Photo Gallery
|
Proofpoint Targeted Attack Protection

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
Most ransomware spreads through phishing email. Proofpoint Targeted Attack Protection not only protects against ransomware, it also defends against phishing attacks, advanced email threats delivered through malicious attachments and URLs, and even zero-day threats. With an innovative approach that incorporates multiple detection techniques, it effectively detects, analyzes and blocks ransomware and other advanced threats before they reach end users’ inbox.
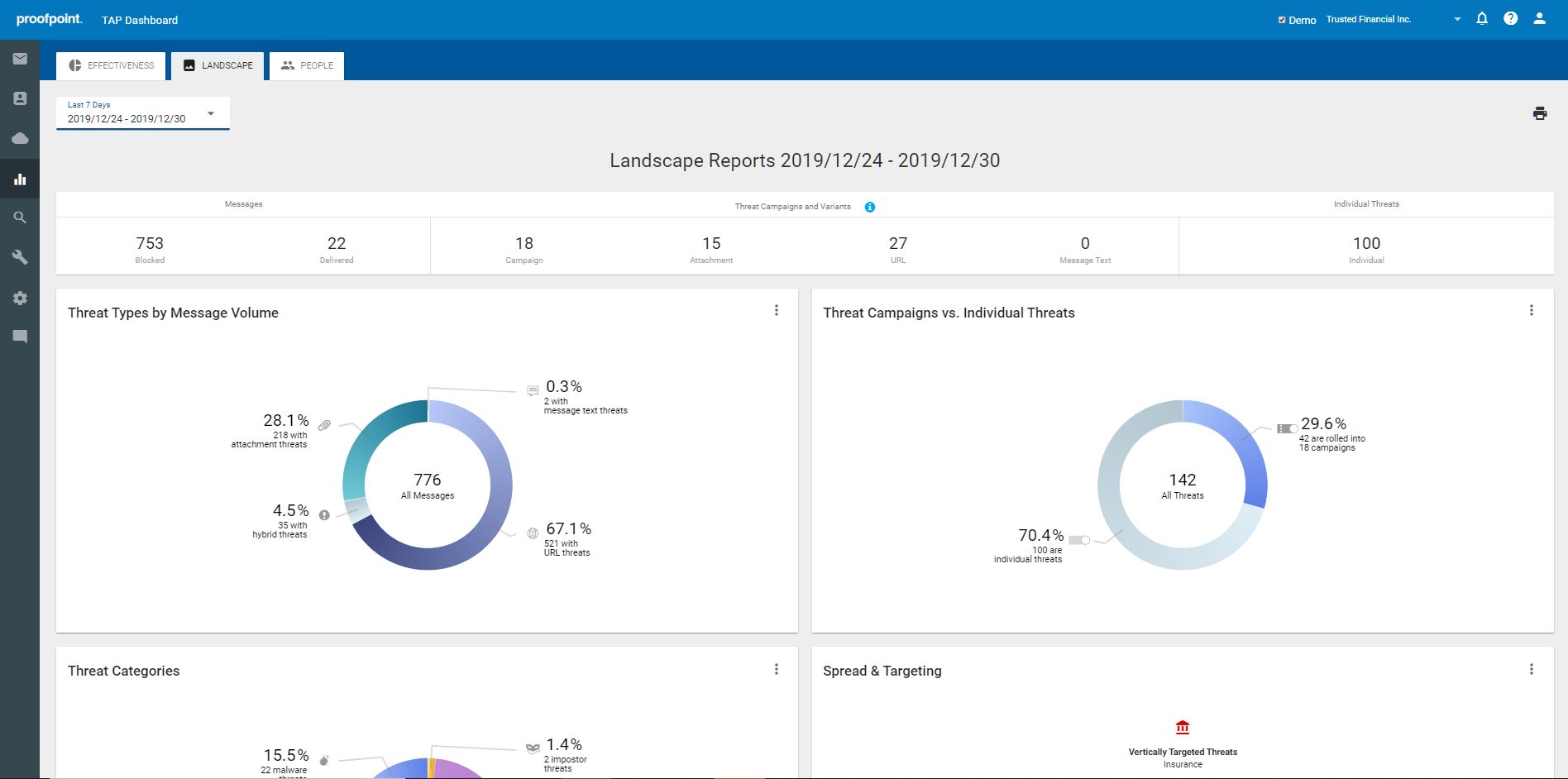
Targeted Attack Protection sees and detects more threats earlier than others. It applies multi-stage analysis to inspect the full attack chain. To better detect ransomware threats, Proofpoint utilizes a combination of static, dynamic and protocol analysis techniques, including multiple machine learning engines spanning threat classification, sender reputation, composite multistage threats, relationship and communication classification and more. By constantly training machine learning algorithms with observed patterns, behavior, and tactics used in each attack, Targeted Attack Protection accurately detects new and emerging threats and leverages that data to inform future detection, making the next attack easier to catch.
Targeted Attack Protection also provides actionable visibility into complex attack campaigns, giving security teams insight around who and what is targeted and how, as well as the threat actors involved and the tools they use. It sees everything – from ransomware and other attacks targeted at the people in your organization, to files in your SaaS file stores for a far-reaching view of the threat landscape.
In addition, Targeted Attack Protection offers a unique Attack Index capability that provides security teams with a people-centric view into their organization’s security posture. It calculates a weighted composite score of all threats sent to an individual within the organization and identifies the very attacked people (VAPs) within an organization. With this unique visibility and insight, security teams can then prioritize the most effective way to mitigate threats and protect their VAPs from ransomware as well as other targeted threats.
How we are different
•Actionable visibility into advanced threats and very attacked people (VAPs): Proofpoint TAP offers unmatched visibility into ransomware, advanced threats, and attackers, through a comprehensive, easy-to-consume dashboard. TAP gives security teams critical insights into their human attack surface – who their most attacked people are, how they’re being attacked and what threat actors are behind those attacks. It provides detailed forensic information on ransomware and other attack campaigns in real time, reducing threat exposure and accelerating threat investigation and response.
•Superior effectiveness in advanced threat detection: Proofpoint leverages an ensemble approach that inspects the entire attack chain using static and dynamic techniques as well as multiple machine learning engines spanning threat classification, composite multistage threats, relationship and communication classification, key employee classification and evolving page design classification.
Our threat graph of community-based intelligence is unparalleled and contains more than 600 billion data points to correlate attack campaigns across diverse industries and geographies. This data pool continually grows as our detection systems also include a worldwide sensor network and one of the largest malware exchanges in the market.
•Detection of threats in cloud apps: Users routinely access and share files stored in sanctioned SaaS services without knowing where they came from and whether they’re safe. Proofpoint TAP surfaces compromised cloud accounts and detects file-based threats in SaaS file stores such Google Drive or Microsoft OneDrive and Sharepoint. As files are added to SaaS services from within your environment, TAP detonates them in our sandbox to observe and analyze. Our multi-layer analysis detects potential threats by examining behavior, code, and protocol in multiple stages through a combination of static and dynamic techniques. Security teams gain visibility into threats hidden in SaaS files including SaaS application hosting the malicious content, the number of threats found and the number of affected users.


