Photo Gallery

|

|
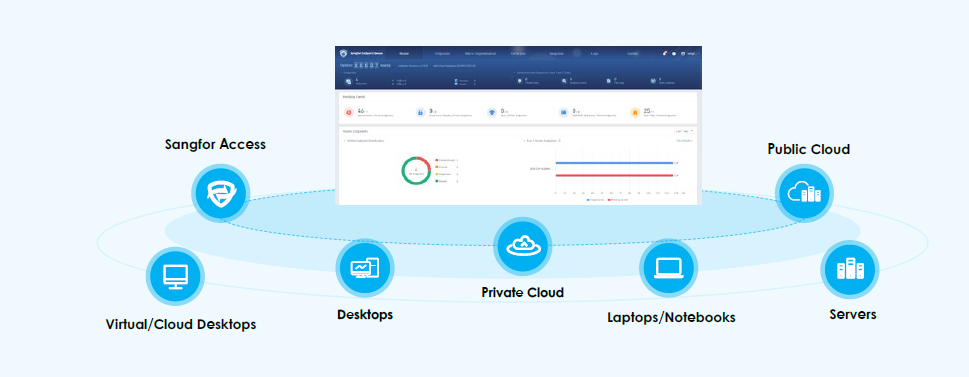
Sangfor Endpoint Secure


Additional Info
| Company | Sangfor Technologies |
| Company size | 5,000 - 9,999 employees |
| Website | http://www.sangfor.com |
NOMINATION HIGHLIGHTS
Sangfor Endpoint Secure is a different approach to defending systems from malware and advanced persistent threats (APTs). Endpoint Secure is part of Sangfor’s XDDR security framework, a truly integrated security solution, providing a holistic response to malware infections and APT breaches across the entire organization’s network, with ease of management, operation, and maintenance.
Endpoint Secure is a different approach to protecting endpoints. Even with Sangfor Engine Zero anti-malware analysis engines’ extremely high detection success rate, it is still not 100% effective. No solution is. Thus, we consider anti-malware to be a “best effort.” Effective security is being prepared for “when” something gets through, and not “if” it gets through.
How we are different
1. Simpler, smarter monitoring
• Scheduled or on-demand vulnerability scanning (scan can be initiated by NGAF)
• Vulnerability Scan results provide informative patch recommendations, including global threat correlation
• Compliance monitoring compares endpoint security configuration with organizational security policies
• Enterprise asset tracking
• Cloud malware sandbox for dynamic analysis
• Endpoint Secure Protect Agent Ransomware Honeypot capability
2. Simpler, smarter response to threats
• Real-time Threat Intelligence from cloud-based Neural-X recognizes new malware signatures discovered by Sangfor TI sources
• One-Click/Automatic Host Micro-Isolation disconnects multiple endpoints from the network, containing the spread of malware
• One-Click/Automatic File Disposal deletes or quarantines malware from multiple endpoints
• Network-Wide Threat Disposal allows the administrator to respond quickly to a large malware outbreak
• NGAF integration can prevent malware from communicating with Command & Control servers and propagation across the enterprise
3. All it takes is one breach.
Endpoint Secure concentrates on response, ready to contain and mitigate that one breach WHEN it happens.


