Photo Gallery
 |
ReversingLabs

Additional Info
| Company | ReversingLabs |
| Company size | 100 - 499 employees |
| World Region | North America |
| Website | https://www.reversinglabs.com/ |
NOMINATION HIGHLIGHTS
According to a Gartner® report, Mitigate Enterprise Software Supply Chain Security Risks, “Software supply chain attacks have seen triple-digit increases, but few organizations have taken steps to evaluate the risks of these complex attacks.” Next, the report states, “The lack of transparency and trust within the global software supply chain has emerged as a critical issue for organizations of all kinds.”
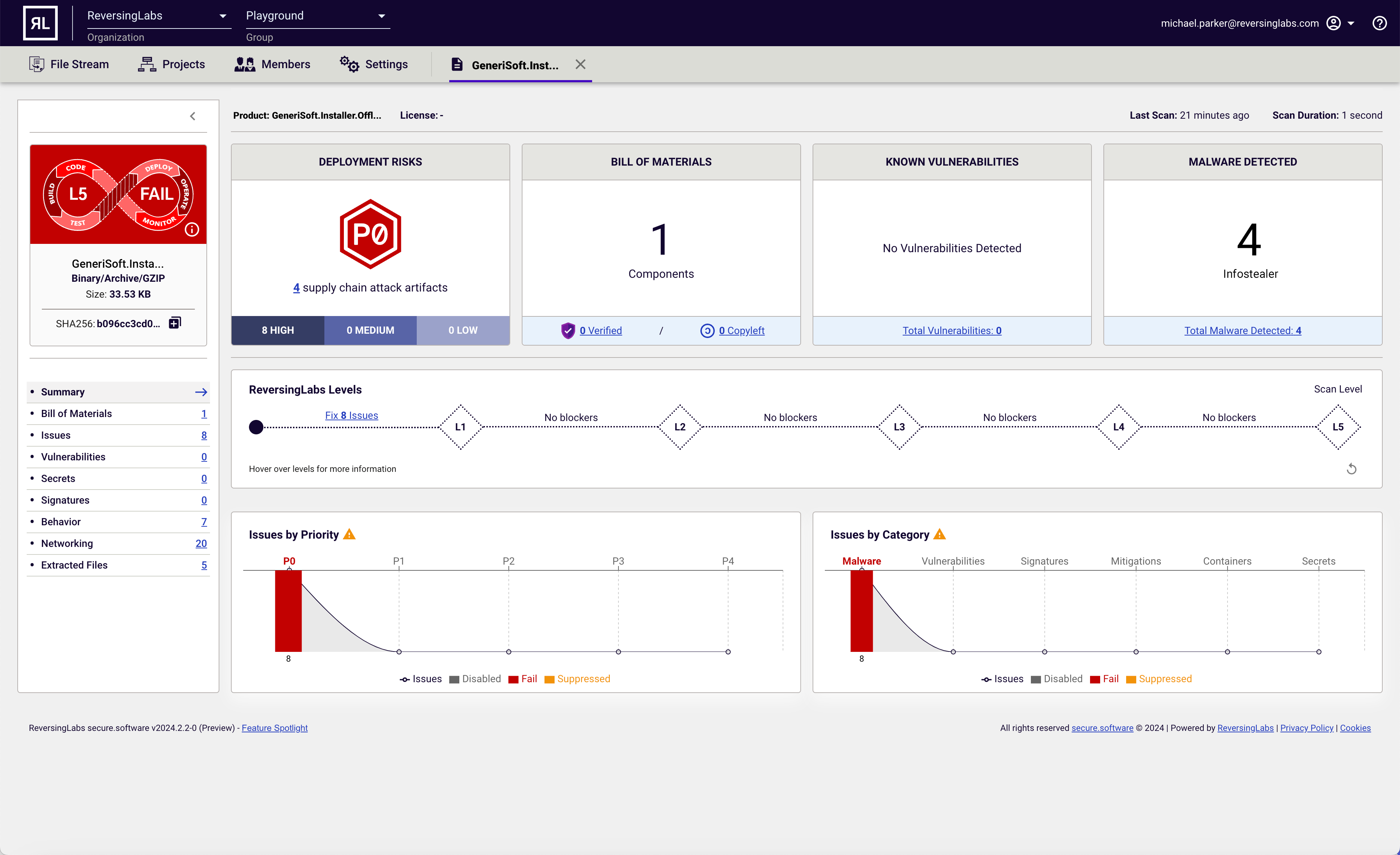
ReversingLabs Spectra AssureTM identifies and stops software supply chain attacks with the industry’s only AI-driven Complex Binary Analysis that does what other application security tools cannot – identify malware, tampering, exposed secrets, vulnerabilities, weak mitigations, and more.
