Photo Gallery
 |
 |
Proofpoint Security Education Platform

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
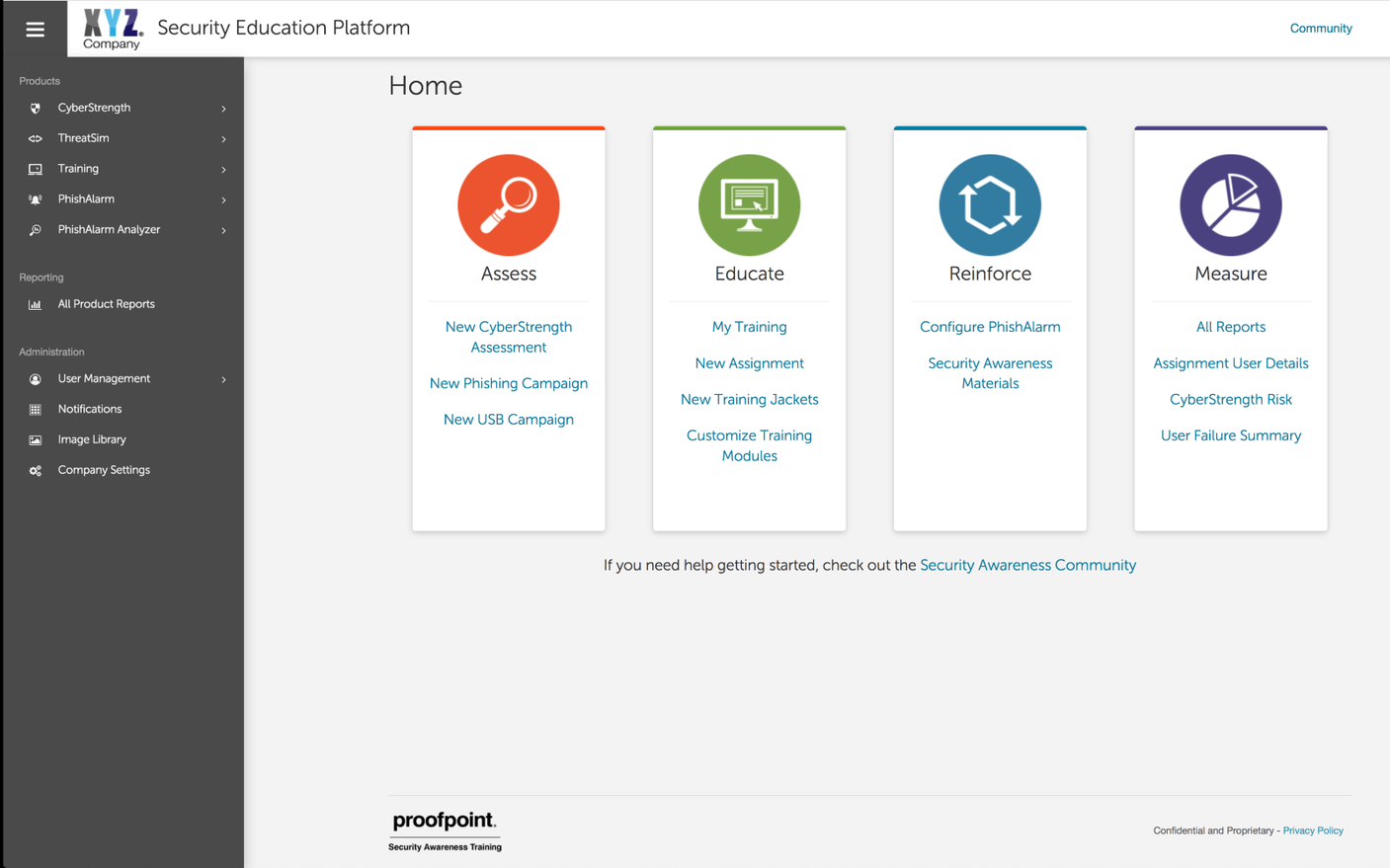
•Flexible ways to manage and track user behavior. The product has multiple ways for administrators to load users into the platform, including built-in user management via CSV as well as integrations with Microsoft Active Directory and Azure platforms. Administrators can add custom properties such as title, manager, or any other property in order to better understand user behavior and important trends in reports.
