Photo Gallery
 |
 |
SpyCloud Account Takeover Prevention


Additional Info
| Company | SpyCloud |
| Company size | 50 - 99 employees |
| Website | http://www.spycloud.com |
NOMINATION HIGHLIGHTS
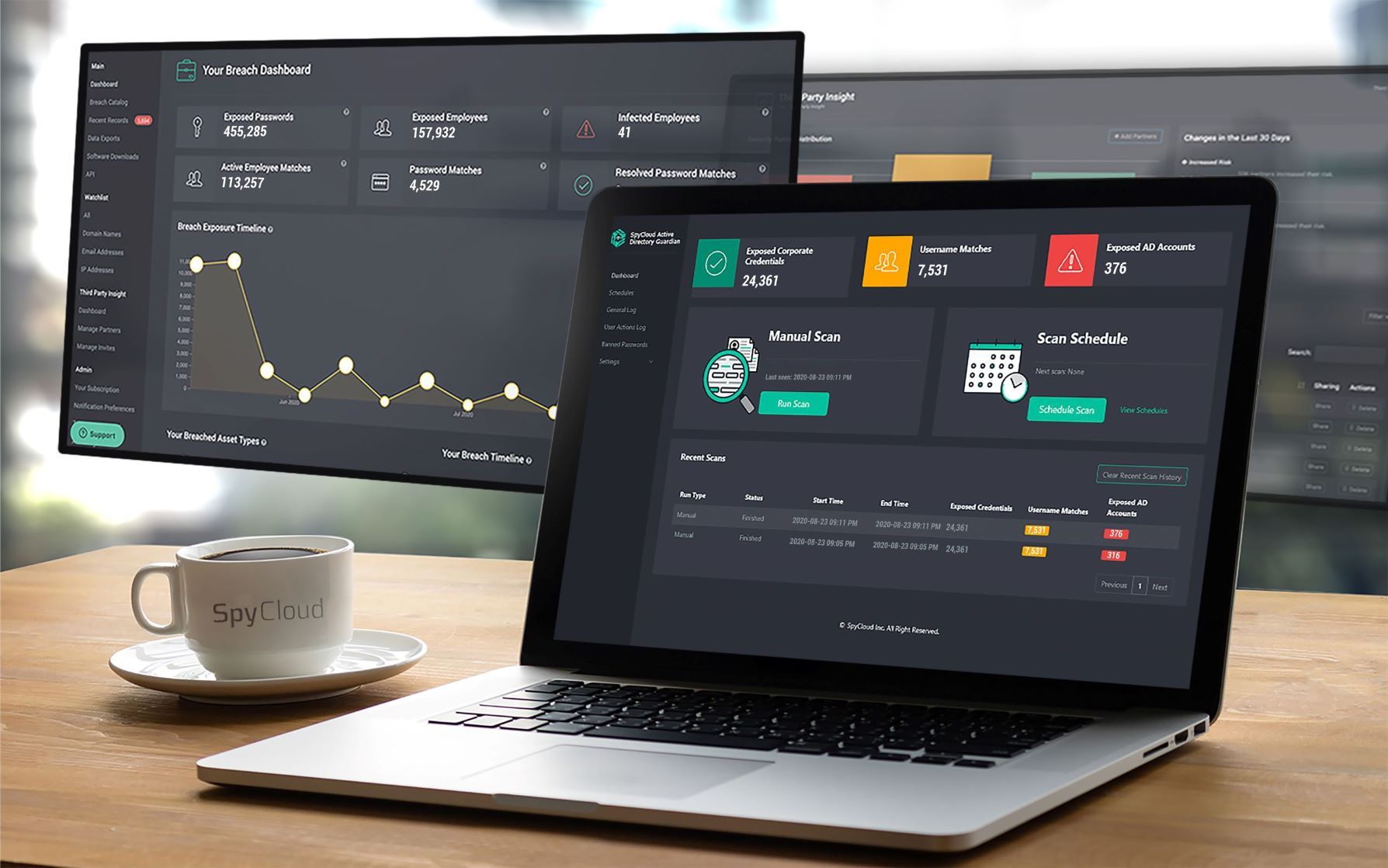
Account takeovers resulting from weak or stolen credentials have become one of the most common paths to online fraud, increasing in frequency at a rate of 72% year over year. As a result, SpyCloud keeps evolving its comprehensive account takeover and online fraud prevention platform to keep pace with the growth in attacks. Preventing fraud requires high confidence in customer identities, and the ability to flag accounts that are using compromised passwords. SpyCloud’s platform is backed by an ever-growing database of more than 113 billion breach assets recovered from the criminal underground – the most comprehensive breach database in the world including 20 billion plaintext passwords – against which customer identity attributes are compared. When exact-match stolen information is detected, the account is flagged for password reset or a step-up authentication process such as MFA, as defined by the company’s risk tolerance. It proactively helps companies identify potentially fraudulent activity while reducing friction and false positives.
Companies using SpyCloud treat account protection as part of the overall customer experience, which allows for seamless transactions and customer satisfaction while also preventing fraud. SpyCloud helps companies prevent account takeover, monitoring accounts for exposed Personally Identifiable Information (PII), passwords, phone numbers, and more. It stops fraud from fabricated identities by spotting user information disparities using its vast breach database, which contains data on not only legitimate users, but also criminal identities. But ultimately, it is designed to prevent fraud in a seamless, frictionless way. Friction can be avoided with periodic offline batch processing to securely identify at-risk accounts using exposed passwords. This is a common method used by SpyCloud clients to reduce friction by proactively identifying high-risk password reuse.
How we are different
Earliest possible remediation: Where other threat intelligence companies scan the dark web waiting for stolen data to appear, SpyCloud uses human intelligence and works undercover in the cybercriminal underground to proactively obtain email addresses, passwords and other PII straight from criminals immediately after a breach. This unique collection method means SpyCloud recovers stolen data much sooner than other threat intelligence providers (often 18+ months ahead). It shortens the exposure window substantially, enabling fraud prevention teams to Intervene early to lock bad actors out of vulnerable accounts.
Unique data: SpyCloud identifies users infected with credential-stealing botnets. Part of its data collection efforts recover bot logs from keylogger malware infections. This data represents active malware infections on consumers’ machines. Companies using SpyCloud have found this data to be incredibly valuable in securing consumer accounts. One crypto exchange noted: “With SpyCloud’s botnet data, we’ve protected thousands of accounts representing tens of millions of dollars of funds. They are users we found in SpyCloud’s botnet data, where we were able to successfully intervene and force password resets and account recoveries before an attacker was able to do something malicious with those credentials.”
Most robust breach data collection: As a result of SpyCloud’s unique combination of human intelligence and early data recovery, the company maintains the world’s largest collection of breach data, composed of more than 113 billion breach assets, helping businesses to find more compromises, stay ahead of hard-to-detect attacks, and protect high-value consumer accounts and their bottom line from financial harm.

Vote by Sharing
- Like
- Digg
- Tumblr
- VKontakte
- Buffer
- Love This
- Odnoklassniki
- Meneame
- Blogger
- Amazon
- Yahoo Mail
- Gmail
- AOL
- Newsvine
- HackerNews
- Evernote
- MySpace
- Mail.ru
- Viadeo
- Line
- Comments
- SMS
- Viber
- Telegram
- Subscribe
- Facebook Messenger
- Kakao
- LiveJournal
- Yammer
- Edgar
- Fintel
- Mix
- Instapaper
- Copy Link
Each completed social share counts as a vote for this award nomination.



