Photo Gallery
 |
|
Rapid7 InsightIDR


Additional Info
| Company | Rapid7 |
| Company size | 850 employees |
| Website | http://www.rapid7.com |
NOMINATION HIGHLIGHTS
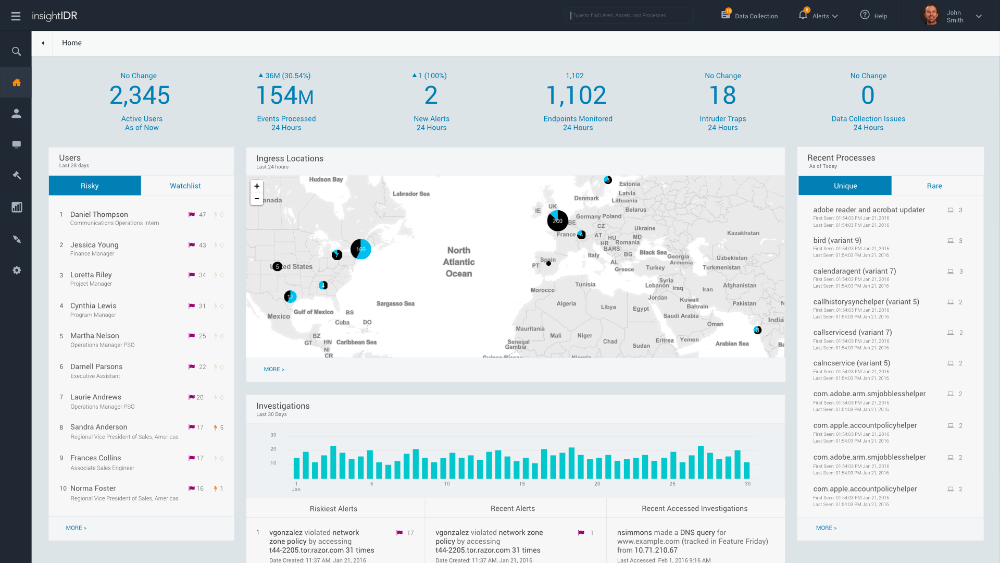
Two decades ago, SIEMs were born from the need to manage and analyze all of the rich data being generated by infrastructure and centralized servers. However, intelligently correlating this data to detect compromises and risky behavior has been an afterthought. Security teams are trapped under a mountain of vague alerts. InsightIDR was built hand-in-hand with security teams to integrate with existing network and security stacks and provide visibility across the ecosystem.
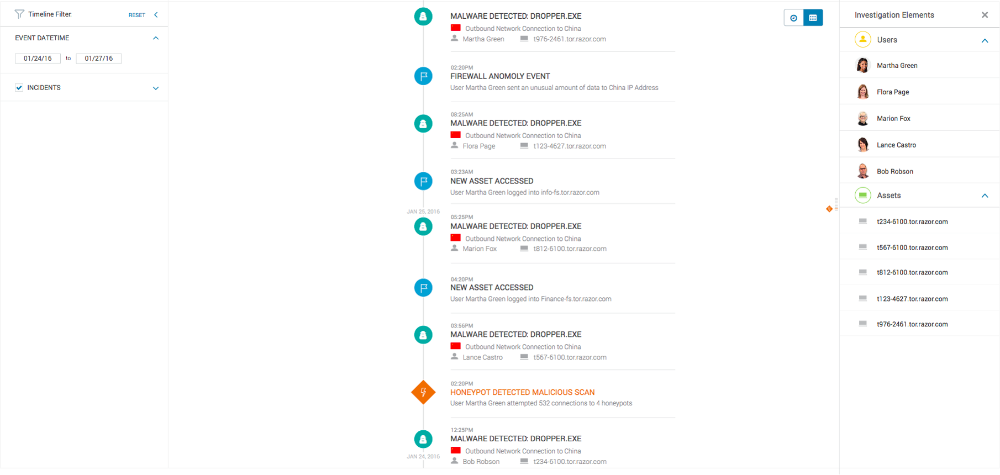
InsightIDR helps find unknown threats with User Behavior Analytics (UBA) and deception technology, provides SIEM capabilities to prioritize where to look, and combines the above with Endpoint Detection and visibility to leave attackers with nowhere to hide. Security teams no longer need to write detection rules or hire certified data splunkers to get the answers hidden in user activity, logs and endpoints. Customers report that their investigations are 20 times faster as they can bring together real-time log search, user activity and endpoint data in a single solution.
Unlike other SIEMs, InsightIDR has user behavior analytics (UBA) and endpoint detection and response (EDR) as core components in the solution. From inception, InsightIDR was built on elastic compute and big data technologies, so customers get up and running faster, never have to worry about scaling or architecture, and never have to tap the networking team for help accessing systems from home late at night.
How we are different
Rapid7 InsightIDR offers a number of business and technical advantages to companies, including:
• Reliable Incident Detection – Fully integrated User Behavior Analytics detect the top attack vectors behind breaches on endpoints and in cloud environments. Automated deception technology detects attacker behaviors that will never appear in logs.
• Full Data Collection & Search – Junior analysts can search the data from across their entire environment without the need to learn logging syntax or perform translations to a common format.
• Compliance Across Modern Environments – Customers can create custom compliance cards to easily fulfill auditor requests. Unified endpoint monitoring and cloud auditing integrations make it easy for security teams to report on any events, whether the data is on endpoints, in centralized logging or in cloud environments.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



