Photo Gallery
|


|
Proofpoint Security Awareness Training

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
Proofpoint Security Awareness Training empowers end-users to protect themselves and defend their organizations by educating them to recognize and report on human-activated threats. Our holistic solution assesses and shapes security behavior, creates sustainable habits, and provides metrics that measure the program’s performance against company objectives and comparisons against industry peers. It reduces human risk by educating users with threat-driven content and reinforcing positive reporting behavior. It keeps users engaged with targeted education relevant to their role, vulnerability, competency, learning style, and language. When integrated with our broader Threat Protection Platform, our security education solution automates threat investigation and response of user-reported messages, reducing time and IT overhead to remediate threats.
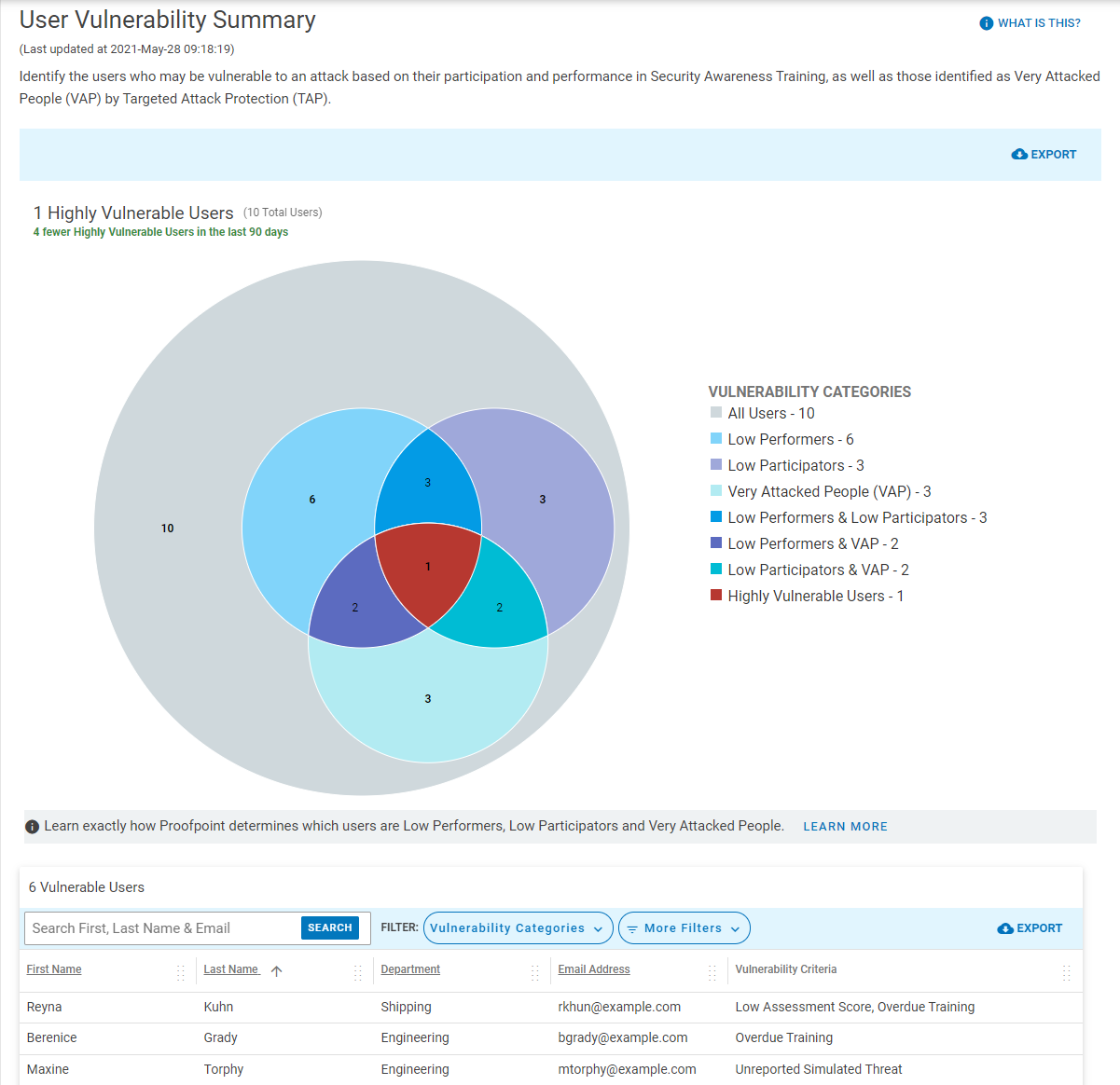
Proofpoint helps identify highly vulnerable users by providing unique visibility into the Very Attacked People and top clickers, as well as low participants and low performers. We allow organizations to establish baseline and identify gaps of current program by providing various tools such as knowledge assessment, culture assessment, and simulated phishing tests driven by real-world threats. Equipped with greater insight on user vulnerabilities and the threats targeting them enables program admins to provide tailored education to targeted users, making training more relevant to users.
