Resecurity’s Data Driven Threat Intelligence Platform Context™
Recognized in the Category:
Photo Gallery
 |

 |
Resecurity's Data Driven Threat Intelligence Platform Context™


Additional Info
| Company | Resecurity, Inc. |
| Company size | 50 - 99 employees |
| Website | http://www.resecurity.com |
NOMINATION HIGHLIGHTS
It’s not enough to know what’s happening IN your network. Organizations need offensive intelligence about what’s happening outside their environment. New threats and security challenges require effective tools for timely identification and in-depth analysis. Without proper contextualization, an overload of raw intelligence becomes a burden, leading to lack of actionable data and incorrect resource planning, increasing the probability of risk and negative outcome. Aimed at intelligence analysts, investigators, SOC/DFIR teams, risk management and C-level security executives, Context™ is an intelligence platform, enabling enterprises and governments to accelerate analysis, prevention and investigation workflows with the goal of discovering valuable insights, and supporting better decision-making, using lightning-fast search and data science.
Use cases:
● Anti-Piracy. Holistic approach to piracy and counterfeit monitoring for various industry verticals. Prevent illicit distribution/product use, using actionable intelligence.
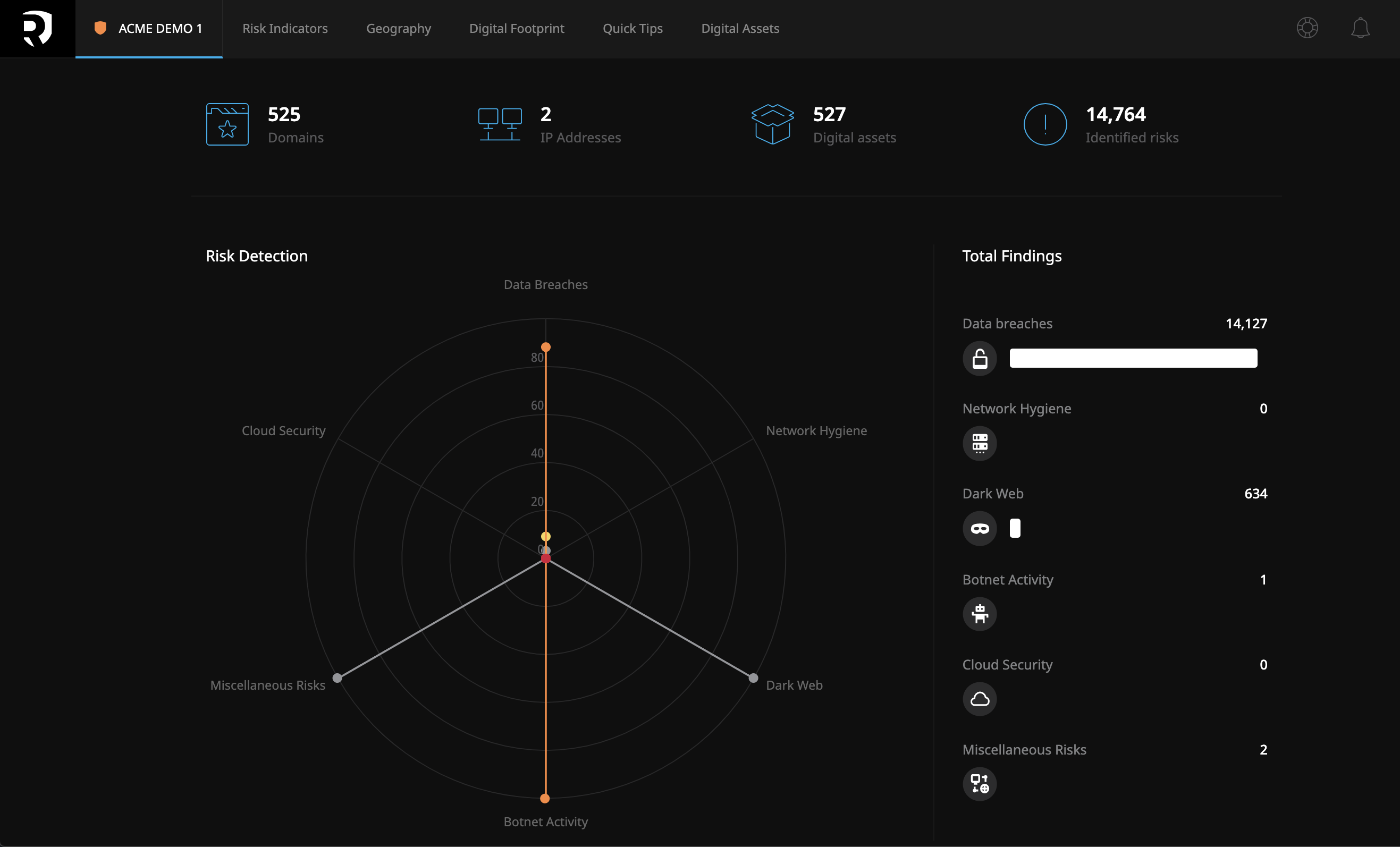
● Data Breach Intelligence. Identify exposure of sensitive data (i.e, intellectual property, confidential documents, customer/employee data). Prevent data breach risk in your infrastructure/clouds.
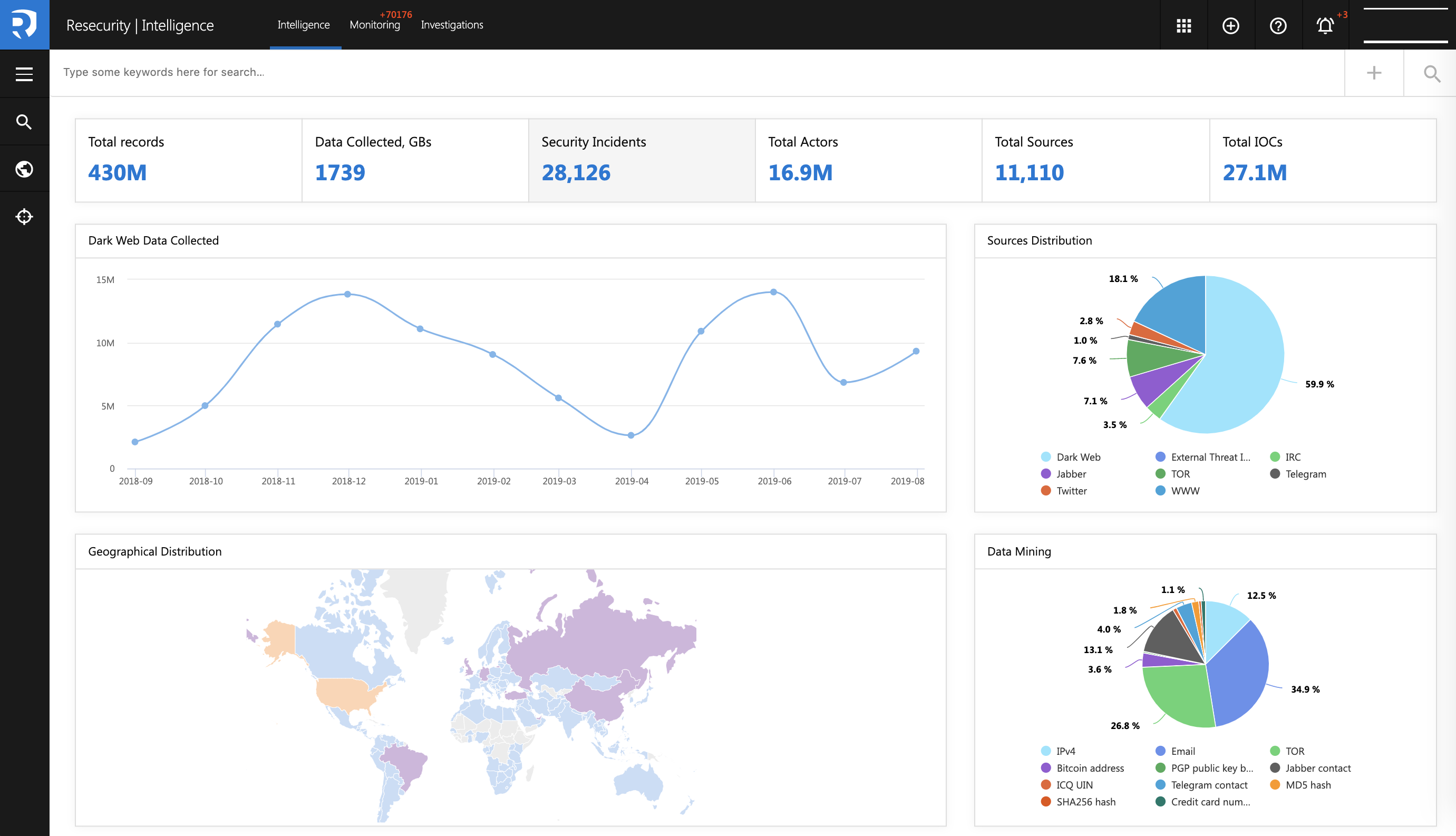
● Dark Web Monitoring. Lightning-fast search in the internet’s darkest corners. The biggest—and continuously updating—repository of underground communities and marketplace.
