Photo Gallery
 |

 |
ReversingLabs Managed Software Assurance

Additional Info
| Company | ReversingLabs |
| Company size | 100 - 499 employees |
| Website | http://www.reversinglabs.com |
NOMINATION HIGHLIGHTS
Companies producing software critical for their business or for customers are under attack. Cybercriminals and nation-state actors have expanded their operations from corporate networks and data centers to software development organizations and supply chains. The 2020 SolarWinds SunBurst attack is the highest-profile example of this shifting threat landscape, it’s hardly the only one.
Today enterprises cannot assume that software applications and updates from their providers are safe or secure. This includes both licensed third-party and open-source software, which are used everywhere to facilitate and accelerate the creation of new applications and services. This is why companies that develop software, as well as their customers, must make the security of their software supply chain a top priority.
Following the 2020 incident, SolarWinds approached ReversingLabs to help it assess and recover from the attack. Accepting the challenge, ReversingLabs quickly identified the source of the incident: compiled software binaries compromised with so-called “back doors.” Existing application security solutions couldn’t detect these malicious components because they lacked the ability to analyze all components and software layers.
Recognizing that software supply chain risks were widespread, ReversingLabs introduced its Managed Software Assurance Service to assist other companies in mitigating supply chain risks. This new offering uses ReversingLabs’ extensive repository of malicious code research and threat intelligence to identify threats in software BEFORE it is released to customers.
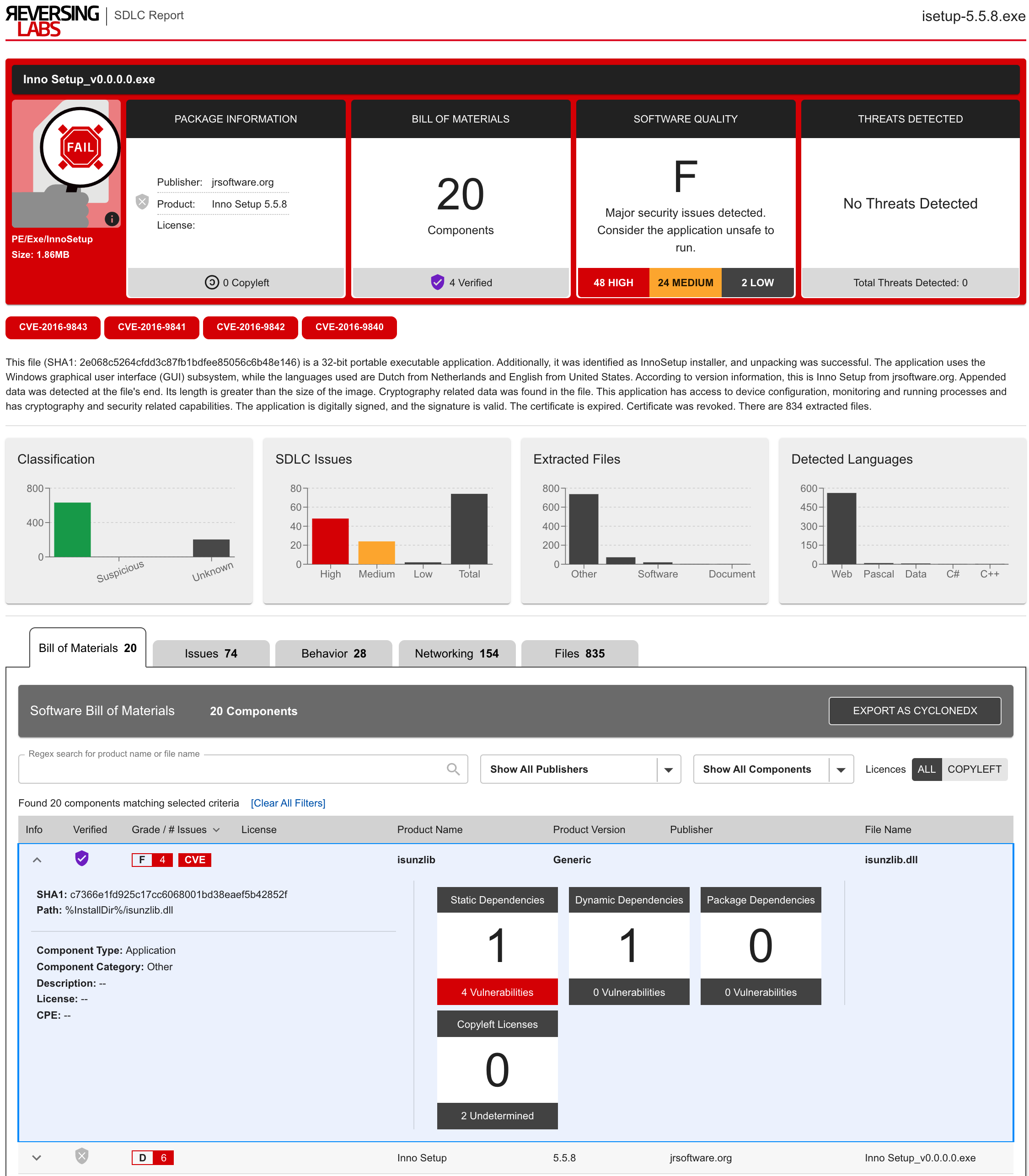
ReversingLabs service makes identifying risks in applications fast and easy. To start, customers simply upload software packages to the Managed Software Assurance Service portal: Secure.Software. ReversingLabs takes the uploaded binary and analyzes every application layer, extracting the embedded components, cataloging them in a software bill of materials, and inspecting each for threats, quality issues, and policy violations. Problems are identified and given a grade representing the software package quality. This grade makes it easy to gauge
How we are different
ReversingLabs Generates a Complete Software Bill of Materials (SBOM): Other available software composition analysis solutions don’t identify the many components within proprietary and open-source software package, which hide preventable security issues and create potential vectors of compromise. The ReversingLabs service inspects every application layer including an in-depth analysis of 400+ file formats commonly used to package software. It then automatically generates a complete SBOM for any in-house developed or third-party software without requiring any vendor assistance.