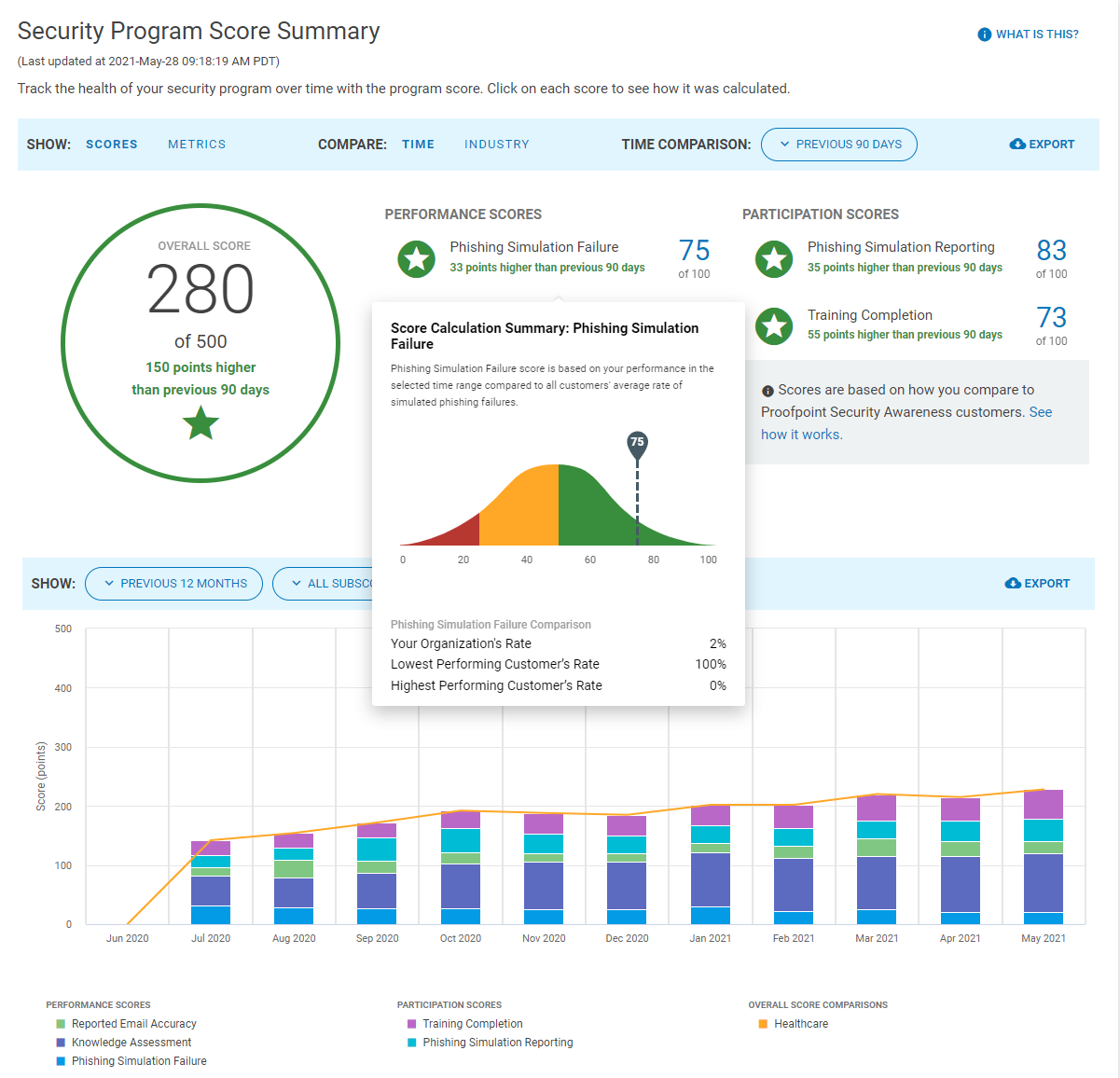
Measuring program success is key to setting regular security awareness baselines. Our unique CISO Dashboard provides metrics, including click rates, reported email accuracy rate, and reporting rates of both simulated and real-world attacks. We help security teams measure program performance over time, and we’re the only vendor who enables organizations to benchmark against their industry peers.
Proofpoint’s holistic approach to security awareness creates a positive feedback loop that helps security teams continuously identify user knowledge gaps, areas of improvement, and empower users to become an effective line of defense.
How we are different
● Drive Security Outcomes with Threat-Driven Content: Proofpoint’s industry-leading threat intelligence provides a unique breadth and depth of knowledge of the ever-changing threat landscape. We incorporate this threat intel into our security education solution, providing users with threat-driven education that matters today. We enable organizations to run simulated phishing attacks based on real-world threats, surfacing real user risk in an organization’s environment. Organizations receive the most up-to-date threats alerts and content, which can be used in user communication, making risk tangible to users.
