Photo Gallery
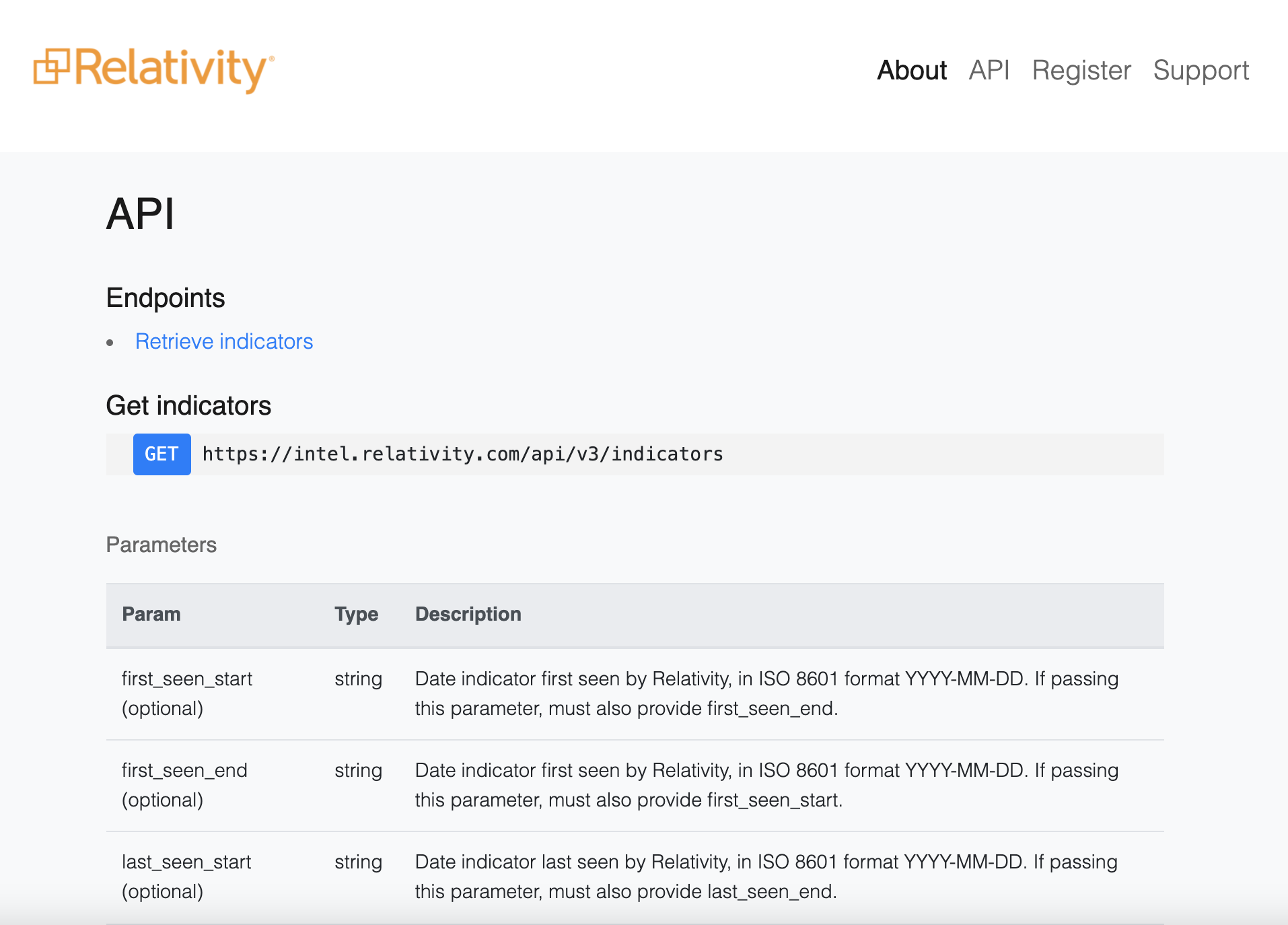 |
Relativity's Threat Intelligence Feed

Additional Info
| Company | Relativity |
| Company size | 1,000 - 4,999 employees |
| Website | http://www.relativity.com |
NOMINATION HIGHLIGHTS
Relativity’s threat intelligence feed is for any legal or legal-adjacent professional wanting to collect Indicators of Compromise (IOCs) in order to build or improve their security program. Intelligence is aggregated from several sources, including the RelativityOne environment, our network of legal-specific honeypots, and open-source intelligence feeds. The feed is maintained by Calder7, Relativity’s in-house security team.
How we are different
• It’s closing the threat intelligence gap in the growing legal tech industry and protecting the greater public in the process. The best security is preventative and is designed to stop attacks before they happen. The Threat Intelligence Feed gives both Relativity customers and the public alike empowerment in this ongoing battle to protect their fortresses. The solution currently tracks nearly 30,000 indicators of compromise and is updated hourly, all pulled from data sources in RelativityOne authentication and firewall logs, legal specific honeypots, and the International Information Systems Security Certification Consortium.
• It helps make security knowledge more accessible and increases overall security awareness. The Threat Intelligence Feed is a free and easy-to-use tool that provides organizations with greater awareness of the security threats around them and helps bolster their security posture from external threat actors. Additionally, it’s easily accessible and can be used to plug into any tools supporting feed API ingestion, including SIEM, firewall, TIP, SOAR and more in order to identify suspicious activity.
• It’s the first of its kind. Relativity’s Threat Intelligence Feed is the only security feed dedicated to the legal tech industry. It's a challenge to find applicable intelligence sources that specialize in reporting threats that target specific business verticals such as legal and legal-adjacent entities. Leveraging threat intelligence, particularly around known threats targeting legal entities, can help organizations improve their ability to prevent, detect and respond to potential threats within their network.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



