Cyberbit SCADAShield Mobile – portable ICS/SCADA network assessment system
Nominated in the Category:
Photo Gallery
 |

 |
Cyberbit SCADAShield Mobile - portable ICS/SCADA network assessment system


Additional Info
| Company | Cyberbit |
| Company size | 100 - 499 employees |
| Website | https://www.cyberbit.com/solutions/ics-scada-security-continuity/ |
NOMINATION HIGHLIGHTS
Cyberthreats now endanger the operational technology (OT) networks that are the backbone of critical infrastructure and manufacturing industries. Breaches on these networks have already caused massive power outages affecting millions of homes and businesses and dangerous factory explosions that endangered human life and caused disruption and monetary loss. Securing them requires overcoming a new set of challenges that are yet uncharted in the IT-only world. As a result, OT network managers today face a formidable cyber threat, but lack the tools and knowhow to do so effectively.
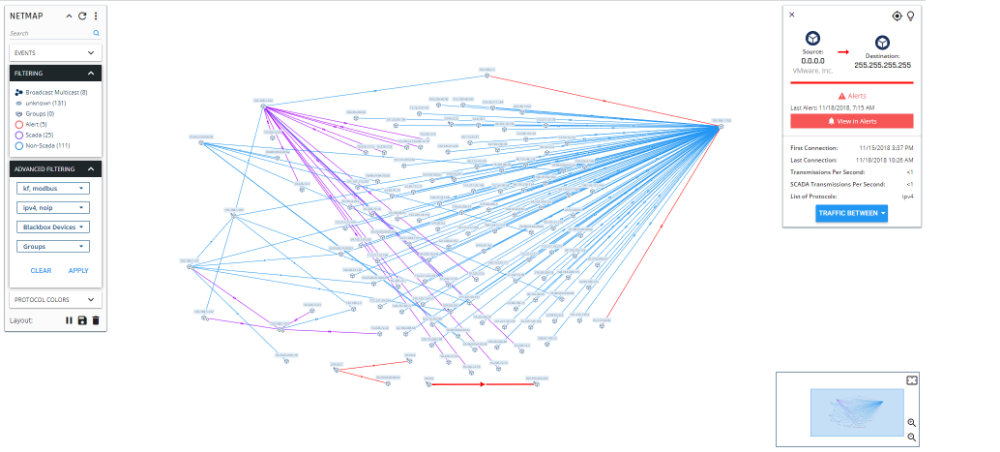
Cyberbit developed SCADAScan to jump start the process of updating and hardening cybersecurity of ICS networks. SCADAScan is the first and only completely mobile ICS security assessments solution that eliminates arduous setup efforts and can be completed in just hours or days. The device plugs into a network switch, and within minutes of passive monitoring Deep packet inspection (DPI) is used to monitor traffic passing through the ICS/SCADA network and provide a complete and detailed map of all assets, and information on vulnerabilities and other potential threats. The solution is especially suited to critical infrastructure organizations that can benefit greatly from periodical scanning and assessment but are not willing to permanently integrate a full-scale monitoring solution.
SCADAScan is contained in a water resistant wheeled suitcase, that weighs just 15 kg (XX lbs) and can be taken on commercial aircraft as a carry-on. The device is powered by Cyberbit SCADAShield technology, which provides monitoring, detection, forensics, visibility, and policy enforcement capabilities for ICS networks. The new product can also be integrated with the company’s Security Orchestration, Automation and Response (SOAR) solution.
How we are different
• Significantly improves security of high-risk critical ICS networks
• “Plug-and-play’ security assessment requires less time, money and integration effort
• Highly accessible, mobile

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