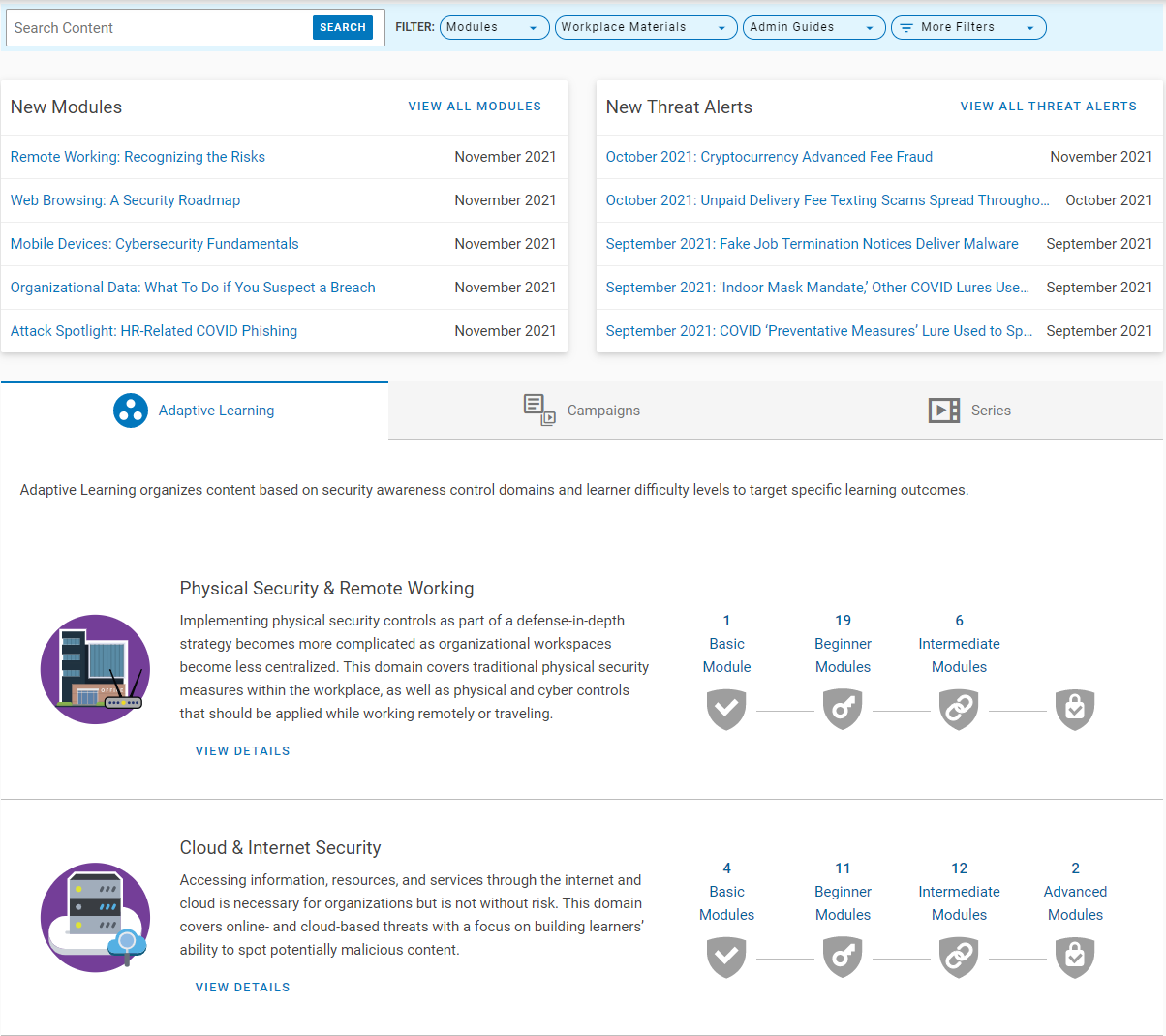
● Keep Users Engaged with Tailored Education: Taking a people-centric approach, Proofpoint first helps organizations identify their vulnerable users. We then provide tailored education with adaptive learning, communication, and behavioral reinforcement to change unsafe behavior. With newly released micro-learning content and adaptive learning framework that are designed to deliver continuous learning, we enable organizations to assign users content centering around their needs to keep them engaged. Organizations can customize curriculum and provide targeted training based on user vulnerability, role, competency, learning style, which supports 40+ languages. Moreover, Email Warning Tags alert users to be more cautious of uncertain emails, providing timely education.
● Provide C-Level Visibility and Automate Threat Response: Proofpoint provides a unique CISO Dashboard to help communicate program performance over time and how it benchmarks against industry peers. It reveals highly vulnerable users by tracking top clickers, Very Attacked People, low participants and performers, allowing organizations to focus their program for better security outcomes. Additionally, users can report email with PhishAlarm button, which kicks off our unique Closed-Loop Email Analysis and Response workflow. User-reported messages are automatically analyzed. When found malicious, they can be quarantined or removed automatically, or with a click. Organizations can customize feedback to users, notifying them the analysis result. This reinforces positive reporting behavior and reduces time and effort responding to threats.


