Photo Gallery

|


|
SentinelOne Singularity XDR Platform

Additional Info
| Company | SentinelOne |
| Company size | 500 - 999 employees |
| Website | http://www.sentinelone.com |
NOMINATION HIGHLIGHTS
The proliferation of connected endpoint, cloud, and IoT devices creates billions of targets for hackers to penetrate enterprise networks. Visibility and protection of the new perimeter – the endpoint – has never been more critical.
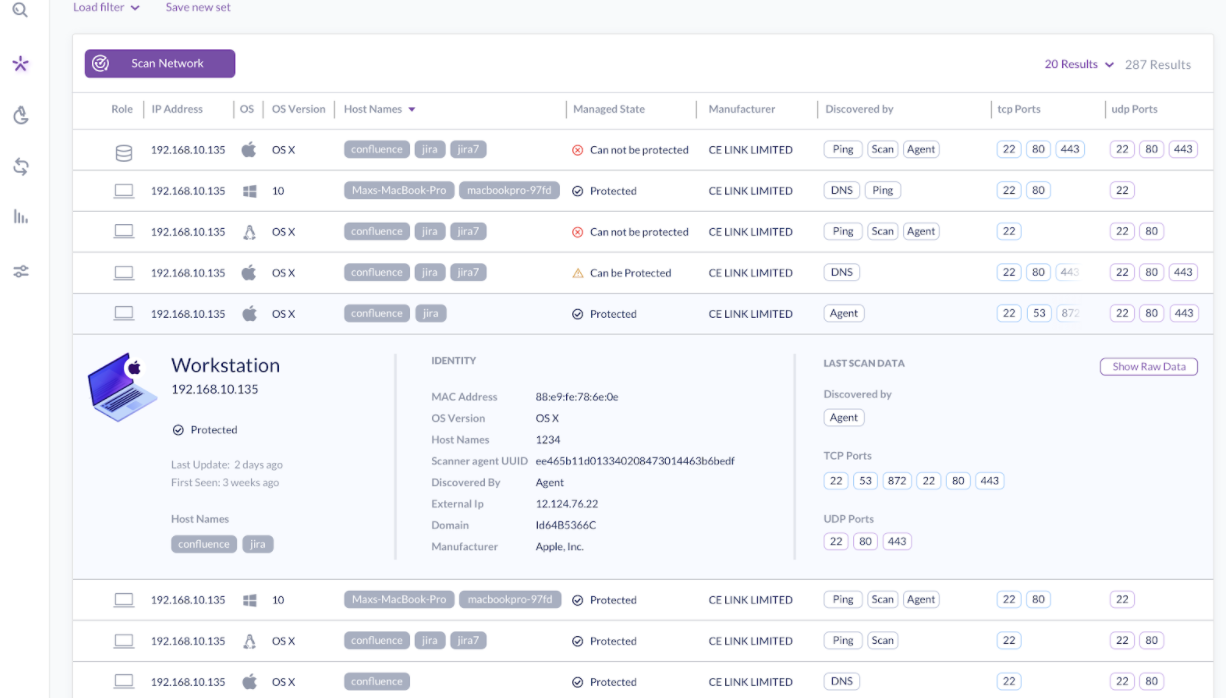
SentinelOne Singularity protects and monitors every endpoint in the enterprise — seamlessly unifying endpoint protection (EPP), endpoint detection and response (EDR), IoT control and cloud workload protection into its Singularity platform for an unprecedented XDR autonomous protection with the lowest performance impact — delivered by the company’s patented behavioral and static AI models.
The technology can not only fingerprint and profile the devices that SentinelOne’s software (agent) discovers by enabling complete environment visibility, but also it can identify an enterprise’s weakest links and minimize risk over time. It is the industry’s first solution that allows machines to autonomously protect, segment, and notify security teams of vulnerabilities, rogue devices, and anomalous behaviors.
The result? Actions and data that once required stacks of hardware as well as trained and tenured SOC analysts is now solved with applied AI. Visibility over a whole class of devices that wasn’t available to the enterprise is now crystal clear. Control of the IoT domain was impossible; now it’s simply within a few clicks. Deploying these capabilities in the form of a lightweight software package that resides on laptops, desktops, servers, and cloud workloads, allows businesses to leverage capabilities that were once available only to the world’s most advanced and largest enterprises. And in large enterprise environments, analysts are now able to focus on investigation and response to mission-critical attacks instead of wasting time researching and linking individual events.
SentinelOne Singularity helps protect the world’s largest and critical businesses from falling victim to the next big cyberattack, regardless of the stage of the threat lifecycle with AI-powered technology (humans optional).
How we are different
AI to Scale Cybersecurity: SentinelOne has zero reliance on humans, services, or even cloud connectivity to deploy and operate the solution. The company is the only cybersecurity platform powered by AI that provides advanced threat hunting and complete visibility across every device, virtual or physical, on prem or in the cloud. Competitive products require human-powered services or rely on reactive database methods which constantly require updates.
Consolidate and Escape Outdated Technology: With Singularity, SentinelOne liberates enterprises and government agencies from ineffective, difficult to manage products which are helpless against modern-day cyber attacks. SentinelOne is a single agent - single console cloud based technology. Typical enterprises have 5+ software agents on their devices. These legacy software technologies slow down the device, frustrate the user, aren’t built for a WFH world, and aren’t able to keep up with modern-day cyber attacks. SentinelOne consolidates. Enterprises can secure WFH computers and ensure that all surrounding IoT devices are prohibited from communication with enterprise assets. Competitive solutions add additional agents versus solve the underlying needs of agent consolidation; for example, other vendors require an agent for EPP and another agent for EDR.
Built for the cloud, in the cloud, to secure the cloud. Digital transformation has more and more data moving from on-prem datacenters to cloud hosted venues, whether that be public clouds, private clouds, or hybrid constructs. Today’s enterprise uses cloud applications such as Slack, G Suite, O365, and Zoom. In addition, modern software development practices leverage containerized workload architectures such as Kubernetes. SentinelOne’s Singularity platform secures each of these attack surfaces and provides cybersecurity teams an easy console to manage the diverse attack surfaces of today’s enterprise. Competitive solutions are limited in Linux distributions, lack cloud workload protection capabilities, and aren't built to protected containerized workloads.


