Photo Gallery
 |
 |
Proofpoint Security Awareness

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| World Region | North America |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
Most threats today are human activated. To protect the organization, security professionals must focus on real business risk — the people who are the most vulnerable targets — and prioritize how to identify and mitigate that human risk.
Proofpoint solves this problem by focusing on and shaping how employees will act when faced with threats. The Proofpoint Security Awareness solution is powered by threat intelligence from 2.6 billion emails that we analyze daily. Using this rich threat intel, we surface an organization’s most attacked and vulnerable people, and deliver targeted education that incorporates threat data to build sustainable security habits.
Our ACE Framework is a holistic approach to people risk reduction: Assess, Change Behavior and Evaluate. We help organizations to assess employees’ vulnerability, change their unsafe behavior, evaluate the program’s effectiveness, and expand and scale that program.
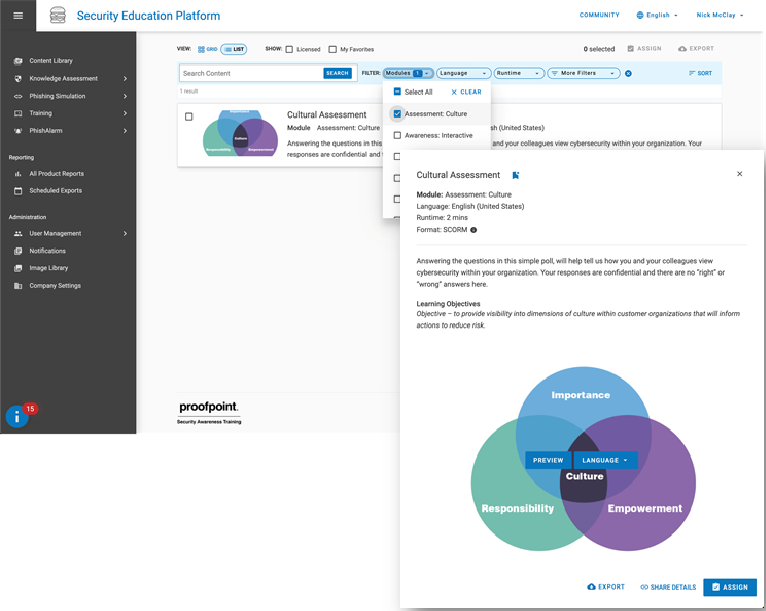
Tailored “micro-learning” teaches positive security habits in easily digestible pieces aligned with each person’s role, vulnerabilities, competency, learning style and language. This approach gives users the right knowledge and skills, and motivates them with engaging, personalized education available in 40+ languages.
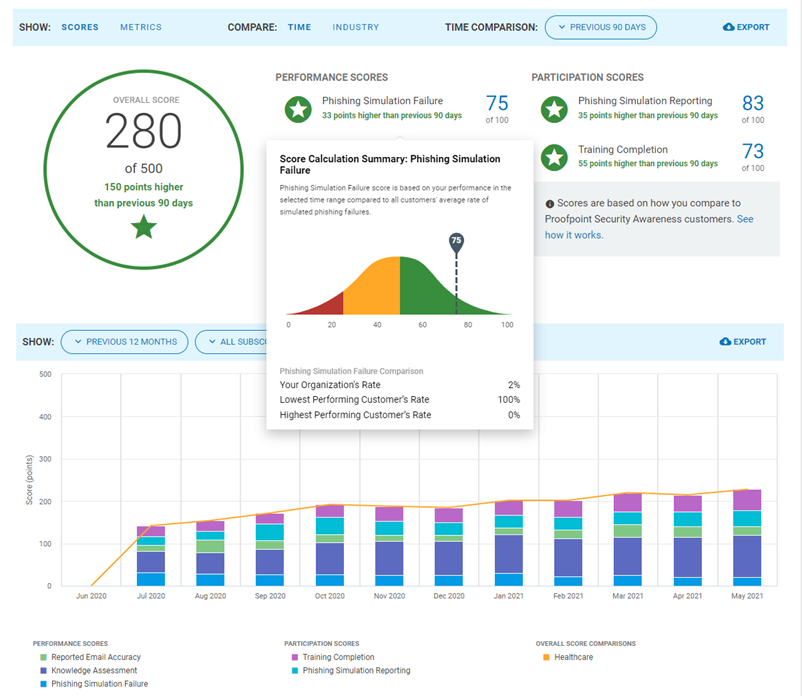
Our solution enhances the administrator experience with automated processes such as delegating multi-tenant roles and investigating user-reported threats. Admins get powerful content filters to easily build specific learning outcomes, and the flexibility to brand and customize their program modules. Measuring program success is key so our unique CISO dashboard tracks behavioral metrics over time, and we’re the only vendor who enables benchmarking against industry peers based on real-world behaviors.
