Photo Gallery
 |
Radiant Security AI-powered SOC Co-pilot

Additional Info
| Company | Radiant Security |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://radiantsecurity.ai |
NOMINATION HIGHLIGHTS
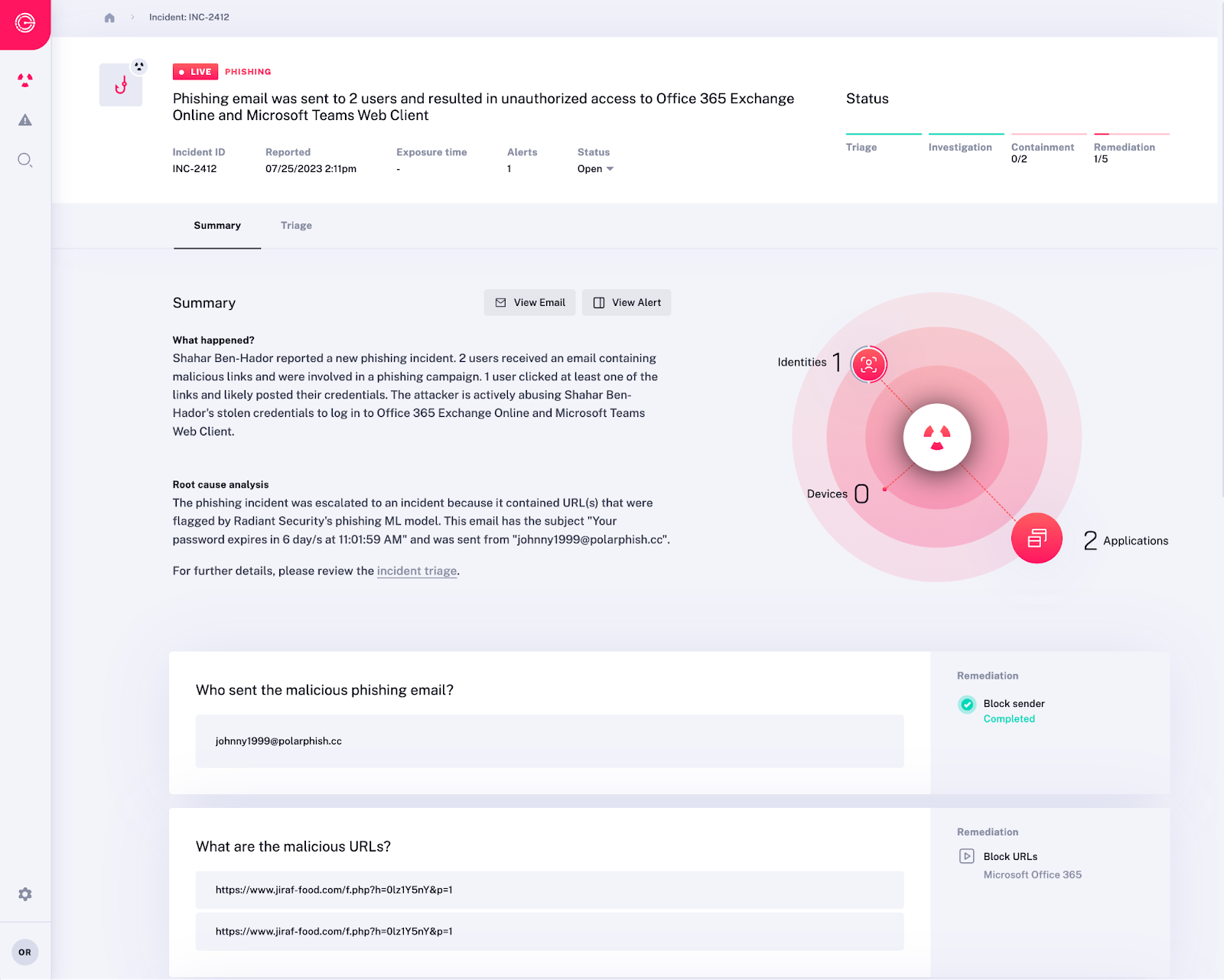
Radiant Security’s SOC Co-pilot is a state-of-the-art platform designed to augment Security Operations Centers with the power of artificial intelligence. It optimizes the SOC workflow by automating the tedious yet critical tasks of alert triage, in-depth investigation, and incident response. In doing so, it allows SOC teams to focus on more strategic activities, amplifying productivity and efficiency.
The SOC Co-pilot represents a significant leap in SOC management. Through intelligent automation, it directly targets and alleviates critical challenges, offering an efficient and robust solution to the ever-increasing complexities of cybersecurity.
Key Capabilities / Features
The Radiant Security SOC Co-pilot boosts analyst productivity through unlimited in-depth investigation, rapid response, and intelligent automation:
- Automated Triage & Investigation: By using AI, Radiant can manage time-consuming tasks, ensuring no attacks slip through the cracks.
- Detecting Real Attacks: Radiant deepens investigations to uncover real incidents, understand their root cause, and track attacks wherever they go.
- Responding Rapidly: With intelligent automation, Radiant can create a response plan, automate or manually perform corrective actions, and allow one-click remediation.
- Empowering Junior Analysts: Radiant acts as a co-pilot to enable entry-level analysts to become valuable contributors by automating triage, investigation, and offering step-by-step guidance.
How we are different
Unlike traditional SOC solutions and incident response platforms, Radiant Security's SOC Co-pilot goes several steps further by incorporating AI-powered automation into every aspect of the SOC workflow. It offers unparalleled precision with an accuracy rate consistently in the high 90% range, surpassing most human analysts. This not only accelerates the incident response times but also allows for in-depth investigations around the clock, setting a new standard in cybersecurity operations.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