ReversingLabs (RL) recognizes that software represents the largest under-addressed attack surface, impacting software producers and enterprise buyers. This is because traditional AppSec testing solutions (e.g., SAST, SCA, or DAST) are limited—they are not designed to identify malware or malicious components, cannot analyze the entire software binary delivered for deployment, and in the case of SCA, only focuses on open-source software. As a result, organizations relying on these tools develop blind spots.
Trusted by companies like SolarWinds, Forescout, and ExtraHop, Spectra Assure is the comprehensive build exam to identify malware and tampering before release or deployment – without the need for source code or dynamic testing. Spectra Assure provides a complete analysis of the software package, including first, second, third-party, and open-source components for threat detection. It can track known malicious behaviors, suspicious behaviors, as well as behavior changes resembling past attacks, to detect and stop novel software supply chain attacks. As a result, Spectra Assure answers two fundamental questions for those shipping or deploying software:
How do you know when your software has been compromised or tampered with?
How do you know when your software is malware?
Key Capabilities / Features
Spectra Assure includes the following capabilities:
AI-Driven Complex Binary Analysis: Provides Spectra Assure with the ability to find and address risks and threats undetectable by legacy AppSec and vendor acquisition tools. Fast and comprehensive, this process takes as little as minutes (e.g. 1GB in 5 minutes), reducing the impact on developer or risk managers.
Find and mitigate threats undetectable by legacy AppSec and vendor acquisition tools with the industry’s first and only AI-driven complex binary analysis powered by the world's largest threat repository of 40B searchable files. With these capabilities, teams can see deeper into software packages and quickly process large and complex software packages - without the need for source code.
Malware and Threat Detection: Identify tampering, malware, and more with a threat intelligence database covering 40 billion files with 16 proprietary malware detection engines to prevent advanced threats from spreading throughout the software supply chain. Spectra Assure highlights real, exploitable software supply chain threats with actionable alerts curated by a team of expert threat researchers.
Tampering Identification: Only Spectra Assure tracks known malicious behaviors, suspicious behaviors, as well as behavior changes resembling past attacks, to detect and stop novel software supply chain attacks.
Secrets Detection: Efficiently remediate exposed secrets detected in the final build with automated prioritization of active SaaS credentials and noise reduction powered by threat repository data.
Comprehensive and actionable Software Bill of Materials (SBOM): Provides a comprehensive SBOM and inventory of all artifacts (proprietary, commercial, open-source, and more) added to software packages during the final build or release process, supporting CycloneDX or SPDX formats.
How we are different
Only Spectra Assure Can See and Stop Software Supply Chain Attacks. It goes beyond traditional legacy AST tools to find malware, malicious code, unauthorized changes in software behaviors, signature tampering, exposed secrets, and other threats because it sees the whole software binary - the proprietary, commercial, open source code, and artifacts included in the build. In minutes, Spectra Assure can identify critical threats and material risks. Integration with CI/CD automation and/or pre-deployment testing tools can halt the process when malicious changes are detected or upon failure to meet customized policies aligned with the organization’s risk appetite.
Only Spectra Assure Has AI-Driven Complex Binary Analysis, which processes large, complete software packages without the need for source code, which is typically unavailable to software buyers wanting to manage third-party risk. This process identifies and analyzes the risks in commercial, proprietary, and open-source code, along with all artifacts and components added as part of the build process that others cannot. It also features automatic differencing across any two software versions:
Reports changes in risk categories, and issue counts between versions to validate that remediations were implemented and no new risks were added between the builds.
Uncovers behavior changes across multiple software versions, often the only way to detect sophisticated, targeted attacks or new malware.
Confirms CI/CD process integrity by checking for behavioral differences across two or more builds of the same software version.
Spectra Assure Has the Largest File Threat Repository, which makes 40+ billion searchable pieces of malware, goodware, and attack intelligence available to customers—eight times larger than the closest offering. This data powers RL’s AI learning processes for continually improving decision-making, and component identification (threat classification and prioritization). The repository also ingests data from 15+ million scans conducted daily across 400 types of binaries and 4,800 file formats.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



