Photo Gallery

|

|
Sangfor Cyber Command

Additional Info
| Company | Sangfor Technologies |
| Company size | 5,000 - 9,999 employees |
| World Region | Asia |
| Website | https://www.sangfor.com/ |
NOMINATION HIGHLIGHTS
Sangfor Cyber Command is a best-in-class Network Detection and Response (NDR) solution that offers organizations unprecedented visibility into their network environment, encompassing hidden threats, attacks in progress, assets including shadow IT, vulnerabilities, and risks. Harnessing the power of artificial intelligence and machine learning technology, Cyber Command offers a comprehensive solution for detecting and responding to sophisticated security incidents, complete with advanced security analytics and real-time threat intelligence. This enables businesses to take decisive action against potential attacks before they escalate into costly breaches.
With its real-time monitoring, analysis, and alerting capabilities, Cyber Command can detect anomalies in network traffic as soon as they occur, empowering organizations to be proactive about their cybersecurity instead of relying on reactive measures. With Sangfor Cyber Command, organizations can transform from passive bystanders to active participants in the battle against cyber threats. Equipped with this advanced security solution, they can effectively stay ahead of increasingly sophisticated cyber threats of both today and tomorrow.
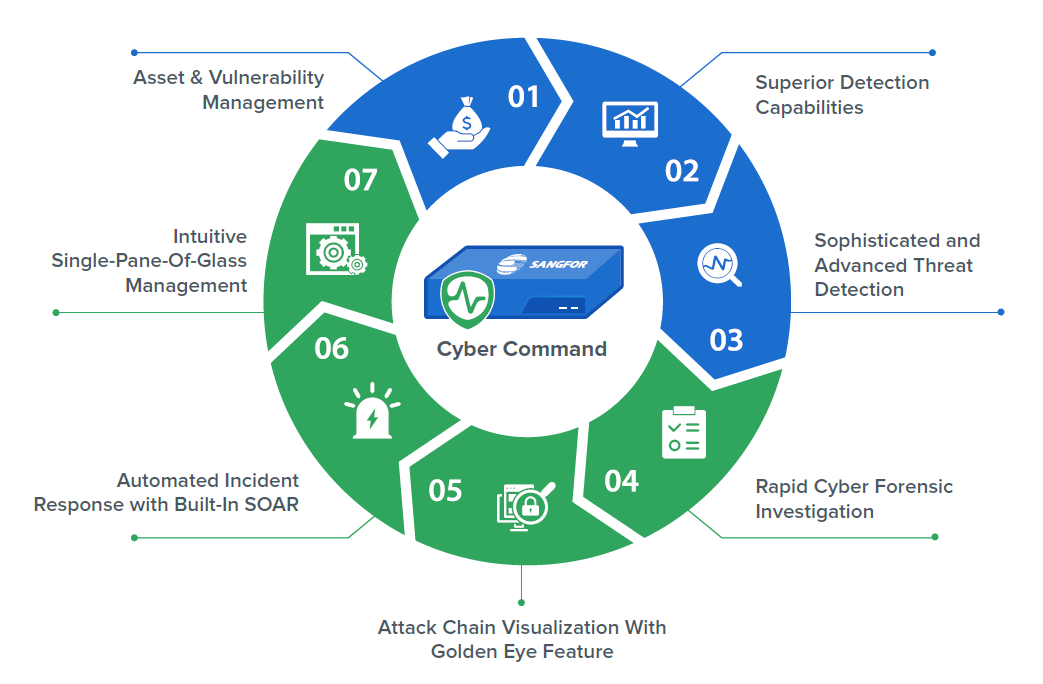
Key Capabilities / Features
1. Asset & Vulnerability Management
Cyber Command automatically discovers and inventories all assets in the environment, including previously unknown shadow IT assets that pose a risk to the network environment. Cyber Command also detects a range of vulnerabilities, such as uninstalled system patches, weak passwords, misconfigurations, and unencrypted traffic, empowering security teams to take prompt remedial measures before they can be exploited by threat actors.
2. Superior Detection Capabilities
Cyber Command offers unparalleled real-time detection by utilizing AI and ML algorithms, as well as the extensive MITRE ATT&CK mapping framework, which details tactics, techniques, and procedures used by adversaries. This framework enables a granular understanding of threat patterns and attack vectors. In conjunction with UEBA technology, Cyber Command monitors user and entity behavior, establishing baselines and employing machine learning for real-time anomaly detection.
3. Sophisticated and Advanced Threat Detection
Cyber Command excels at detecting advanced and sophisticated threats, including ransomware and crypto mining, by utilizing state-of-the-art AI and machine learning methodologies. These advanced algorithms persistently scrutinize network traffic, system conduct, and user interactions to recognize potential threats with real-time precision. To identify and mitigate threats effectively, Cyber Command employs a multifaceted approach that includes behavioral analysis, signature-based detection, and dynamic sandbox analysis.
4. Rapid Cyber Forensic Investigation
Elevate response efficacy with security automation by merging similar security logs into a unified event, highlighting affected assets, and conducting comprehensive forensic analysis. This methodology involves the collection of indicators of compromise (IOCs) and behavioral indicators of compromise (BIOCs) and ensuring post-incident assessment. Efficiently investigate and authenticate an extensive range of IOCs and BIOCs, which can be seamlessly downloaded and exported as needed, all from our innovative Cyber Command platform.
How we are different
1. Superior Threat Detection and Analysis
Cyber Command leverages advanced AI algorithms and machine learning techniques to
continuously learn and adapt to your threat landscape, enabling you to accurately identify and analyze a wide range of threats like ransomware, zero-day attacks, APTs, and crypto mining. Cyber Command is equipped with Sangfor’s Neural-X threat intelligence and analytics platform, which ensures that it is continuously enriched with real-time threat intelligence, patterns, and behaviors from extensive sources to remain effective against advanced and emerging threats. Cyber Command integrates UEBA technology to quickly identify any irregularities or network anomalies and detect anomalous behavior patterns from both users and network entities such as devices, applications, and services at no additional cost. Cyber Command provides a comprehensive mapping of its detection and response capabilities to the MITRE ATT&CK framework, providing organizations with extensive coverage of adversary techniques across all stages of the attack lifecycle, from initial reconnaissance to data exfiltration.
2. More In-Depth Threat Hunting and Forensic Investigation
Cyber Command offers a built-in threat-hunting model, includeing Business Impact Analysis (BIA) that helps you understand asset prioritization and the business impact should assets be compromised. It leverages Sangfor’s unique “Golden Eye” feature, designed to empower security teams with the ability to delve into the entire attack lifecycle with ease.
3. Truly Automated and Integrated Incident Response
Cyber Command’s SOAR module comes with incident response playbooks tailored for some common threat scenarios. To give you greater flexibility and control over your incident response strategies, our playbooks can be easily customized by security teams to align with your organization’s unique requirements and policies, and we enable you to clone or copy our built-in templates and execute them in your existing security tools.


