Photo Gallery
 |
Proofpoint Zero Trust Network Access

Additional Info
| Company | Proofpoint |
| Company size | 1,000 - 4,999 employees |
| Website | https://www.proofpoint.com/us |
NOMINATION HIGHLIGHTS
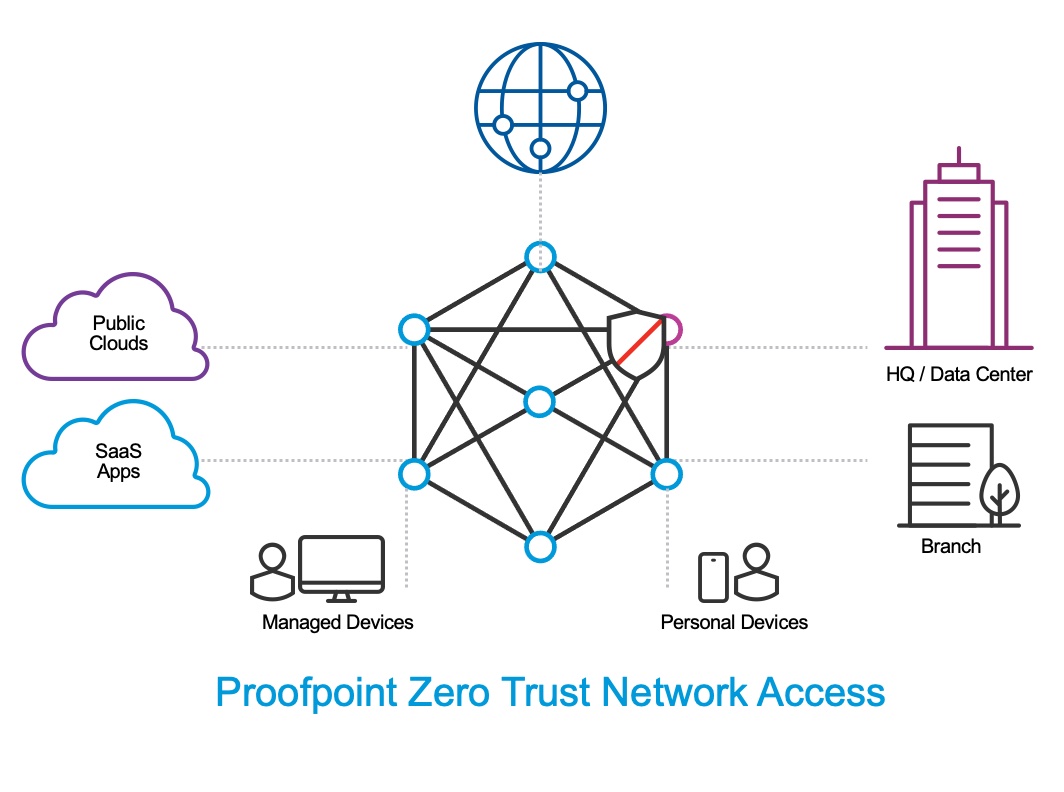
Proofpoint Zero Trust Network Access (ZTNA) delivers user-centric computing to enterprises. It is an overlay network that is global and multi-tenant. However, it functions as a private enterprise-wide area network for each customer’s organization. The infrastructure of this network is provided by Proofpoint ZTNA in the cloud, so there is no hardware to deploy. ZTNA has a dense network of points-of-presence (POP) around the world. End-users, legacy data centers, branch offices, and clouds all connect to ZTNA via the nearest local POP.
There are two ways that users connect to ZTNA. One is an always-on VPN-based connection, which is recommended for managed corporate devices. The other is browser-based secure remote access, which is most appropriate for personal devices, as well as contractors, partners, and consultants. All user traffic—WAN, LAN, and internet—flows through this network, where it is secured and audited. Internet traffic breaks out at the local POP.
From a technology perspective, this network serves as a distributed identity-based router that Proofpoint ZTNA deploys in the cloud. Policies abstract physical topology and deal with users and resources. ZTNA is built upon a zero-trust architecture where each user is bound by a software-defined perimeter. Each user has a unique, fixed identity – irrespective of rom where they connect to the network. The software defined perimeter security framework allows one-to-one network connections that are dynamically created on-demand between the user and the specific resources they need to access. All other resources are invisible to the user. Access is impossible unless it is explicitly granted, and continuously verified at the packet level. This model effectively provides organizations with dynamically-provisioned secure network segmentation.
How we are different
● Proofpoint Zero Trust Network Access (ZTNA) is highly scalable and based upon a Software Defined Perimeter / Zero Trust architecture. It is designed to handle large complex routing and DNS environments. All enforcement is done in the cloud and applied directly at the user's identity level. (ZTNA does not rely on network or IP address to make traffic enforcement determinations).
● Proofpoint ZTNA's backbone is entirely IPv6 native, which allows it to perform and enforce inspection of traffic at every level. User's identities are embedded into IPv6 frames end-to-end inside the ZTNA backbone.
● Customers can employ Proofpoint ZTNA in conjunction with their existing security stack. ZTNA routes user traffic to specific egress points defined by the customer.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