Proofpoint enables organizations to build a strong security culture while expanding their education program. We help uncover what employees believe about security, which is critical to how they will behave in a threat situation. Together we encourage best practices in daily lives that empower them to become an effective line of defense.
How we are different
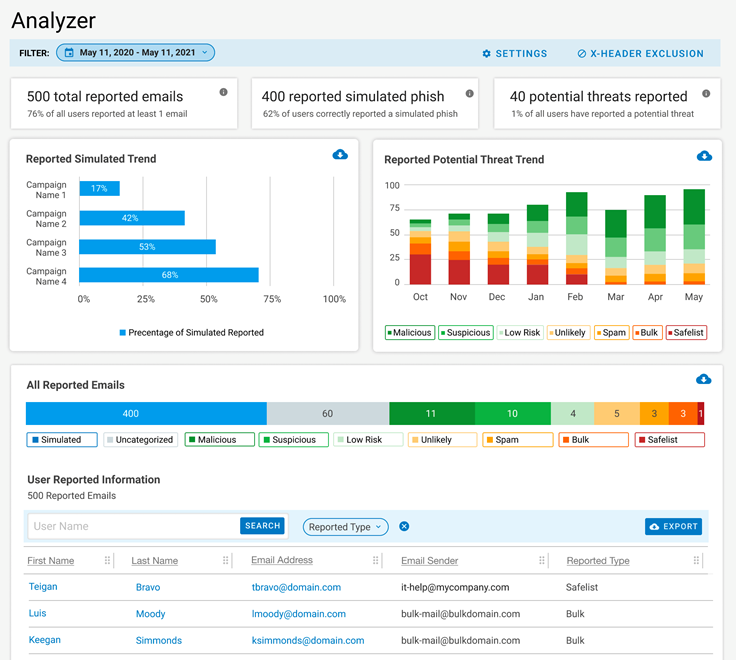
Leverage insight from rich threat intel. Proofpoint incorporates our industry-leading threat intelligence into the Security Awareness solution. No other vendor has the global footprint that gives us deep visibility into the threat landscape. This lets organizations run targeted phishing simulations that incorporate the most up-to-date threat content, so users are practicing with mimics of real-world attack emails. We surface most attacked users and the threats targeting them, so security teams can focus on real risky users and make informed decisions about training that will lower risk.
Change user behavior with tailored education. Proofpoint Security Awareness delivers targeted, personalized education that addresses each person’s unique knowledge gaps. Like the phishing simulations, the educational content is driven by Proofpoint’s threat intelligence about real world attacks. Our micro-learning format delivers short bursts of training that fit into users’ limited time and busy schedules — the opposite of a one-size-fits-all approach — and gives in-the-moment education such as email warnings. Security admins can customize feedback to users who reported suspicious email and automatically notify them about the email disposition, creating a closed-loop response that reinforces positive reporting behavior.
Measure and achieve strong security outcomes. Security teams can track their program’s performance and measure the improvement in user behavior beyond completion rate. Proofpoint customers see approximately 32% accuracy rate in user-reported email, and 36% fewer clicks on real-world malicious links within 90 days. Security Awareness has a powerful CISO Dashboard that gives visibility into the most attacked people and top clickers, as well as low participators and low performers. Security admins can view the program effectiveness over time and benchmark their progress against industry peers. They can report this risk reduction to C-level stakeholders and focus the program for even better security outcomes.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



