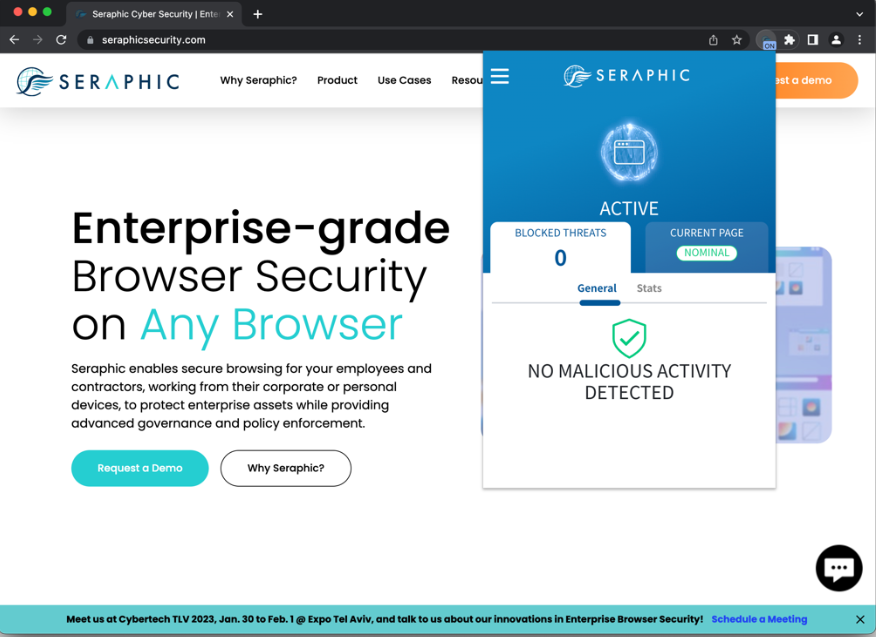
Seraphic Security, Enterprise Browser Security on Any Browser
Recognized in the Category:
Photo Gallery

|
|
Seraphic Security, Enterprise Browser Security on Any Browser

Additional Info
| Company | Seraphic Security |
| Company size | 10 - 49 employees |
| World Region | North America |
| Website | https://seraphicsecurity.com/ |
NOMINATION HIGHLIGHTS
Seraphic Security takes a completely novel approach to isolation. Rather than separating the user from the browser, its patented Chaotic Defense Engine (CDE) separates the code in web pages from the browser’s native rendering and execution components. The CDE presents an unpredictable variant of the browser execution environment and, because successful exploitation requires prior knowledge of what will happen when a vulnerability is triggered, the unpredictability effectively “breaks” exploits. The practical effects of this innovation on browser exploitation are very similar to the effect of Address Space Layout Randomization (ASLR) on memory corruption bugs: benign code is unaffected and operates normally, while malicious code fails to execute. As result, Seraphic Security can prevent 0-day and unpatched N-day exploits without the need for signatures, threat intelligence feeds, or ML/ AI.