● Digital Risk Monitoring. Inventory digital assets and control risk across a variety of digital channels. Set up your digital-footprint settings and get early-warning notifications.
● Fraud & Risk Intelligence. Discover fraudsters and cybercriminals’ latest tools, tactics and procedures targeting your enterprise. Use our SDK and the REST API in your apps/services to strengthen anti-fraud.
● Investigations. Built-in case management system tracks subjects of interest in real time and centralizes collected intelligence with proper tagging and context for further analysis.
● Security Intelligence. Manage multiple internet and external threat-intelligence feeds; enrich circulating threat telemetry in your SOC/SIEM/TIP for strategic decision-making and proactive incident response.
● Brand Protection. Protection from abuse, reputational risks, copyright infringement and intellectual property violation. Minimize brand damage, loss of revenue and customer trust.
How we are different
1. Resecurity knows what information organizations need to protect themselves and how to ensure it’s accurate, timely, and relevant. Many threat-intelligence offerings provide large data lakes but no way to prioritize what’s important. Context™ combines cyber-threat intelligence harvested from millions of data points with data science to extract current, objective, and actionable insights; geo-location capabilities deliver contextual information identifying low-, medium- and high-risk areas for managing infrastructure, network resources and other assets; and case management.
2. Context™ draws on data comprising more than 5 billion threat artifacts (indicators of compromise and attacks, tools, tactics, and adversary procedures) with valuable meta-data stored in historical form used for deep-dive investigations; 9 million threat-actor profiles collected from various underground communities and criminal marketplaces, intelligence reports, and security-expert community with associated metadata; 300M+ fully indexed and translated Dark Web data entries with extracted artifacts, graphical screenshots and links visualization; 40 languages with a built-in, offline translation solution and unique linguistic expertise to provide details on threat actors’ chatter; and a constantly updated repository of 20,000 Dark Web sources.
3. Context™ is based on the Intelligence Cycle—a classic six-step process used by government agencies and industry experts, providing a balanced, comprehensive approach to intelligence gathering and analysis: a) Planning: Receives subjects of interest from user, enabling criteria definition and directions for further intelligence collection. b) Collection: Harnesses constantly-expanding cloud of indexed threat artifacts and associated adversaries collected from public/private sources. c) Processing. Converts vast amount of collected information to a form usable by analysts through decryption, language translations, and data reduction. d) Analysis/Production. For organizations to make timely, strategic decisions, intelligence must be current, objective and actionable with enough context for interpretation. e) Dissemination. Flexible workspace for collaboration between team members and internal case- management system to store/distribute the final intelligence product. f) Evaluation.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



