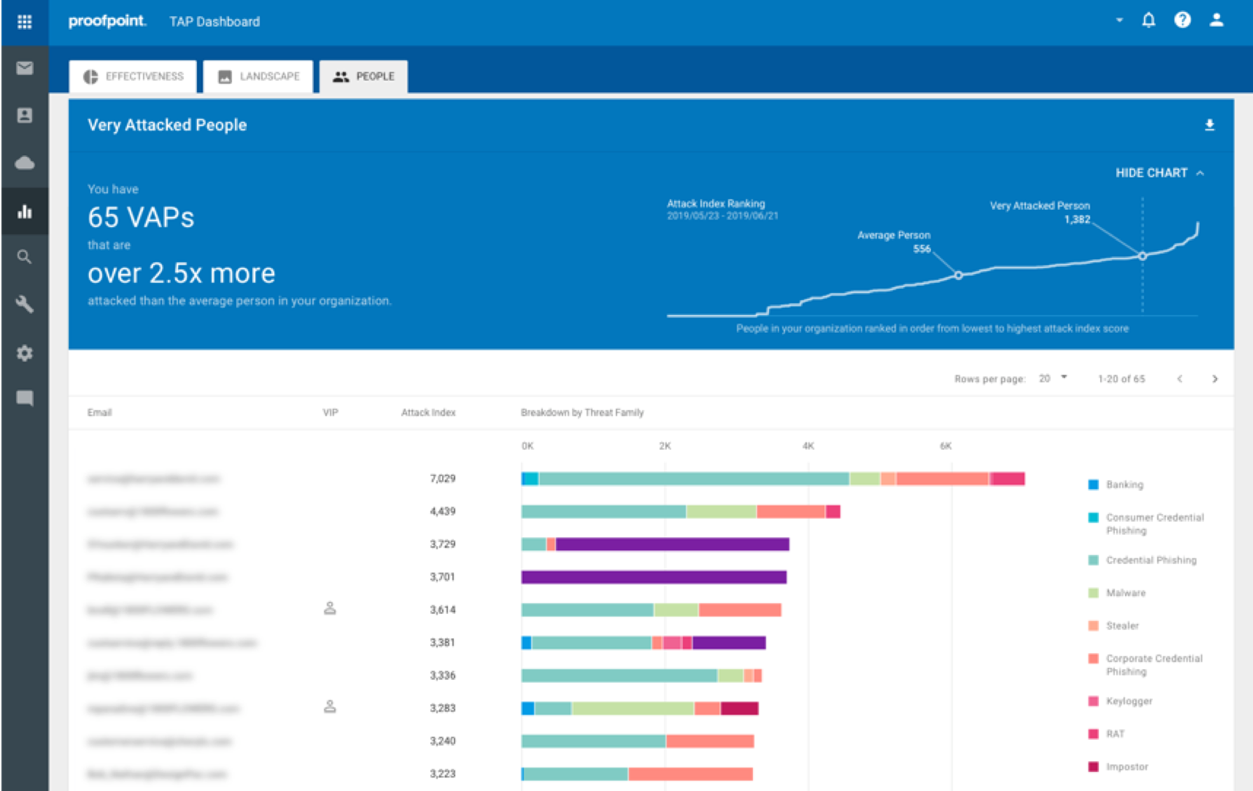
Unmatched Visibility: Proofpoint provides visibility into the human attack surface, revealing Very Attacked People and peer group comparisons to help organizations assess, prioritize, and mitigate risk. We identify which users are being attacked by what type of threats and provide granular visibility into BEC themes, such as gift carding, lures, payroll redirect, and invoicing fraud. We reveal malicious lookalike domains used to send fraudulent emails or used by phishing website and uncover fraudulent social accounts. With our newly released Supplier Risk Explorer, we provide supplier-centric view into threats, identifying risky suppliers and prioritizing the risk they pose to an organization. We’re also the first to identify malicious supplier lookalike domains.
Automated Response: Proofpoint automates threat response, saving organizations money by improving operational effectiveness. Suspicious impostor emails reported by end-users are automatically quarantined and analyzed. Security professionals can remove impostor emails with just one click or automatically, even if they were forwarded. Proofpoint also automatically removes unsanctioned content or locks down an account if account tampering has been detected. Organizations can easily designate approved account configurations, including authorized owners, images, credentials, and third-party applications.