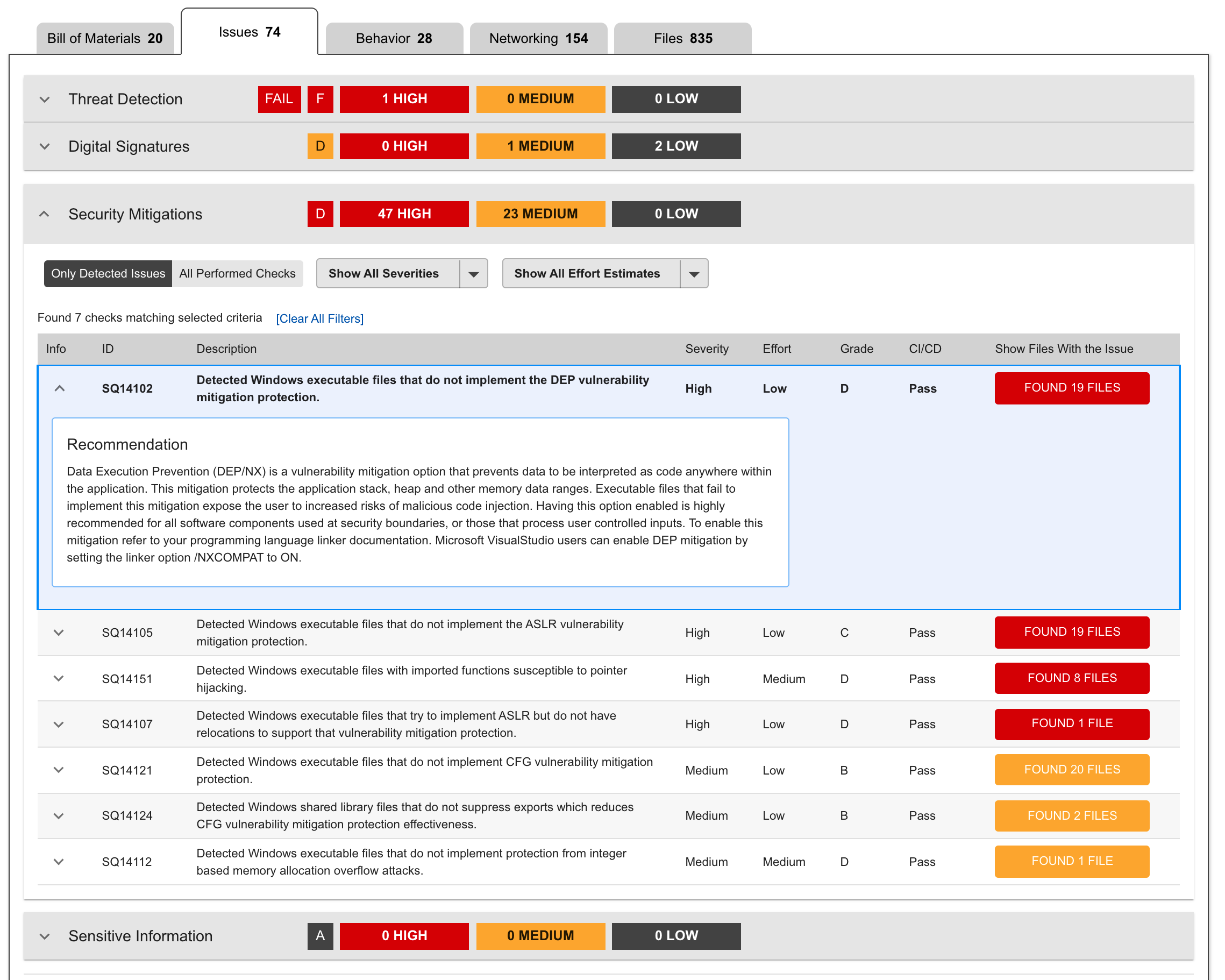
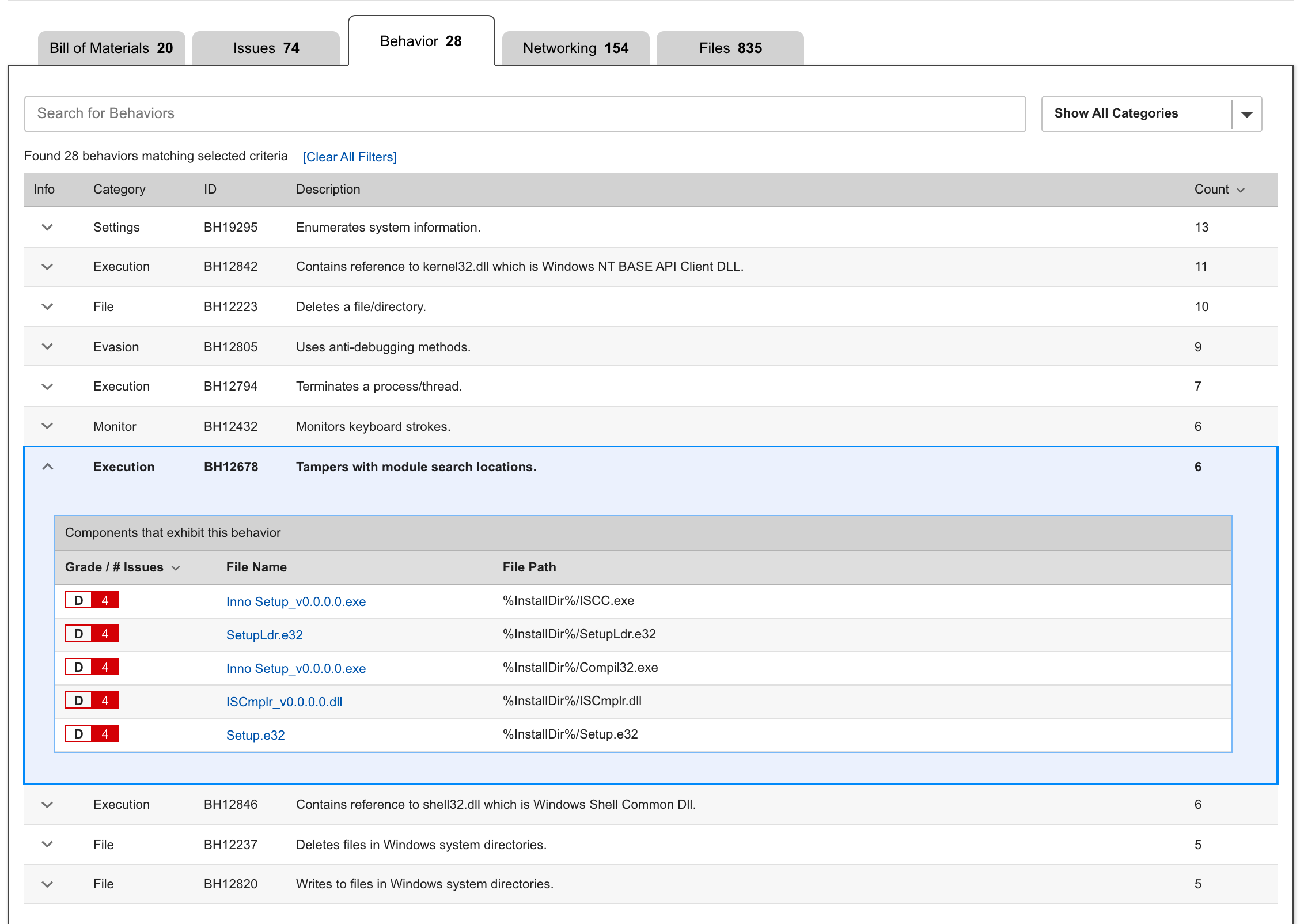
ReversingLabs Audits Behaviors and Checks for Malware: An Enterprise Security Group (ESG) eBook reports that 48 percent of organizations regularly push vulnerable code. That’s because other software assurance solutions fail to thoroughly inspect complex software layers that result in malware detection gaps. ReversingLabs recognizes that build environments are perfect targets for malicious backdoor code injection which is why it checks every application layer for malicious code intent. This prevents the deployment of software releases containing hidden malware or injected backdoor code. It also allows companies to take control of application behaviors and eliminate supply chain attacks through powerful code behavior tracking.
Minimize Vulnerability Risk Surface Area: By one estimate, 60 percent of organizations have had production application vulnerabilities exploited. That is because software build tools don’t reliably enforce vulnerability mitigations across the release package, allowing easy-to-exploit flaws to make it into production code. ReversingLabs’ service audits every application component for known and actively exploited vulnerabilities, keeping software components up-to-date and fortifying existing code to make even undiscovered vulnerabilities harder to exploit.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



