SberBank Intelligent Cyber Threats Management System
Recognized in the Category:
Photo Gallery
 |
 |
SberBank Intelligent Cyber Threats Management System

Additional Info
| Company | SBER |
| Company size | 10,000 or more employees |
| Website | https://www.sberbank.com/index |
NOMINATION HIGHLIGHTS
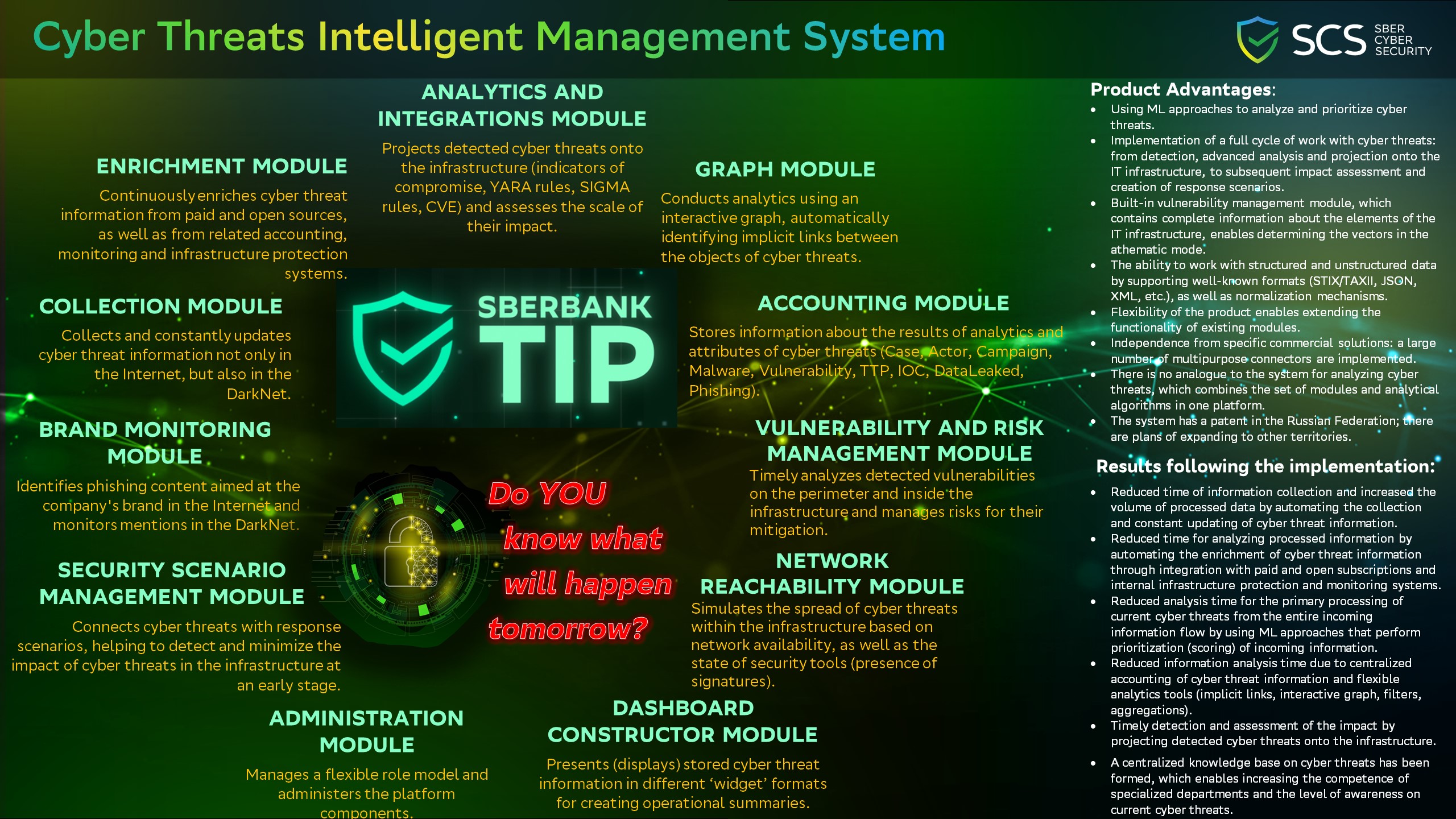
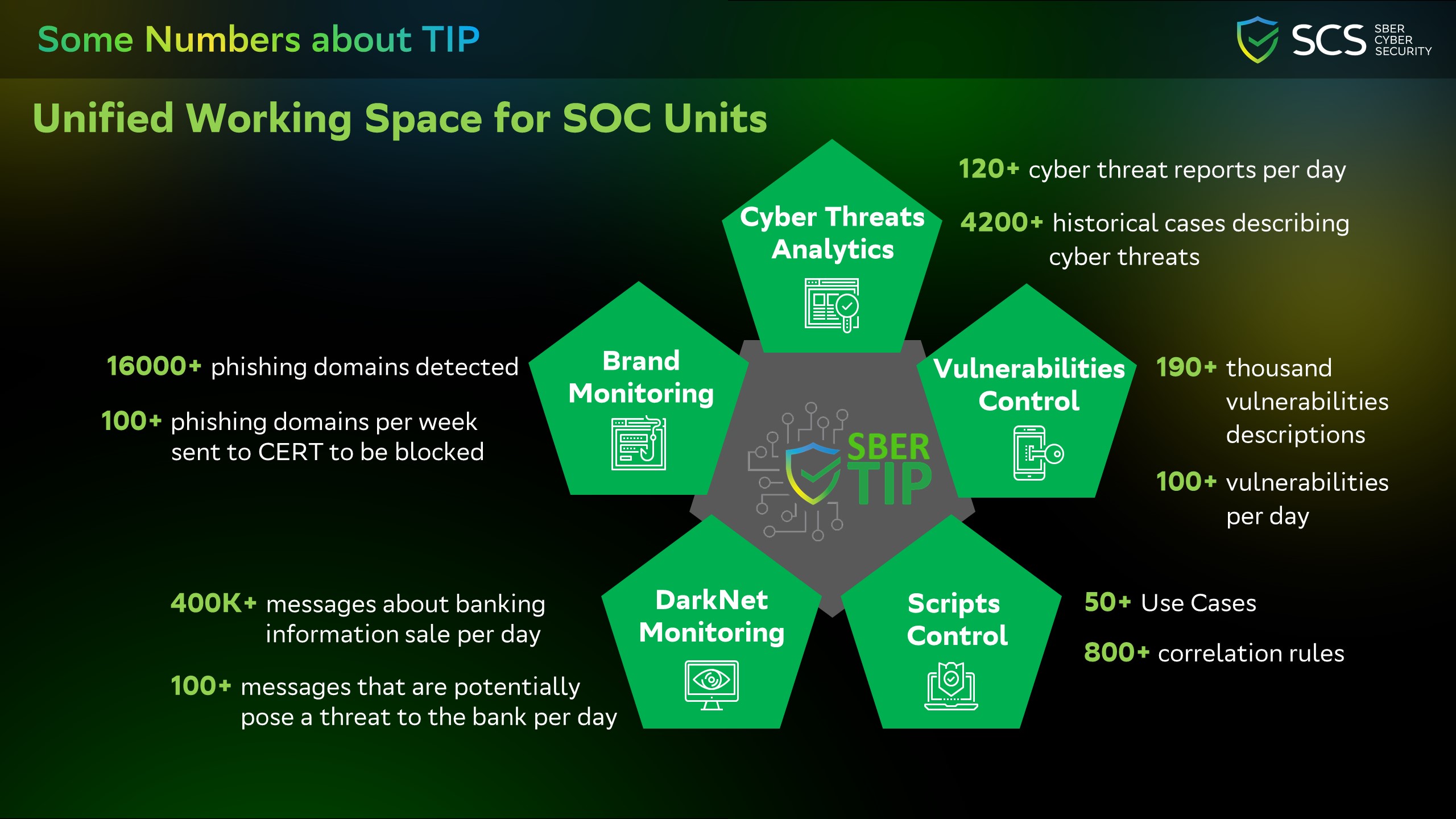
Intelligent cyber threats management system was launched in 2019. It is aimed at automating the collection, constant updating and prioritization of cyber threat information.
Thanks to the flexible mechanisms of data collection and algorithms of data transformation (normalization), it works with both structured and unstructured data.
Existing integrations with paid and open sources (subscriptions) continuously enrich it with additional information.
Multiple integrations with internal infrastructure monitoring and security systems enable projecting detected cyber threats onto the infrastructure and simulate their propagation paths.
Use of analytical modules prioritizes the processing of incoming data, as well as reveals implicit links between the attributes of cyber threats.
Application of automation tools reduces the time for collecting information and increases its volume, while reducing the time for complete analysis.
All these features allow to identify and analyze cyber threats in a timely manner, with the subsequent creation of detection scenarios and risk minimization.
Product Advantages:
1. Using ML approaches to analyze and prioritize cyber threats.
2. Implementation of a full cycle of work with cyber threats: from detection, advanced analysis and projection onto the IT infrastructure, to subsequent impact assessment and creation of response scenarios.
3. Built-in vulnerability management module, which contains complete information about the elements of the IT infrastructure, enables determining the vectors in the athematic mode.
4. The ability to work with structured and unstructured data by supporting well-known formats (STIX/TAXII, JSON, XML, etc.), as well as normalization mechanisms.
5. Flexibility of the product enables extending the functionality of existing modules.
6. Independence from specific commercial solutions: a large number of multipurpose connectors are implemented.
7. This system has no analogue on the market because it combines the set of modules and analytical algorithms in one platform.
8. The system has a patent in the Russian Federation; there are plans of expanding to other countries.
More information you can see in our short video: https://drive.google.com/file/d/1QXewbpXT_9i2Hitjwa7Ehis-bcDtAeDL/view?usp=sharing
How we are different
• Cyber threats are identified and analyzed in a timely manner by this system.
• The system doesn’t just collect information on cyber threats, but comprehensively manages the full cycle: from detection, analysis and prioritization to creation of detection / mitigation scenarios.
• The system is a single platform that includes many modules, which is a unique technology.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



