Photo Gallery
 |
 |
Proofpoint Threat Response

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.proofpoint.com |
NOMINATION HIGHLIGHTS
Proofpoint Threat Response streamlines the incident response process through:
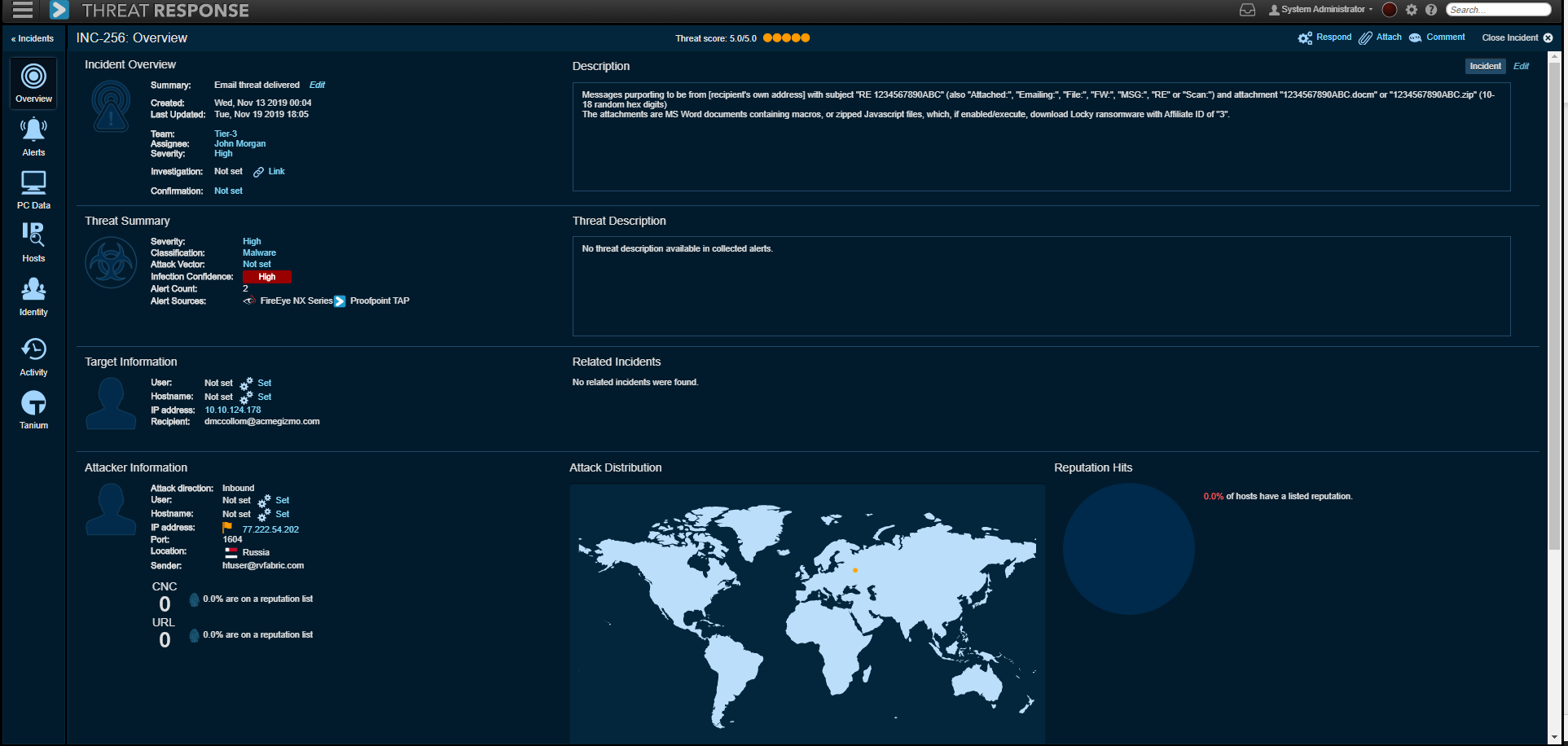
•Automated security alert enrichment: Threat Response can collect any alert from any source and automatically enrich and group them into incidents in a matter of seconds. Security teams receive rich and vital context from leveraging Proofpoint Threat Intelligence as well as third-party threat intelligence such as STIX/TAXII feeds, WHOIS, VirusTotal, Soltra and MaxMind which helps them understand the “who, what and where” of attacks, quickly triage and prioritize incoming events.
•Automated or customized response actions: Based on the context and forensics collected and analyzed by the system, Threat Response presents a context rich view of that threat. This view allows analysts to take push-button response actions, identify areas for additional investigations or turn on automated response such as retract delivered email from users’ mailboxes, add users to low permission groups, update blocklists of firewalls and web filters and much more. Contain the threat by blocking/quarantining threats across Exchange, Firewalls, EDR, Web Gateway, AD, NAC and other solutions
Proofpoint Threat Response enables messaging and security administrators to move malicious or unwanted emails to quarantine, after delivery. It follows forwarded mail and distribution lists and creates an auditable activity trail. Proofpoint Threat Response provides graphical reports showing email alerts, post-delivery quarantine attempts, and success or failure of those attempts. This saves time and frustration, and with the added benefit of showing message ‘read’ status, TRAP additionally helps prioritize which users and endpoints to review.