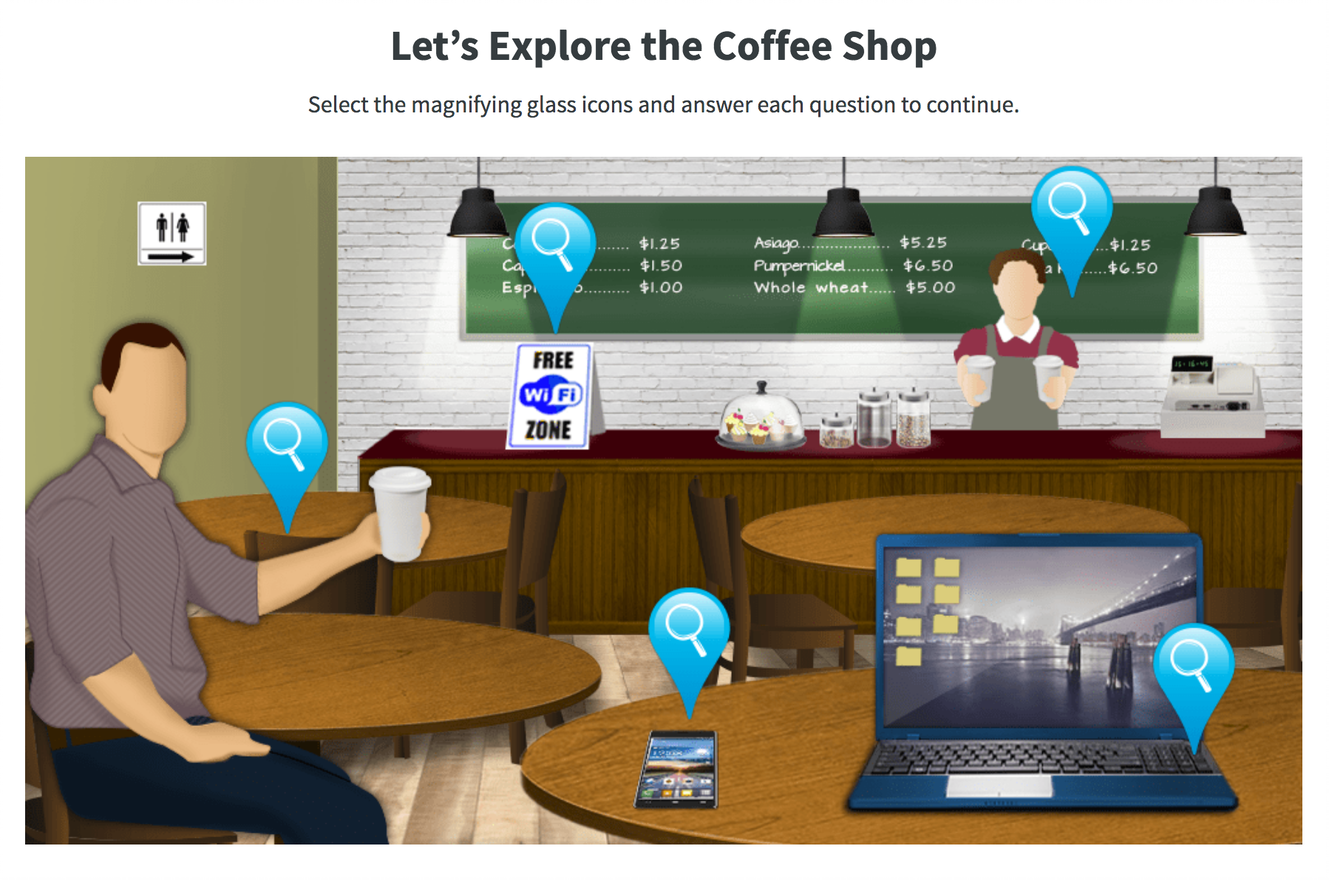
•Engaging content to drive behavior change. Our training modules address critical areas of cybersecurity and compliance and are continuously refreshed based on industry best practices. Training module formats include video, interactive, and game-based modules to cater to all learning styles. With the short 5-15 minute formats of our training, administrators can reallocate their limited 1-2 hour per user per year security awareness training budgets to address new critical user risk needs and maximize the value of user training time. Customers can export the training modules in a SCORM format for use in their own Learning Management System (LMS) at any time.
•Customized training content: Self-service customization of training content via Customization Center allows administrators to modify text, images, screens, questions, and create customized versions of training to improve relevance for their audience. As administrators customize the content the Learning Science Evaluator measures several module qualities and provides you with recommendations to ensure your custom training modules will continue to change user behavior.
•Multinational support for global organizations in 35+ languages with translation, localization, and regional references to improve relevancy for users around the world.
