Cyberbit SCADAShield – OT Security, Visibility and Continuity for ICS/SCADA Networks
Nominated in the Category:
Photo Gallery
 |
 |
Cyberbit SCADAShield - OT Security, Visibility and Continuity for ICS/SCADA Networks

Additional Info
| Company | Cyberbit |
| Company size | 100 - 499 employees |
| Website | https://www.cyberbit.com/solutions/ics-scada-security-continuity/ |
NOMINATION HIGHLIGHTS
As ICSSCADA networks grow increasingly connected and complex, they are at constant risk of downtime due to operational failures and malicious activity, but lack the necessary monitoring and analysis tools. Malformed packets, unauthorized devices and activities, changes in network volumes and anomalous commands can cause harm and disruption. To achieve continuous operations, derived from secured and trusted networks, visibility and anomaly detection must be applied.
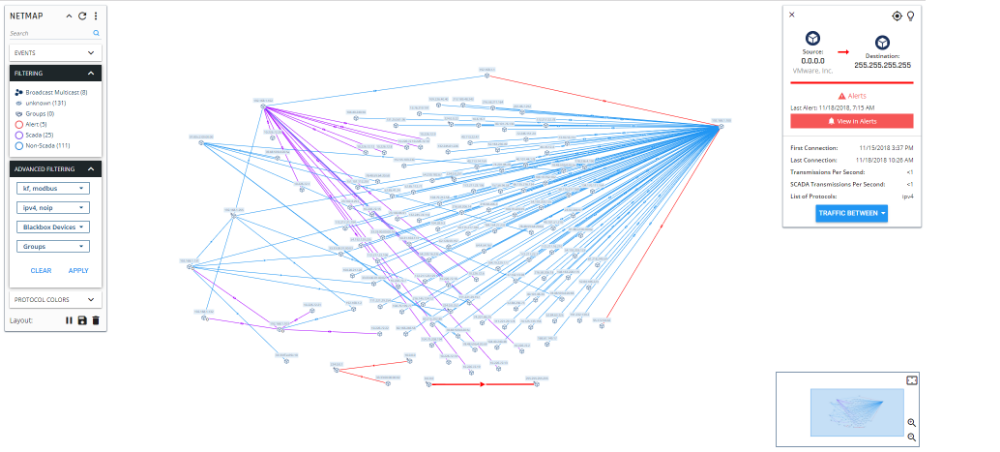
SCADAShield uses Granular Deep Packet Inspection (GDPI) to thoroughly analyze packets and detect OT, IT/OT and IT attack vectors. Traffic analysis is also used to build a real-world network map and for asset management. SCADAShield uses mirror port for passive and non-intrusive monitoring.
VISIBILITY – SCADAShield provides full visibility of the OT network by automatically generating a live real-world network map based on traffic analysis. The network map presents all IP and non-IP network assets and their communication paths and protocols, allowing network managers and analysts to quickly identify IT/OT touchpoints, initiate investigations and analyze alerts.
DETECTION – SCADAShield automatically baselines the customer’s network and alerts on anomalous security and operational behaviors. It alerts on malfunctions and misconfigurations, and helps enforce operational policies and regulation. The engine provides clear guidelines for remediation and response, allowing network managers and analysts to achieve remediation in a timely manner.
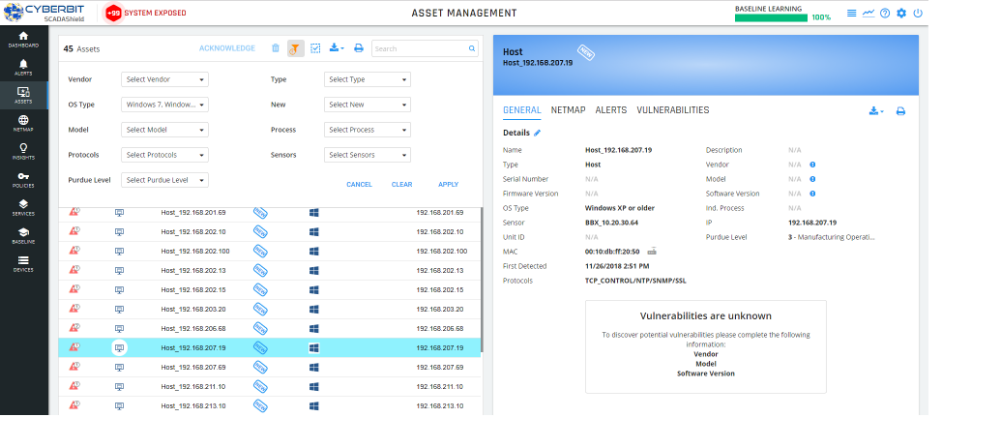
ASSET and LAYER MANAGEMENT – SCADAShield automatically maps and identifies all OT and IT assets and their types, presenting them in Purdue Model for OT layer management. It graphically shows the operational and organizational layers, identifying device types, vendors, model, serial number, operating systems, firmware and software versions, vulnerabilities, MAC address, IP, last seen, last configuration change, and more.
How we are different
• Network visibility and management of all OT and IT assets
• Detect and mitigate known vulnerabilities in OT and IT networks
• Detect and respond to unknown ICS threats

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



