Proofpoint Targeted Attack Protection (TAP) and Threat Response
Photo Gallery
 |
Proofpoint Targeted Attack Protection (TAP) and Threat Response

Additional Info
| Company | Proofpoint |
| Website | http://www.proofpoint.com |
| Company size (employees) | 1,000 to 4,999 |
| Headquarters Region | North America |
| Type of solution | Cloud/SaaS |
Overview
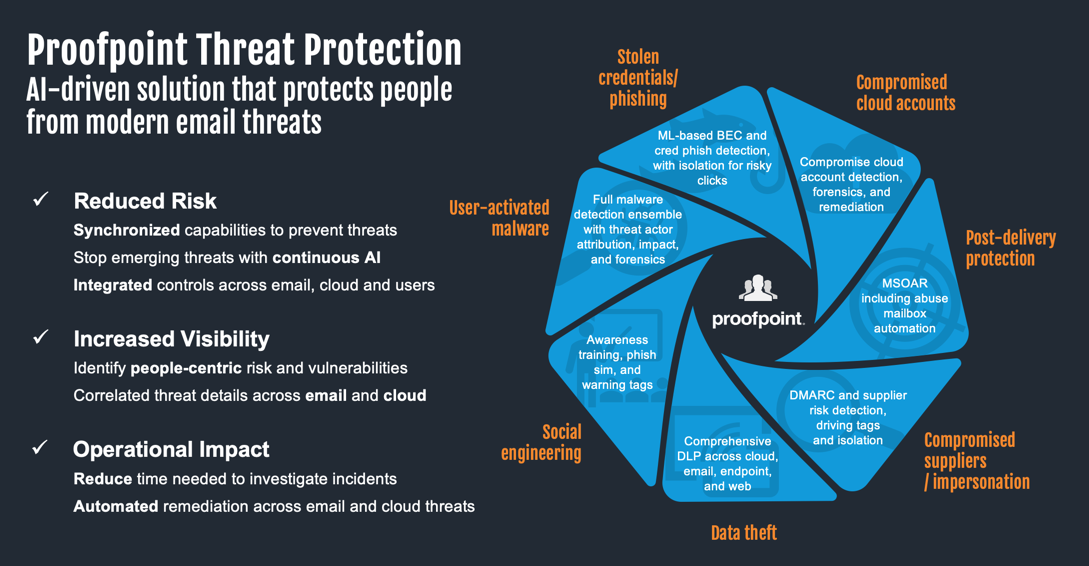
In today’s threat landscape, email remains the primary attack vector, with over 90% of targeted attacks initiated through this channel. Our data shows an average of 66 million Business Email Compromise (BEC) attacks per month, highlighting the ever-evolving tactics employed by cyber criminals.
Proofpoint Targeted Attack Protection (TAP) helps organizations stay ahead of these threats with its innovative approach. TAP goes beyond traditional email security with:
• Proactive Threat Detection: It analyzes and blocks advanced threats, including ransomware, zero-day threats, polymorphic malware, and phishing attacks, before they reach the inbox – regardless of delivery method (malicious attachments, URLs, etc.).
• Adaptive Controls for Risky Clicks: TAP identifies high-risk URL clicks and implements adaptive controls like email isolation, minimizing potential damage if a user interacts with a malicious link.
• Cloud App Threat Detection: TAP extends its reach beyond email by detecting threats and suspicious activity within cloud applications, connecting potential email attacks to broader compromise attempts like credential theft.
By combining advanced detection capabilities with real-time analysis and adaptive controls, TAP provides a comprehensive shield against evolving email threats, safeguarding organizations from the ever-present dangers lurking in the inbox.
Key Capabilities / Features
*Proofpoint TAP: Protecting Users and Stopping Threats Before They Strike*
• Multi-Layered Threat Detection: TAP utilizes a combination of static and dynamic analysis, including sandboxing on various environments, to identify new and evolving threats. This empowers early detection and minimizes the window of opportunity for attackers.
• Machine Learning for Continuous Adaptation: TAP leverages machine learning to continuously analyze attack patterns, behaviors, and techniques. This allows it to adapt and stay ahead of even the most sophisticated threats.
• Comprehensive Threat Coverage: TAP protects against a wide range of threats, including phishing attacks, ransomware, BEC, and cloud-based threats. This unified protection ensures users are safe regardless of the attack vector.
*Proofpoint Threat Response: Streamlining Response and Empowering Security Teams*
• Contextual Threat Intelligence: Threat Response enriches security alerts with crucial data, providing a clear picture of each incident. This empowers security teams to prioritize and respond swiftly to real threats.
• Automated Response Actions: Based on the threat analysis, Threat Response can automatically trigger response actions like email quarantine or user permission adjustments, saving valuable time for security teams.
• Improved Investigation Efficiency: Threat Response simplifies investigations by collecting endpoint forensics and presenting a context-rich view of the attack. This allows security teams to identify key evidence and take informed action.
By combining advanced threat detection with automated response and investigation tools, Proofpoint TAP and Threat Response work together to empower users and simplify security operations. This translates to a more secure environment for users and increased efficiency for security teams.
How we are different
• Unparalleled Threat Intelligence for Superior Protection: TAP leverages the power of the Nexus Threat Graph and NexusAI, fueled by real-time threat intelligence from the most widely deployed security solution across leading global companies (F100, F1000, G2000). This vast network not only protects against email threats but also extends to cloud, network, and social media vectors, providing a holistic view of the threat landscape.
• Unmatched Visibility to Empower Security Teams: TAP delivers unparalleled visibility into both widespread and targeted attacks. It goes beyond simply identifying threats, providing detailed information on threat actors, very attacked people (VAPs), and specific campaigns. Security teams can leverage the Proofpoint Attack Index, a weighted composite score of all threats against an individual within an organization, to identify these VAPs and prioritize security measures to protect them from targeted ransomware and other attacks. This actionable intelligence allows security teams to focus on the most critical threats and respond more effectively.
• Automated Response for Faster Resolution: Many security alerts lack the critical information required to determine the context of a threat and next steps. Proofpoint Threat Response automatically enriches security alerts by collecting important internal and external context, intelligence, and data to create an actionable view of each alert. This insight empowers security teams to quickly understand, prioritize, and respond to security threats. Threat Response automatically checks every domain and IP provided in security alerts and sandbox reports against its built-in premium intelligence feeds. This step removes hours of work and manual one-by-one searching against intelligence services to find attacking IPs and hosts leveraging known bad sites.