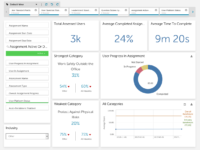
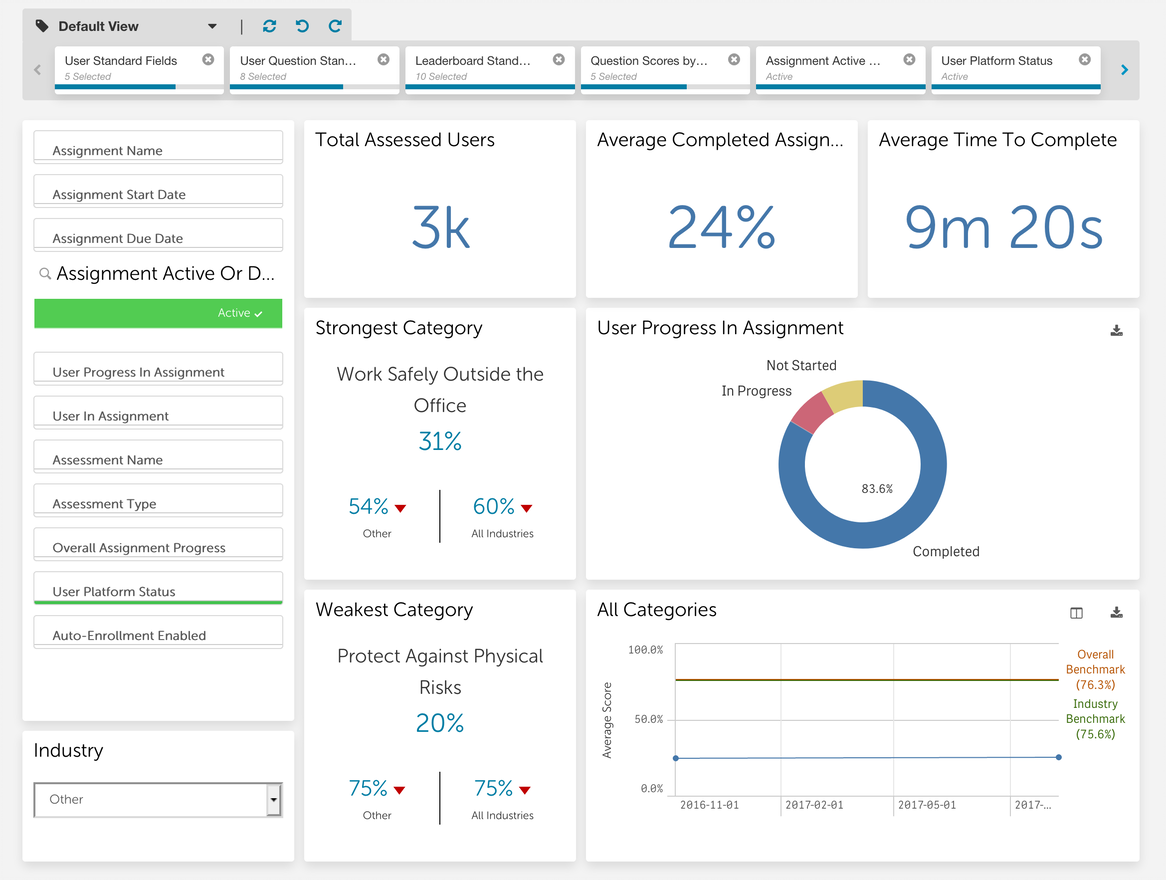
•End user insights for business intelligence: Our reporting provides the ability for administrators to drill down to specific topics and even questions where users are or aren’t performing well. This granular insight allows you to uncover specific strengths and weaknesses of your user base to further refine and build your training program.
How we are different
• We consistently hear from customers who have utilized multiple security awareness training vendors, or even left us before and come back, that users prefer and get the most value out of our Learning Science Principles approach to training modules. This approach keeps users engaged and follows a set of established criteria designed to change behavior and ensure knowledge retention.
•Our ability to allow customers to customize training modules on-the-fly is the most comprehensive in the industry and gives clients the ability to provide their users any content they need while ensuring the efficacy of customized training content being delivered.
•We have several user-specific features to ensure training modules are meeting the needs all users such as mobile-responsive support, pause and resume training, 508 & WCAG 2.0 AA compliance features for low or non-visual users, and 35+ languages translated with localized and regional content such as domains.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