Threat Response works in many IT Security and Security Operations Center environments – small, medium, or large. It can be customized and extended to meet customers specific needs through rich API functionality and supports customizations and integrations through the following options: List Management API, Incident API, Custom Response API, JSON Alert Source, ETL Scripting and custom Powershell Scripts.
How we are different
•Proofpoint is the only cybersecurity vendor that has taken a people-centric approach to security and offers solutions that address the changing landscape that is increasingly targeting people rather than infrastructure. Proofpoint Threat Response reports provide granular insight into targeting of internal users, including past histories that display which users have been targeted the most frequently over customizable time periods. Similarly, targeting of departments, groups, or geographic locations are also available as reports.
•Many security alerts lack critical information required to determine the context of a threat and next steps. Threat Response automatically enriches security alerts by collecting important internal and external context, intelligence, and data to create an actionable view of each alert. Armed with this insight, security teams can quickly understand, prioritize, and respond to security threats.
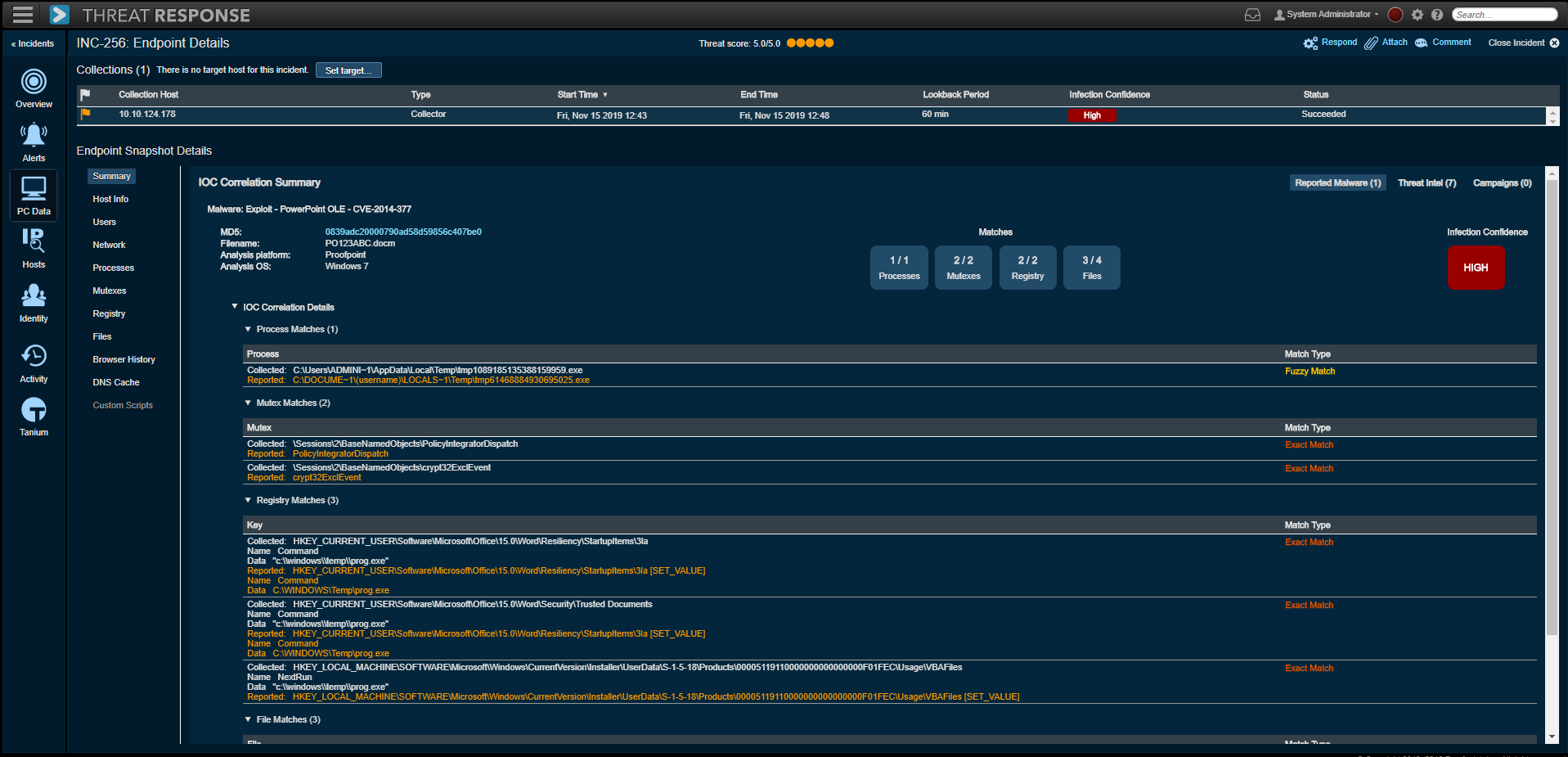
•When a security alert reports a system has been targeted with malware, Threat Response automatically deploys an endpoint collector to pull forensics from the targeted system. This data is compared to a database of known IOCs to quickly confirm whether a system is infected with IOCs related to the current attack. Teams can also gain visibility into IOCs from previous attacks that were not cleaned up. This built-in infection verification can save hours per incident. And it dramatically reduces the number of time-wasting false positives that lead to needless reimaging and backup-restoration cycles.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