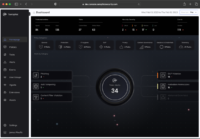
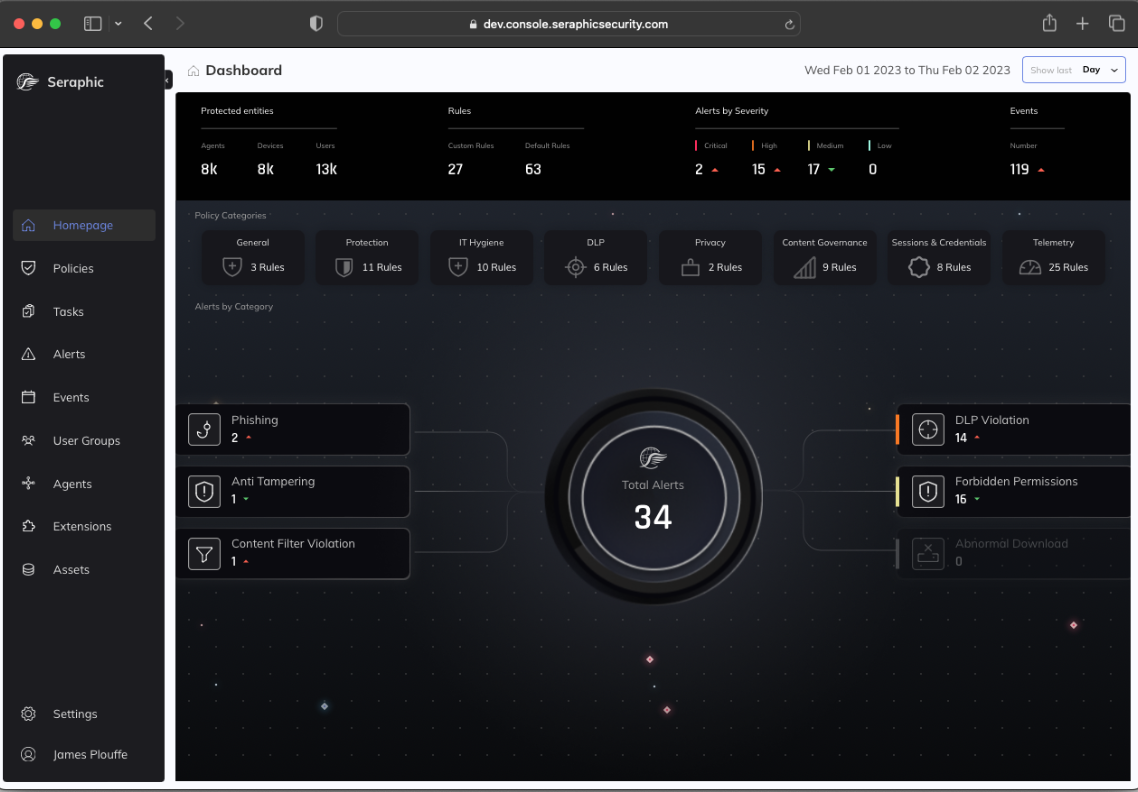
The protection doesn’t stop at exploitation, however. Because Seraphic Security operates at the heart of the browser, it has full visibility into all browser activity giving organizations a vital mechanism for governance and policy enforcement. These capabilities enable fine-grained control over activity ranging from content filtering to copy/ paste/ print/ screen capture to file upload/ download. It also has the ability to identify and mask sensitive data in both rendered and downloaded content. These controls prevent data loss resulting from user actions within the browser, a vector traditional isolation solutions don’t cover.
Seraphic Security is, therefore, ideally suited to addressing the two core problems browser isolation aims to solve: protecting users and endpoints from compromise via the Internet, and preventing the leakage or loss of sensitive data via the browser. But perhaps the most compelling characteristic of the solution is that it delivers these capabilities to any browser on both managed and unmanaged endpoints without the cost, complexity, latency, and rendering issues that have plagued other browser isolation
How we are different
Seraphic Security is unique in its ability to prevent 0-day, unpatched N-day, and other web-based attacks (such as cross-site scripting/ XSS, HTML smuggling, and UI redressing). Other isolation approaches attempt to limit the “blast radius” of exploits but don’t prevent them and they are completely unable to stop other attacks. In customer deployments, Seraphic Security blocks attacks that bypass other security tools at an average rate of 2 – 3 per month.
Seraphic Security does not impose undue costs on end users or IT teams. Because it operates directly in existing browsers, issues like network latency that plague “pixel pushing” isolation solutions or page rendering/ web app compatibility problems that result from Document Object Model (DOM) reconstruction do not affect Seraphic. The installation and operation of Seraphic Security is entirely transparent to end users and provides security without the need to make any changes to their normal workflow: they can continue to use their favorite browser. The experience is so fluid that users frequently ask to switch from other solutions to Seraphic Security before the Proof-of-Concept (PoC) is finished. Seraphic Security also does not require procurement and ongoing maintenance of server farms dedicated to running virtual browsers, reducing CAPEX, OPEX, and IT labor.
Seraphic Security scales from deployments of tens of users to tens of thousands. It puts a new level of security in the hands of both small and large enterprises, protecting them from increasingly costly breaches that may jeopardize the long-term viability of the business. Organizations can meaningfully improve their security posture without a corresponding increase in complexity or drag on productivity.


