Photo Gallery
 |

 |
Proofpoint Insider Threat Management

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
The powerful forces of the cloud and mobility have spurred greater collaboration and more distributed workforces. At the same time, the 2020 Verizon DBIR report found that 30% of all data breaches involved an insider. Proofpoint Insider Threat Management (ITM) provides the leading solution for this problem with more than 1000 customers globally. We help organizations protect against data loss, malicious acts, and brand damage involving insiders acting maliciously, negligently, or unknowingly.
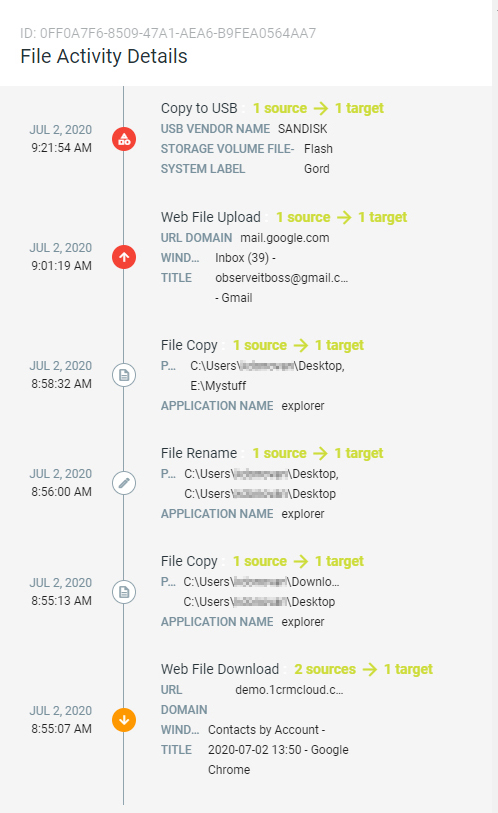
ITM correlates activity and data movement, empowers security teams to detect, investigate, and respond to potential insider threats by delivering real-time alerts, contextual intelligence on users, data and threats and easy to understand evidence of wrongdoing.
ITM delivers five key capabilities necessary for managing risky behavior on the endpoint:
1. Deliver visibility and context on user and data activity
2. Detect and alert on risky user behavior and data interaction in real time.
3. Prevent risky data exfiltration from the endpoint
4. Accelerate incident response and investigations
5. Simplify deployment with a pure SaaS platform and lightweight endpoint agent architecture
How we are different
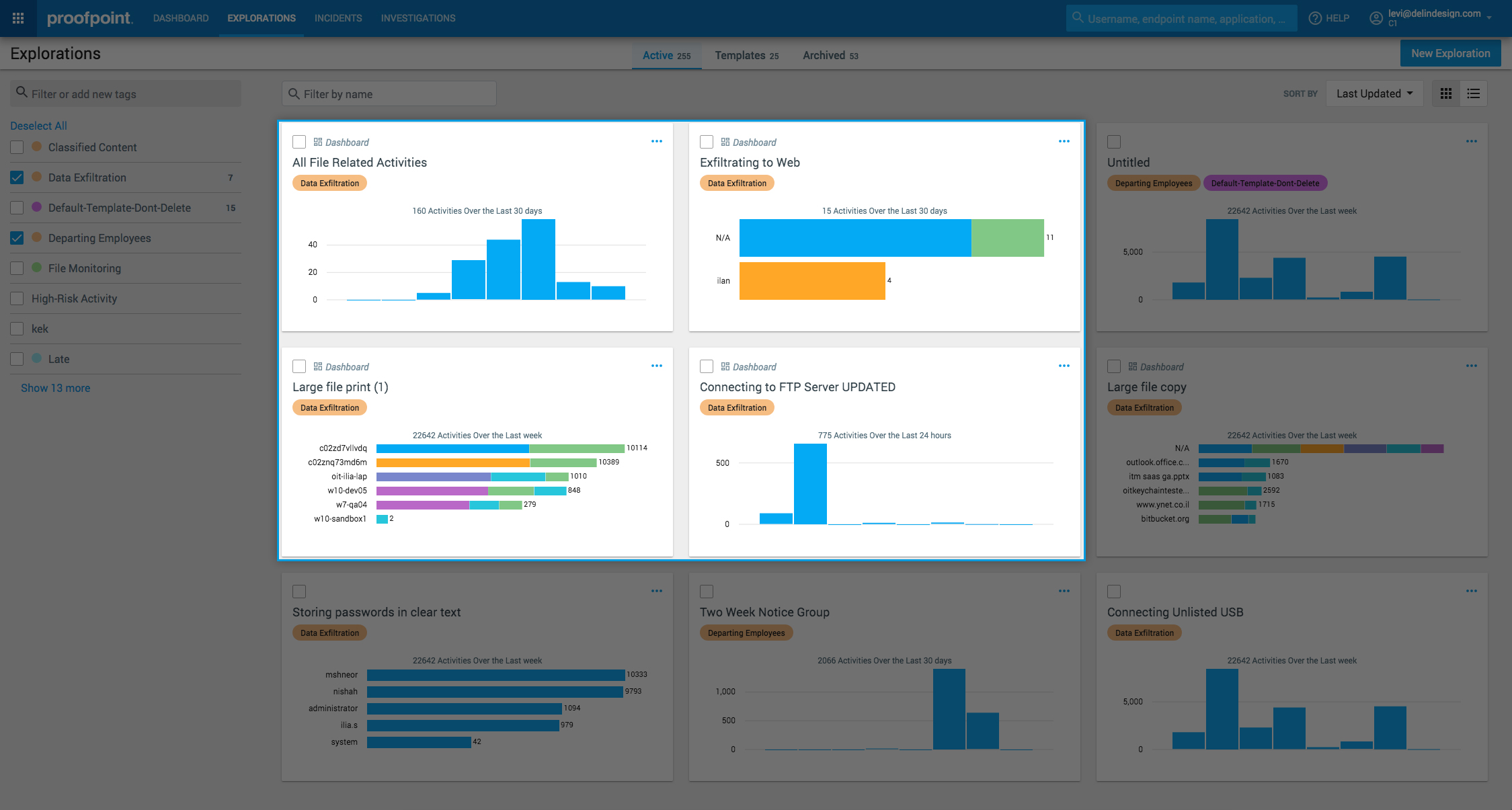
- Real-time visibility & detection: Given the number of applications used by each employee or contractor, security teams would need to constantly monitor and analyze an unmanageable number of application and security logs. Instead, Proofpoint ITM provides a single source of truth on your users and their activity across applications, files, data, servers, desktops and applications, whether the applications are hosted in the cloud, on the endpoint or on-premises. On top of this, we detect risky insider behavior across unauthorized activity and access, risky accidental actions, system misuse and out of policy data movement.
- Context: Legacy endpoint data loss prevention and user activity monitoring tools cannot provide the context of “who, what, where, when and why” around incidents to quickly triage and investigate alerts and incidents. Proofpoint ITM correlates all activity by user and visualizes it in an activity timeline. This is backed up by screenshots of activity before, during and after clear and obvious policy violations by the user. In effect, we paint a clear picture of evidence that is understood by cybersecurity and non-cybersecurity teams alike, without any jargon.
- Lightweight endpoint solution: Legacy endpoint DLP solutions rely on heavy agents that intercept most endpoint application transactions and often result in productivity drags and system crashes. Proofpoint ITM leverages a user-mode endpoint agent that doesn’t hinder users’ productivity or clash with your other security tools at the kernel level. Yet, our endpoint agents provide a granular, app-agnostic view into the user’s activity on the endpoint.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



